Block | THM Writeup
Introduction
Detailed walkthroughs for Block CTF challenges on TryHackMe .
Description
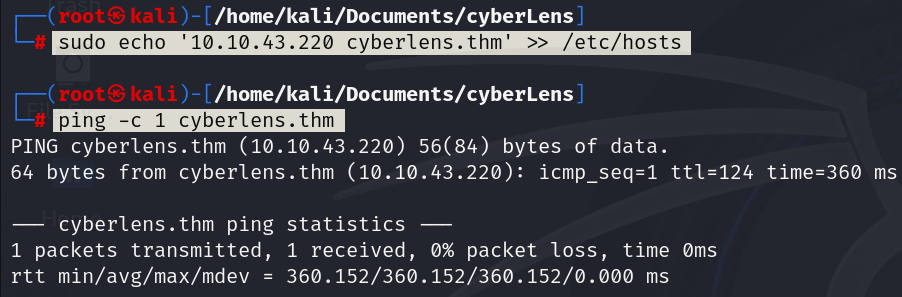
One of your junior system administrators forgot to deactivate two accounts from a pair of recently fired employees. We believe these employees used the credentials they were given in order to access some of the many private files from our server, but we need concrete proof. The junior system administrator only has a small network capture of the incident and a memory dump of the Local Security Authority Subsystem Service process. Fortunately, for your company, that is all you need.
- CTF
- Forensic
- Lssas.DMP
- Pypykatz
- John
- SmbDecryption
- Wireshark
- Mimikatz
- Endianess
- Pyscript
- Tryhackme
- Windows
- Medium