Introduction
Detailed walkthroughs for Block CTF challenges on TryHackMe .
Description
One of your junior system administrators forgot to deactivate two accounts from a pair of recently fired employees. We believe these employees used the credentials they were given in order to access some of the many private files from our server, but we need concrete proof. The junior system administrator only has a small network capture of the incident and a memory dump of the Local Security Authority Subsystem Service process. Fortunately, for your company, that is all you need.
Tools used
Wireshark, pypykatz, mimikatz, john and pythonScript
Evidence
We got 2 files named lsass.DMP and traffic.pcapng when unzipping evidence-1697996360986.zip.
$ file *
lsass.DMP: Mini DuMP crash report, 16 streams, Sun Oct 22 16:54:50 2023, 0x421826 type
traffic.pcapng: pcapng capture file - version 1.0
Lets start with .pcapng file.
.pcapng
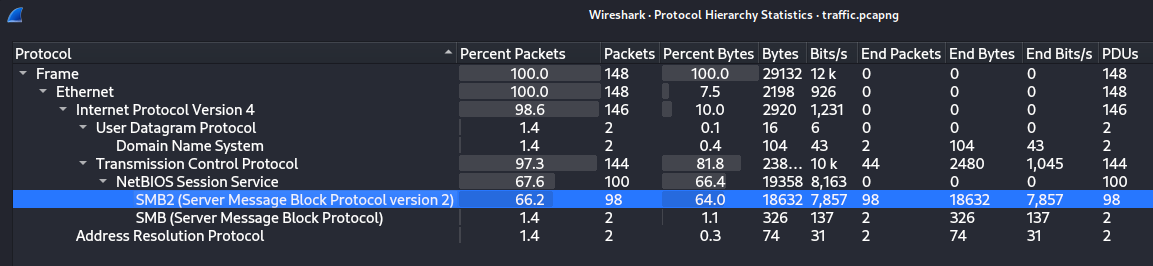
SMB2 packets were captured, which is interesting data.
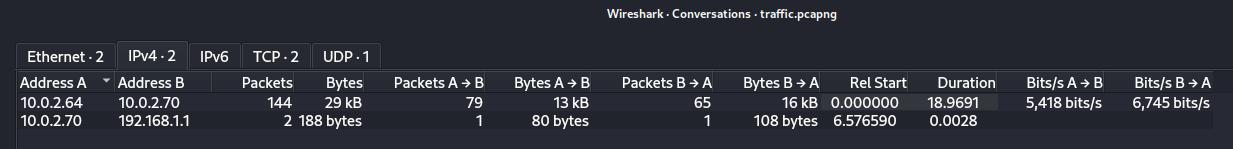
10.0.2.64, 10.0.2.70, 192.168.1.1.
No Time Source Destination Protocal Length Info
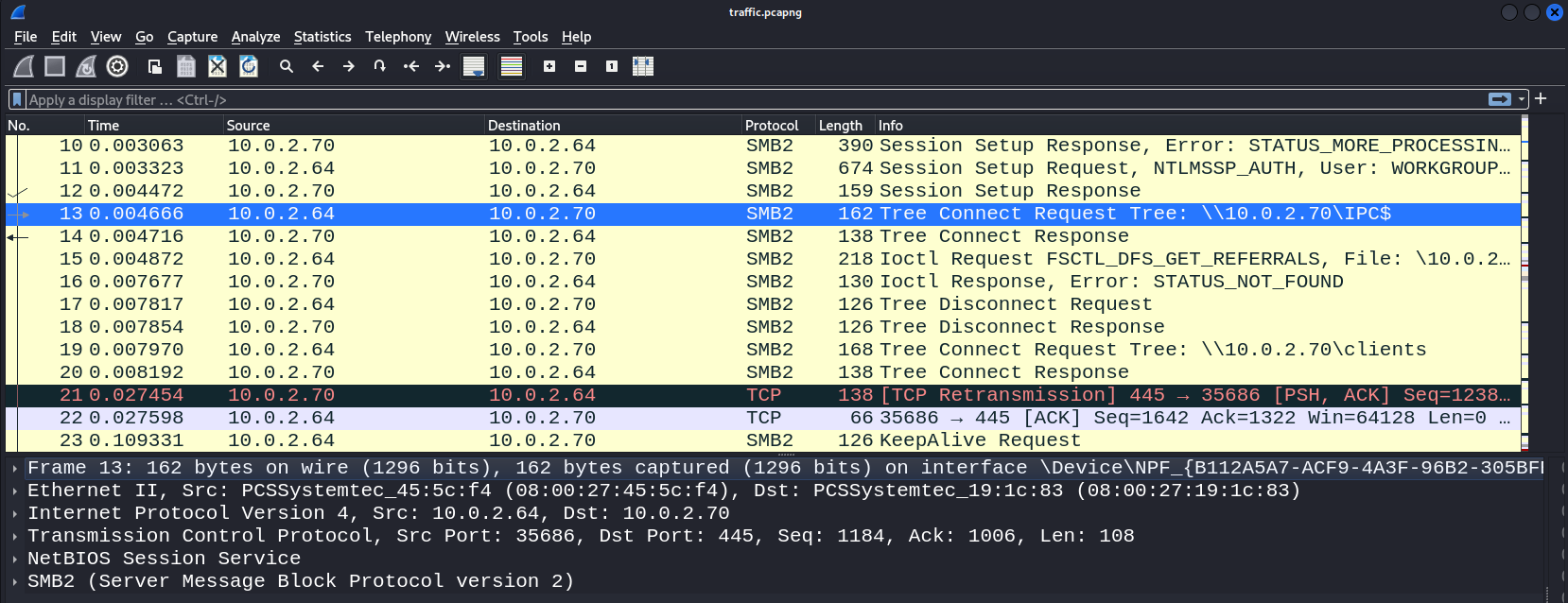
11 0.003323 10.0.2.64 10.0.2.70 SMB2 674 Session Setup Request, NTLMSSP_AUTH, User: WORKGROUP\mrealman
While looking into the .pcapng data using wireshark, we found first user connected to the system.
82 11.716089 10.0.2.64 10.0.2.70 SMB2 680 Session Setup Request, NTLMSSP_AUTH, User: WORKGROUP\eshellstrop
Further reviewing the packets we got the second user as well.
SMB data were encrypted. We need to decrypt to get useful information.
lsass.DMP
Now lets move to analyze the dump file.
Learn about LSASS: B2dfir
pypykatz
pypykatz lsa minidump evidence/lsass.DMP > dump.txt
Used the above command to extract the credentials using pypykatz and saved it in the file dump.txt.
$ pypykatz lsa minidump evidence/lsass.DMP -p msv
INFO:pypykatz:Parsing file evidence/lsass.DMP
FILE: ======== evidence/lsass.DMP =======
== LogonSession ==
authentication_id 1883004 (1cbb7c)
session_id 3
username mrealman
domainname BLOCK
logon_server WIN-2258HHCBNQR
logon_time 2023-10-22T16:53:54.168637+00:00
sid S-1-5-21-3761843758-2185005375-3584081457-1104
luid 1883004
== MSV ==
Username: mrealman
Domain: BLOCK
LM: NA
NT: 1f9175a516211660c7a8143b0f36ab44
SHA1: ccd27b4bf489ffda2251897ef86fdb488f248aef
DPAPI: 3d618a1fffd6c879cd0b056910ec0c31
== LogonSession ==
authentication_id 828825 (ca599)
session_id 2
username eshellstrop
domainname BLOCK
logon_server WIN-2258HHCBNQR
logon_time 2023-10-22T16:46:09.215626+00:00
sid S-1-5-21-3761843758-2185005375-3584081457-1103
luid 828825
== MSV ==
Username: eshellstrop
Domain: BLOCK
LM: NA
NT: 3f29138a04aadc19214e9c04028bf381
SHA1: 91374e6e58d7b523376e3b1eb04ae5440e678717
DPAPI: 87c8e56bc4714d4c5659f254771559a8
The data above has been extracted using pypykatz, and I’ve included only the information that is relevant for our CTF lab. Here we have an interesting data that is NT Hash. Lets try to bruteforce the password using the hash string which we have.
JohnTheRipper
$ echo 1f9175a516211660c7a8143b0f36ab44 > hash.txt
$ john hash.txt -format=NT --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (NT [MD4 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
Blockbuster1 (?)
1g 0:00:00:00 DONE (2024-09-12 21:34) 1.587g/s 18025Kp/s 18025Kc/s 18025KC/s Blondehair10..Blizzard56
Use the "--show --format=NT" options to display all of the cracked passwords reliably
Session completed.
We cracked the password of user1 using john.
But, not able to crack the passwords of user2 using NT hash [rockyou.txt used].
SMB Decryption
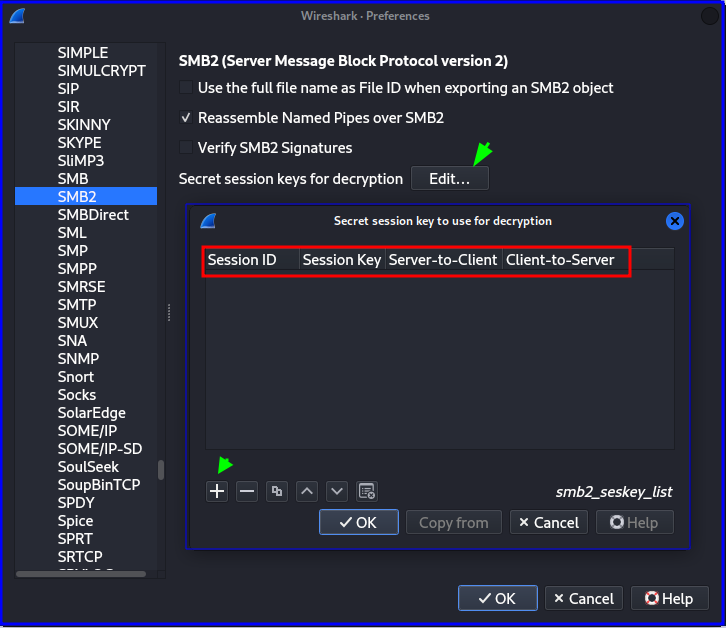
Edit > Preference > Protocols > SMB2
Generating random Session key
Got an interestion page Decrypting SMB3 Traffic with just a PCAP
, and Wiki’s Wireshartk
, Samba
, where we will get idea about the SMB2 Encryption/Decryption process.
We need the following data’s to compute the session key for SMB:
- User’s password or NTLM hash
- User’s domain
- User’s username
- NTProofStr
- Key Exchange Key (Also known as the NTLMv2 Session Base Key)
- Encrypted Session Key
user= “test”
domain= “workgroup”
password = “test”
NTProofStr = a0e42a75c54bbb0fab814593569faa22
EncryptedSessionKey = C914ADCEB0F1C32FB7C2548D8D959F01
hash = MD4(password.encode(‘utf16-le’))
# hash is 0cb6948805f797bf2a82807973b89537ResponseKeyNT(HMAC_MD5(hash, (user.toUpper()+domain.toUpper()).encode(‘utf16-le’)))
# ResponseKeyNT is f31eb9f73fc9d5405f9ae516fb068315 KeyExchangeKey=HMAC_MD5(ResponseKeyNT, NTProofStr)
# KeyExchangeKey is fd160d4ed7f2cb38f64262d7617f23b3RandomSessionKey = RC4(KeyExchangeKey,EncryptedSessionKey)
# RandomSessionKey is 4462b99bb21423c29dbb4b4a983fde03
We have the pseudocode to compute session key, using this we are going to create a python script.
import hmac
import hashlib
from binascii import unhexlify
from Crypto.Cipher import ARC4
import sys
def get_response_key_nt(nt_hash, user, domain):
user_domain = (user.upper() + domain.upper()).encode('utf-16le')
return hmac.new(nt_hash, user_domain, hashlib.md5).digest()
def get_key_exchange_key(response_key_nt, nt_proof_str):
return hmac.new(response_key_nt, nt_proof_str, hashlib.md5).digest()
def decrypt_session_key(key_exchange_key, encrypted_session_key):
rc4 = ARC4.new(key_exchange_key)
return rc4.decrypt(encrypted_session_key)
def main():
if len(sys.argv) < 5 or len(sys.argv) > 7:
print("Usage for NT hash method: python script.py nt_hash username domain nt_hash_value NTProofStr EncryptedSessionKey")
print("Usage for password method: python script.py password username domain password_value NTProofStr EncryptedSessionKey")
sys.exit(1)
method = sys.argv[1]
user = sys.argv[2]
domain = sys.argv[3]
if method == 'nt_hash':
if len(sys.argv) != 7:
print("Usage: python script.py nt_hash username domain nt_hash_value NTProofStr EncryptedSessionKey")
sys.exit(1)
try:
nt_hash = unhexlify(sys.argv[4])
NTProofStr = unhexlify(sys.argv[5])
EncryptedSessionKey = unhexlify(sys.argv[6])
except Exception as e:
print(f"Error parsing hex values: {e}")
sys.exit(1)
response_key_nt = get_response_key_nt(nt_hash, user, domain)
print(f"ResponseKeyNT: {response_key_nt.hex()}")
key_exchange_key = get_key_exchange_key(response_key_nt, NTProofStr)
print(f"KeyExchangeKey: {key_exchange_key.hex()}")
random_session_key = decrypt_session_key(key_exchange_key, EncryptedSessionKey)
print(f"RandomSessionKey: {random_session_key.hex()}")
elif method == 'password':
if len(sys.argv) != 7:
print("Usage: python script.py password username domain password_value NTProofStr EncryptedSessionKey")
sys.exit(1)
password = sys.argv[4]
try:
NTProofStr = unhexlify(sys.argv[5])
EncryptedSessionKey = unhexlify(sys.argv[6])
except Exception as e:
print(f"Error parsing hex values: {e}")
sys.exit(1)
# Step 1: MD4 hash of the password
try:
md4_hash = hashlib.new('md4', password.encode('utf-16le')).digest()
except Exception as e:
print(f"Error hashing password: {e}")
sys.exit(1)
print(f"MD4 Hash of Password: {md4_hash.hex()}")
# Step 2: Calculate ResponseKeyNT using HMAC-MD5
response_key_nt = get_response_key_nt(md4_hash, user, domain)
print(f"ResponseKeyNT: {response_key_nt.hex()}")
# Step 3: Calculate KeyExchangeKey using HMAC-MD5
key_exchange_key = get_key_exchange_key(response_key_nt, NTProofStr)
print(f"KeyExchangeKey: {key_exchange_key.hex()}")
# Step 4: Decrypt EncryptedSessionKey using RC4
random_session_key = decrypt_session_key(key_exchange_key, EncryptedSessionKey)
print(f"RandomSessionKey: {random_session_key.hex()}")
else:
print("Invalid method. Use 'nt_hash' or 'password'.")
if __name__ == "__main__":
main()
Lets save this as file sessionKey.py.
Lets gather the required data:
- username =
mrealman(from pcap) - domain =
WORKGROUP(from pcap) - password =
Blockbuster1(Decrypted from NT hash which we got in lsass.dmp) - NTProofStr =
16e816dead16d4ca7d5d6dee4a015c14(from pcap) - EncryptedSessionKey =
fde53b54cb676b9bbf0fb1fbef384698(from pcap) We have all required data, lets run the python script.
$ python sessionKey.py mrealman WORKGROUP Blockbuster1 16e816dead16d4ca7d5d6dee4a015c14 fde53b54cb676b9bbf0fb1fbef384698
MD4 Hash of Password: 1f9175a516211660c7a8143b0f36ab44
ResponseKeyNT: 110fd571fec8b2d44728e3d4d6f32f0a
KeyExchangeKey: 17e09b2c9b92045329a4382898f50159
RandomSessionKey: 20a642c086ef74eee26277bf1d0cff8c
We got the results.
We also have session id 0x0000100000000041 (from pcap).
But, SMB2 data is not decrypted when using this session id and key combination, problem with session id.
Endian
import sys
# Get session ID from command line argument (as a hex string)
session_id_str = sys.argv[1]
# Convert hex string to an integer
session_id = int(session_id_str, 16)
# Ensure it's padded to 8 bytes
num_bytes = 8
# Convert the integer to bytes (big-endian), padding it to 8 bytes
original_bytes = session_id.to_bytes(num_bytes, byteorder='big')
print(f"Original Bytes (big-endian): {original_bytes.hex()}")
# Reverse the bytes
reversed_bytes = original_bytes[::-1]
print(f"Reversed Bytes: {reversed_bytes.hex()}")
# Convert back to integer from reversed bytes (little-endian)
reversed_session_id = int.from_bytes(reversed_bytes, byteorder='big')
# Print original and reversed hex values, ensuring it's always 8 bytes (16 hex digits)
print(f"Original: 0x{session_id:016x}") # Pad original with zeros to ensure 16 hex digits (8 bytes)
print(f"Reversed: 0x{reversed_session_id:016x}") # Ensure reversed is also 8 bytes in the output
Used this script to reverse the endian .
The reversed session id of 0x0000100000000041 is 4100000000100000.
By using this reversed session id we are sucessfully able to decrypt the smb traffic.
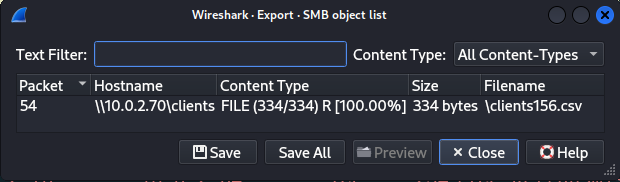
clients156.csv in Export:SMB objects.Lets export that file.
$ cat clients156.csv
first_name,last_name,password
Jewell,Caseri,eS8/y*t?8$
Abey,Sigward,yB0{g_>KezO
Natassia,Freeth,tS2<1Fef9tiF
Verina,Wainscoat,kT8/2uEMH
Filia,Sommerling,oE9.2c?Sce
Farris,Busst,THM{REDACTED}
Bat,Oakes,gE0%f@'qw}s%
Verina,Jedrachowicz,wK4~4L\O
Caril,Wolfarth,yQ3$Ji0~f7aB>F{
Bordie,Baume,iM1}"x)yP'`2|S
,,
Got flag 3 here.
Lets try to decrypt the smb traffic of 2nd user. Lets gather the required data:
- username =
eshellstrop(from pcap) - domain =
WORKGROUP(from pcap) - password/NT hash =
3f29138a04aadc19214e9c04028bf381(Decrypted from NT hash which we got in lsass.dmp) - NTProofStr =
0ca6227a4f00b9654a48908c4801a0ac(from pcap) - EncryptedSessionKey =
c24f5102a22d286336aac2dfa4dc2e04(from pcap)
$ python new.py nt_hash eshellstrop WORKGROUP 3f29138a04aadc19214e9c04028bf381 0ca6227a4f00b9654a48908c4801a0ac c24f5102a22d286336aac2dfa4dc2e04
ResponseKeyNT: f48087e449d58b400e283a27914209b9
KeyExchangeKey: 9754d7acae384644b196c05cda5315df
RandomSessionKey: facfbdf010d00aa2574c7c41201099e8
And the reversed session id of 0x0000100000000045 is 4500000000100000.
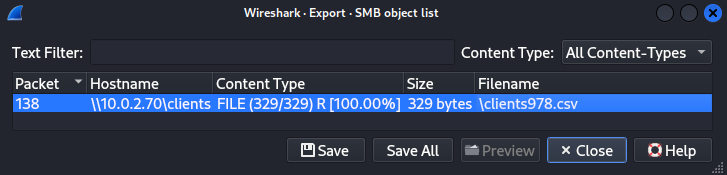
clients978.csv in Export:SMB objects.Lets export that file.
$ cat clients978.csv
first_name,last_name,password
Fran,McCane,vP5{|r$IYDDu
Fredrika,Delea,qU2!&Bev
Josefa,Keir,hX0)gq54I"%d
Joannes,Greatham,vS1)N,z1X1rc
Courtenay,Keble,lV6|0aiSZL@@`bbM
Tonye,Risebrow,THM{REDACTED}
Joleen,Balog,tK9'ZapdU.'igGs
Clementia,Kilsby,uC6!Bx}`Xe
Mason,Woolvett,eL0$NO)FRY1IT
Rozele,Izachik,wA8>11$,'0,b+
,,
We got final flag here.
Alternatives
Using mimikatz
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # sekurlsa::minidump Z:\evidence\lsass.DMP
Switch to MINIDUMP : 'Z:\evidence\lsass.DMP'
mimikatz # sekurlsa::logonPasswords full
Opening : 'Z:\evidence\lsass.DMP' file for minidump...
Authentication Id : 0 ; 1883004 (00000000:001cbb7c)
Session : Interactive from 3
User Name : mrealman
Domain : BLOCK
Logon Server : WIN-2258HHCBNQR
Logon Time : 22-10-2023 09:53:54
SID : S-1-5-21-3761843758-2185005375-3584081457-1104
msv :
[00000003] Primary
* Username : mrealman
* Domain : BLOCK
* NTLM : 1f9175a516211660c7a8143b0f36ab44
* SHA1 : ccd27b4bf489ffda2251897ef86fdb488f248aef
* DPAPI : 3d618a1fffd6c879cd0b056910ec0c31
tspkg :
wdigest :
* Username : mrealman
* Domain : BLOCK
* Password : (null)
kerberos :
* Username : mrealman
* Domain : BLOCK.THM
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 828825 (00000000:000ca599)
Session : Interactive from 2
User Name : eshellstrop
Domain : BLOCK
Logon Server : WIN-2258HHCBNQR
Logon Time : 22-10-2023 09:46:09
SID : S-1-5-21-3761843758-2185005375-3584081457-1103
msv :
[00000003] Primary
* Username : eshellstrop
* Domain : BLOCK
* NTLM : 3f29138a04aadc19214e9c04028bf381
* SHA1 : 91374e6e58d7b523376e3b1eb04ae5440e678717
* DPAPI : 87c8e56bc4714d4c5659f254771559a8
tspkg :
wdigest :
* Username : eshellstrop
* Domain : BLOCK
* Password : (null)
kerberos :
* Username : eshellstrop
* Domain : BLOCK.THM
* Password : (null)
ssp :
credman :
mimikatz #
Here we have used miikatz to extract data from DMP file.
We solved the lab.
Happy Hacking !!! 😎