Light | THM Writeup
Introduction
Detailed walkthroughs for Light CTF challenges on TryHackMe .
Description
I am working on a database application called Light! Would you like to try it out?
If so, the application is running on port 1337. You can connect to it using nc 10.10.95.233 1337
You can use the username smokey in order to get started.
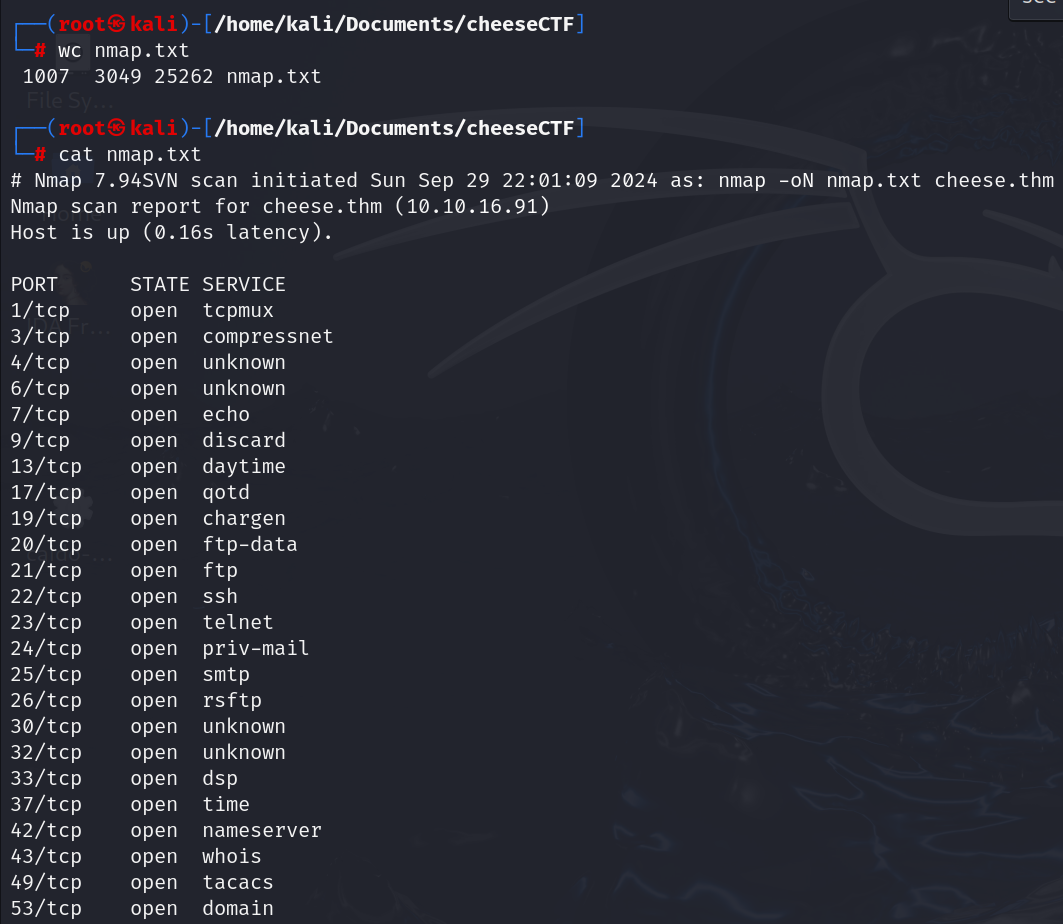
Enumaration
sudo echo 10.10.95.233 light.thm >> /etc/hosts
Mapped the ip to domain light.thm.
NetCat
We receive the password when a valid username is entered.