Introduction
Detailed walkthroughs for CERTain Doom
CTF challenges on TryHackMe
.
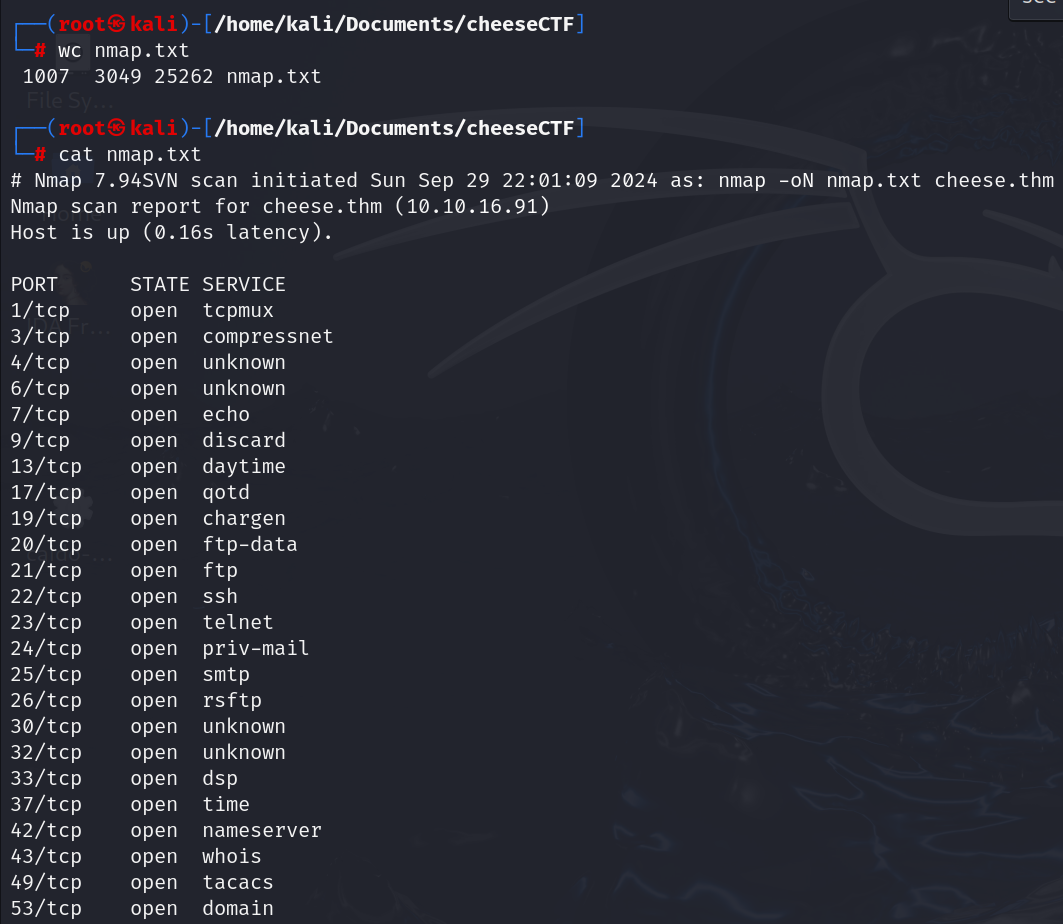
$ echo "10.10.81.254 certain-doom.thm" >> /etc/hosts
Mappped the ip to domain certain-doom.thm.
Questions
1. What is the web flag? Hint:Today's lucky number is 11
2. What is the user's flag?
3. What is the super secret flag? Hint: supersonic subatomic
Rustscan
$ rustscan -a certain-doom.thm -- -sV -sC
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
[~] The config file is expected to be at "/root/.rustscan.toml"
Open 10.10.81.254:22
Open 10.10.81.254:80
Open 10.10.81.254:8080
[~] Starting Script(s)
Scanned at 2024-09-14 08:29:53 IST for 157s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:69:84:5c:69:01:42:2d:da:01:3e:13:a6:db:2f:c3 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDI9RmMphpZ0uukrNxPj8ojeRdQF3nTPgufa6bqShoWI9Sfs78koCvg+oYL2dz+o+JU34j7kbNnzqrlkvG2piLgjGa/nzZbUVpiAk85TGSrltb2H9p6ORqTXmgnFNitwynoz8tI0XqIBxuQm801hEYBOYFdEqRp8pPLkbDI8gDUJCtk8Ta+v189AXvIBragn4jPcXS7wbX61csUr7jGjneln9hybY4GC/cmHMIF2sYCzHbDuwl7bC4QVf8Qd1DNknR0f7pPGillIa76d4c+10pF83kv4QjZf3WRdytNo6psqg9VH2Kz6AWpPn9z6aWTanONQzl3HdP8mzBzsUA76ZPh/IgNQDrCJTmM9SX4z2n60+aqlPo6PjvM8XxSu/XvPsvzpL+CABmz+k2ziCmd+nQ0tJrpIwUFTpb/82ZbGSDtFNNm35vsL++R5yHodU0jvb0Yq8blpUu4vh7Pzuiryk2H7HgjYcj1FmPwGvv+HpdY+uPQwuIA9xe2bnxZ8BW7LKE=
| 256 cc:55:d5:72:1d:be:03:85:d5:7e:3e:1a:d6:72:2c:2c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLig4AYdXAxFRwdUHHUtXGkdr3GFGGM83WssnCjyrU1deeFT1BDuit5NI+7nEqVl0BeSSU3LRpHeLpSIYiugxC0=
| 256 08:34:3b:e0:5d:d1:37:d4:68:28:6b:cf:e2:f1:53:ed (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINFfDent94JxaXvMValeP9zIhJO8/mj/WFtHqGkUsv4X
80/tcp open http syn-ack ttl 59 hastatic-1.0.0
|_http-server-header: hastatic-1.0.0
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Content-Length: 117674
| Accept-Ranges: bytes
| Date: Sat, 14 Sep 2024 03:00:00 GMT
| Server: hastatic-1.0.0
| Content-Type: text/html
| Cache-Control: no-transform,public,max-age=300,s-maxage=900
| Last-Modified: Thu, 26-Jan-2023 22:44:29 UTC
| ETag: 98eb1c6fb079742e0b8682cb642c5c777329ebbe
| Vary: Accept-Encoding
| Referrer-Policy: strict-origin-when-cross-origin
| X-Frame-Options: SAMEORIGIN
| X-XSS-Protection: 1; mode=block
| <!doctype html>
| <html class="no-js" lang="">
| <head>
| <meta charset="utf-8">
| <title>Super Secret Admin Page</title>
| <meta name="description" content="">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta property="og:title" content="Hydra's Super Secret Admin Page">
| <meta property="og:type" content="website">
| <meta property="og:url" content="https://admin.certain-doom.thm">
|_ <meta property="og:image" content="">
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Super Secret Admin Page
|_http-favicon: Unknown favicon MD5: 338ABBB5EA8D80B9869555ECA253D49D
8080/tcp open http-proxy syn-ack ttl 59 Apache Tomcat 9?
|_http-title: HTTP Status 404 \xE2\x80\x93 Not Found
|_http-server-header: Apache Tomcat 9?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 404
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 431
| Date: Sat, 14 Sep 2024 03:00:00 GMT
| Connection: close
| Server: Apache Tomcat 9?
| <!doctype html><html lang="en"><head><title>HTTP Status 404
| Found</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 404
| Found</h1></body></html>
| RTSPRequest:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Sat, 14 Sep 2024 03:00:00 GMT
| Connection: close
| Server: Apache Tomcat 9?
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 158.30 seconds
Raw packets sent: 7 (284B) | Rcvd: 4 (172B)
We got 3 active ports: 22, 80 and 8080.